Choosing Between Host and Network Intrusion Detection System
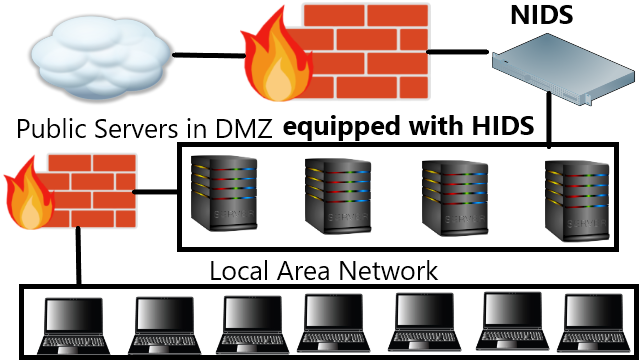
Regarding to the deployment of IDS on the public cloud there are two cases. The first one is when we own the cloud the other one is if we borrow someone else’s cloud. As for the first there are two types of network, one is the internal network and the other one is public network where those from the Internet can normally access the network. The structure of the network depends on the administrators but usually the internal and outside network are separated by demilitarized zone (DMZ). The public servers (where users from thy e Internet access) should be equipped with tight security. The most common one is the firewall on the end of the public network and antivirus on each servers. To complete the security intrusion detection system (IDS) or intrusion prevention system (IPS) should be equipped. But which type of IDS should be placed? Host based or network based, signature based or anomaly based? A hybrid of signature and anomaly based is best for my opinion but whether using a host base IDS (HIDS) or network base IDS (NIDS) is something to think hard off, and this greatly depends on the network architecture and the urgency of the situation. This is the seventh assignment from my Masters Advanced Network Security Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here.
Using the HIDS is very affective because (1) can protect important servers (2) can monitor encrypted communications (3) distributed resource used. Even though all servers are part of the network but amongst them they have different scale of importance. A server that offers services as online shopping, e-learning, community are most likely to be attacked because not only contains important informations, it’s very popular. For this case (1) is the reason we should deploy HIDS. Sometimes even NIDS needs to be equipped with HIDS because attacks could directly aim for NIDS. For (2) case it’s convenient because HIDS is not affected by encryptions because the encrypted packet is alway decrypted on the end of the server. NIDS on the other hand must cope with encrypted communications. For (3) each hosts uses IDS so the resource consumed is distributed, it only processes the packets received. On the other hand for NIDS must handle all network traffics.
Sometimes we cannot use HIDS for certain reasons such as (1) using special operating system (OS) where no HIDS is available for that OS, and (2) restriction to changes on host (for certain reasons) or as much as possible want to avoid changes. Another reason is afraid if some sort of accident might occur for example forgot to boot HIDS when restarting a server. Then NIDS should be use here especially if one is curious in monitoring the whole network. Placing an NIDS on a layer 1 network will be no problem since all packets flows to all ports. If using layer 2 or higher where communications is private NIDS must be place on mirror port (copies other ports communication to this one).
The best security choice is to use both HIDS and NIDS but resource became a problem. Install HIDS on all service greatly affects the network’s performance, an NIDS tends to disfunction at very high traffic. This resource issue became very sensitive on the second type of public cloud where we buy a cloud service which is maintained by another party (cloud providers) such as Amazon, Google, Cloud9, etc. Information from most customers that they don’t have control over the physical hardware, which some argues that using IDS is useless because we don’t have access to inbound and outbound traffic. Today’s research regarding to this issue introduces the virtual machine based IDS (VM-IDS). One example of the VM-IDS install an IDS on the public cloud and the web and database servers on the VM. The users on the Internet must go through the IDS regardless because the servers resides on the VM.
Mirrors
- https://www.publish0x.com/fajar-purnama-academics/choosing-between-host-and-network-intrusion-detection-system-xykwvvw?a=4oeEw0Yb0B&tid=github
- https://0darkking0.blogspot.com/2021/02/choosing-between-host-and-network.html
- https://0fajarpurnama0.medium.com/choosing-between-host-and-network-intrusion-detection-system-24342279b9d
- https://0fajarpurnama0.github.io/masters/2020/07/12/choosing-between-host-and-network-intrusion-detection-system
- https://hicc.cs.kumamoto-u.ac.jp/~fajar/masters/choosing-between-host-and-network-intrusion-detection-system
- https://steemit.com/technology/@fajar.purnama/choosing-between-host-and-network-intrusion-detection-system?r=fajar.purnama
- https://stemgeeks.net/technology/@fajar.purnama/choosing-between-host-and-network-intrusion-detection-system?ref=fajar.purnama
- https://blurtter.com/blurtech/@fajar.purnama/choosing-between-host-and-network-intrusion-detection-system?referral=fajar.purnama
- https://0fajarpurnama0.wixsite.com/0fajarpurnama0/post/choosing-between-host-and-network-intrusion-detection-system
- http://0fajarpurnama0.weebly.com/blog/choosing-between-host-and-network-intrusion-detection-system
- https://0fajarpurnama0.cloudaccess.host/index.php/9-fajar-purnama-academics/197-choosing-between-host-and-network-intrusion-detection-system
- https://read.cash/@FajarPurnama/choosing-between-host-and-network-intrusion-detection-system-9e64e4b6
- https://www.uptrennd.com/post-detail/choosing-between-host-and-network-intrusion-detection-system~ODU5MTU3