My Comments on Network and Bots and Pentest when I was a young student
This is the first assignment from my Masters Advanced Network Security Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here. Since it is the first meeting, this only my comments about the first lecture but hopefully you get the picture about it.
1. Network Consists of Clients and Servers
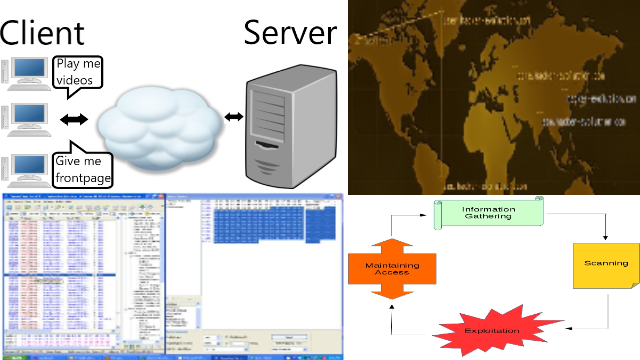
About network servers I capture that the network consist of clients and servers. The clients requests informations and servers gives the information. I have tried using some server which includes web server, file server, mail server, dns server, and dhcp server but I’m still new especially on the security aspects of this servers.
2. There Are Many Bots on The Network
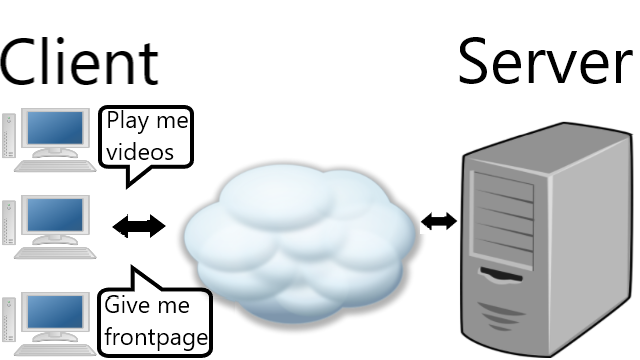
I have heard bot network before, I played a game called hacker evolution that gives a picture of bots but I never tried them before. If I were on the hacker side I will hijack into other clients PC using malware. That malware will inform back to me and I can use the hijacked clients to do something for me for example sending spam mails, or make new bot (find other victims). Usually as an amateur I would directly hack to the targeted server, but with this method is more effective because instead of using my own PC, I can use other PCs as well. I wonder if I can practice this in virtual machine. By the way some links on the buttom of the page are dead.
3. Popular Hacking Methods
DDOS or Denial of Service is very famous in hacking event among newcomers, which is to disable the service of a server. I have only practice this by flooding the traffic of a Wifi, the other I tried is on a server on client using many computer. The way I tried is very suitable using statement in number 2 using bots. By having many PC increases the computing power. About web defacement I have seen some sites have their contents hacked, either by modifying the contents or inserting new contents. Today there are many free tools available to scan for vulnerability, Nessus for example, and tools to exploit those vulnerability like Metasploit Framework. I’m only user of this tools so I still don’t know the concept behind it. There also exist simple vulnerabilities due to misconfiguration for example MySQL injection that allows to use MySQL commands on login to bypass, or another one which I can modify the html page which allows to enter without password.
4. My Prior Knowledge About Penetration Testing
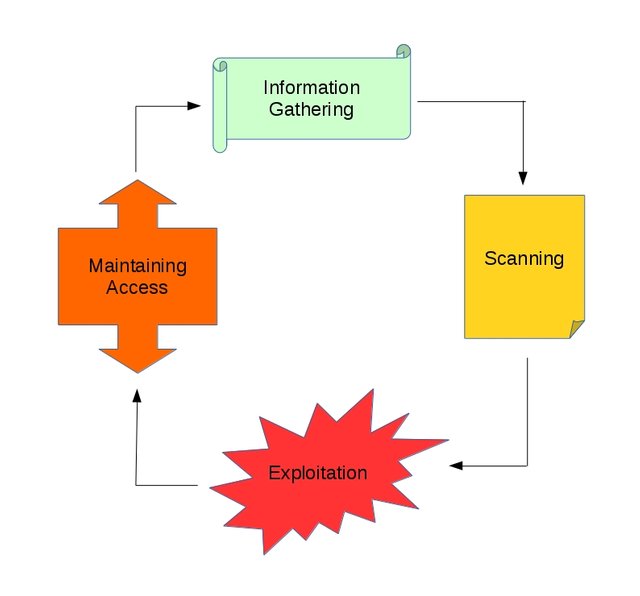
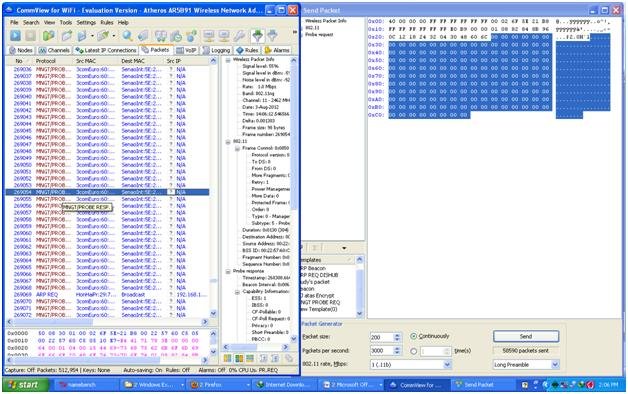
In the past of learning network security the first thing I was asked to remember the OSI layers which consists of physical, datalink, network, transport, session, presentation, and application. Buffer overflow is very famous but the concept behind it for me is more tricky that others. I have read a book called The Basics of Hacking and Penetration Testing. The contents told me that there is a difference between hacker (black hat) for ill purposes and penetration tester (white hat) to find security holes in order to cover them. I on the other hand am a grey hat (only serve as a hobby and mere curiosity, and only finds satisfaction if able to hack a system and won’t go further than that). Main the contents consist of 4 important steps of hacking which is highly recommend to follow in order. First and the most important part is information gathering which affect the outcomes of the other processes. Second is scanning, while information gathering gathers informations about the target, scanning scan this information like port scanning on certain found IP from information gathering. Then the third, the main step becomes affective which is exploitation. Finally the fourth is maintaining access for permanent access.
Mirrors
- https://www.publish0x.com/fajar-purnama-academics/my-comments-on-network-and-bots-and-pentest-when-i-was-a-you-xryxxqp?a=4oeEw0Yb0B&tid=github
- https://0darkking0.blogspot.com/2021/01/my-comments-on-network-and-bots-and.html
- https://0fajarpurnama0.medium.com/my-comments-on-network-and-bots-and-pentest-when-i-was-a-young-student-d74c7aed8c6f
- https://0fajarpurnama0.github.io/masters/2020/07/06/comment-network-bot-pentest
- https://hicc.cs.kumamoto-u.ac.jp/~fajar/masters/comment-network-bot-pentest
- https://steemit.com/technology/@fajar.purnama/my-comments-on-network-and-bots-and-pentest-when-i-was-a-young-student?r=fajar.purnama
- https://stemgeeks.net/technology/@fajar.purnama/my-comments-on-network-and-bots-and-pentest-when-i-was-a-young-student?ref=fajar.purnama
- https://blurtter.com/blurtech/@fajar.purnama/my-comments-on-network-and-bots-and-pentest-when-i-was-a-young-student?referral=fajar.purnama
- https://0fajarpurnama0.wixsite.com/0fajarpurnama0/post/my-comments-on-network-and-bots-and-pentest-when-i-was-a-young-student
- http://0fajarpurnama0.weebly.com/blog/my-comments-on-network-and-bots-and-pentest-when-i-was-a-young-student
- https://0fajarpurnama0.cloudaccess.host/index.php/9-fajar-purnama-academics/191-my-comments-on-network-and-bots-and-pentest-when-i-was-a-young-student
- https://read.cash/@FajarPurnama/my-comments-on-network-and-bots-and-pentest-when-i-was-a-young-student-7ec0b40b
- https://www.uptrennd.com/post-detail/my-comments-on-network-and-bots-and-pentest-when-i-was-a-young-student~ODU2MjMw