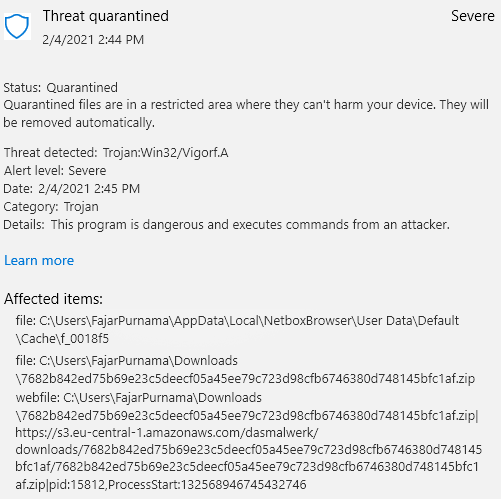
My Comments on Malware Quarantine when I was a young student
Quarantine is a place to isolate an object to prevent the infection of harmful substances. We can see when a person who is suffering from influenza is brought into an isolated place because influenza is known as a virus that could easily spread and infects other people. Not only people, animals and plants also brought into quarantine if it could spread diseases, other stuffs also applies. The word quarantine was originally Italian “quaranta” meaning forty (40). History claims during the 13th century in Europe and Asia there was The Black Death academic that causes over 450 millions death cause by a bacteria back then contained in black rats. Ships with the passengers coming to the mainland waited for 40 days before it can enter to see whether symptoms occurs. Those without the symptoms after 40 days may pass. This is the eighth assignment from my Masters Advanced Network Security Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here.
In computer and information system the quarantine is used to isolate harmful data that could spread and infect other PCs for example worms, virus, and packets containing attack patterns. An example of a quarantine that is common in public is on the anti virus (AV) software. When an (AV) detected a file infected by a computer virus it will put it into quarantine, functionally no users and other programs may access the infected file (isolated).
On a computer network the quarantine server is usually attached on a mirror port of layer 2 switch, or functions as a DHCP server, or both. An IPS can prevent attacks from outside but it cannot manage on the inside when a PC is infected by a worm or virus, and so a quarantine is mostly use to protect from the inside. Even thought there are AV software, but in this situation it is assumed that it’s not perfect (there maybe PC not equipped with AV, out of date AV, etc). The quarantine on the network act as a gate it first scan the PC of vulnerability, updates on the AV, and presence of the virus (depends on the quarantine). The PC will be granted access to the network if for example it has no vulnerability, updated OS, AV, application, etc, and no presence of worms and virus (tries to delete them if detected). On DHCP method it might not give IP address to the client if the condition above is not met, another method it adds to the block list of ACL on switches and routers or not included on the accept list. The quarantine is used to strengthen authentication and traffic control, investigate whether OS, AV, and its applications is up to date, and check for the presence of worms and virus.

To me the network quarantine system is very new. Personally I would prefer a quarantine system that would only delete the worms and virus along the way when communicating on the network. If acts like a strict security guard I will be strictly to always update my applications to the latest before I may use the network which seems very troubling if I have urgent cases. On the other hand this system is a great additional solution to tighten network security, especially in cases in protecting very important data.
Mirrors
- https://www.publish0x.com/fajar-purnama-academics/my-comments-on-malware-quarantine-when-i-was-a-young-student-xmkgmlz?a=4oeEw0Yb0B&tid=github
- https://0darkking0.blogspot.com/2021/02/my-comments-on-malware-quarantine-when.html
- https://0fajarpurnama0.medium.com/my-comments-on-malware-quarantine-when-i-was-a-young-student-881aa474599a
- https://0fajarpurnama0.github.io/masters/2020/07/13/comment-malware-quarantine
- https://hicc.cs.kumamoto-u.ac.jp/~fajar/masters/comment-malware-quarantine
- https://steemit.com/technology/@fajar.purnama/my-comments-on-malware-quarantine-when-i-was-a-young-student?r=fajar.purnama
- https://stemgeeks.net/technology/@fajar.purnama/my-comments-on-malware-quarantine-when-i-was-a-young-student?ref=fajar.purnama
- https://blurtter.com/blurtech/@fajar.purnama/my-comments-on-malware-quarantine-when-i-was-a-young-student?referral=fajar.purnama
- https://0fajarpurnama0.wixsite.com/0fajarpurnama0/post/my-comments-on-malware-quarantine-when-i-was-a-young-student
- http://0fajarpurnama0.weebly.com/blog/my-comments-on-malware-quarantine-when-i-was-a-young-student
- https://0fajarpurnama0.cloudaccess.host/index.php/9-fajar-purnama-academics/198-my-comments-on-malware-quarantine-when-i-was-a-young-student
- https://read.cash/@FajarPurnama/my-comments-on-malware-quarantine-when-i-was-a-young-student-6c917a7c
- https://www.uptrennd.com/post-detail/my-comments-on-malware-quarantine-when-i-was-a-young-student~ODU5NzA0