Masters
Compatible Course Content Synchronization Model for Various LMS over The Network
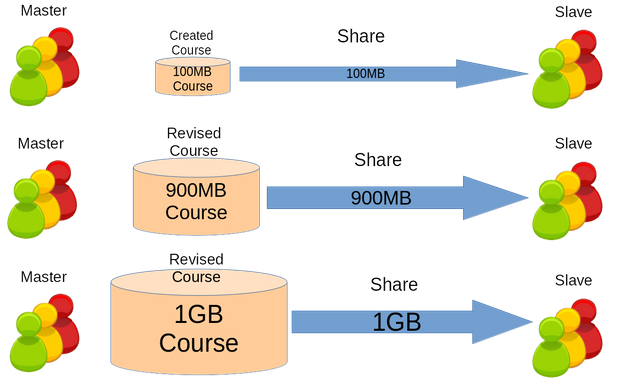
There are connectivity issues in developing countries and is distributed LMS. However, the resource cost keeps on increasing which requires incremental synchronization.
Keywords: elearning online rsync synchronization learning management system
My Summary and Most Interested Topic in Advanced Computer Organization 2 Master's Course

My own summary regarding to the lecture about how computer hardware works and who knows it might give you a description.
Keywords: computer organization interconnection network hardware microprocessor FPGA assignment
7,4 Hamming Codes
First group 4 bits per block, and then obtain the 3 hamming bit codes from the 4 bits for each blocks and add them to make 7 bits per block.
Keywords: math binary chaos piecewise hamming assignment markov random engineering science technology
(4,3)-Single Parity Check of Binary Sequence Skew Tent and PWL Map
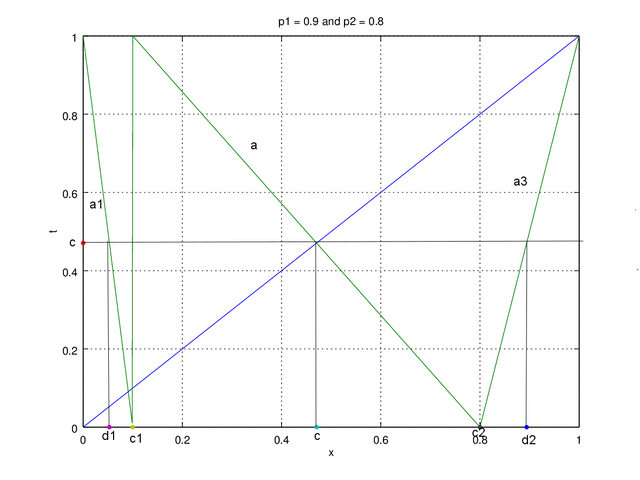
For error probability below 0.2 the Skew Tent Map has lower undetected error and for above that, it is better to use Piece Wise Linear Map.
Keywords: math binary chaos piecewise parity assignment random engineering science technology
Markov Information Binary Sequences Based on Piecewise Linear Chaotic Maps
Uses piecewise linear chaotic binary sequence which is more complex than skew tent map but allows various map design for chaotic sequences.
Keywords: math binary chaos piecewise markov assignment random engineering science technology
Chaotic and Memoryless Binary Sequences Based on Skew Tent Maps
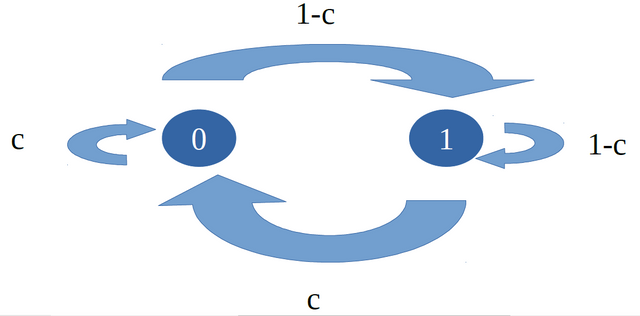
Using the chaotic sequence generated by skew tent map we can generate the random binary sequence with the probability of '0's and '1's.
Keywords: math binary chaos markov assignment random engineering science technology
Chaotic Real-Valued Sequences By Skew Tent Map
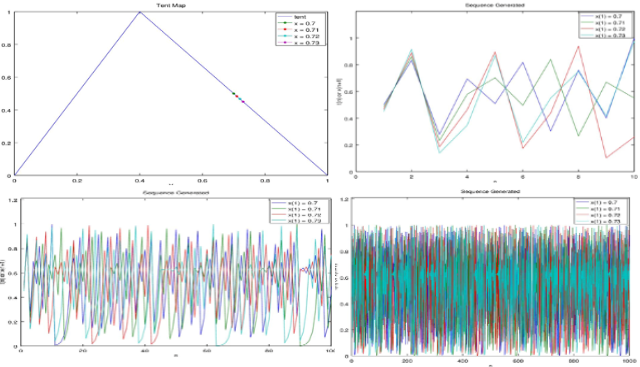
We can predict the weather for a month. Beyond that, we will likely miss predict. In computer it can be applied for creating random values.
Keywords: math engineering chaos random assignment science technology
Portable and Synchronized Distributed Learning Management System in Severe Networked Regions

This is a thesis submitted to Graduate School of Science and Technology, Computer Science and Electrical Engineering in Kumamoto University, Japan, on September 2017 in partial fulfillment of the requirements for the degree of Master of Engineering.
Keywords: technology e-learning portable synchronization distributed system portable masters thesis
Collection of My Mini Assignments in Current Science and Technology in Japan 2016 Course

The assignments that survived are Control System, Xray, Noise Policy, Pulse Power, Binaural Accoustic, and how to return home without honor.
Keywords: technology science engineering Japan assignment
My Assignment in Simple Image Compression Utility Website Evaluation and Other Journal Paper Presentation
The assignments in human perceptions were exciting where we experiment in compressing image, analyzing website, making video presentations.
Keywords: engineering image human perception assignment
My Summary About Origin of Biosignals
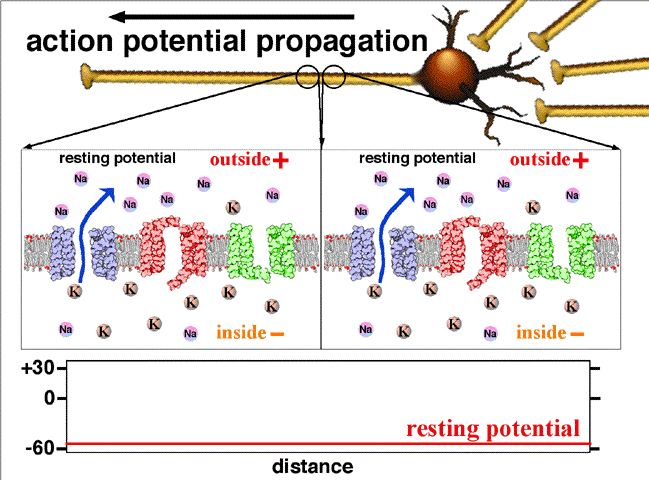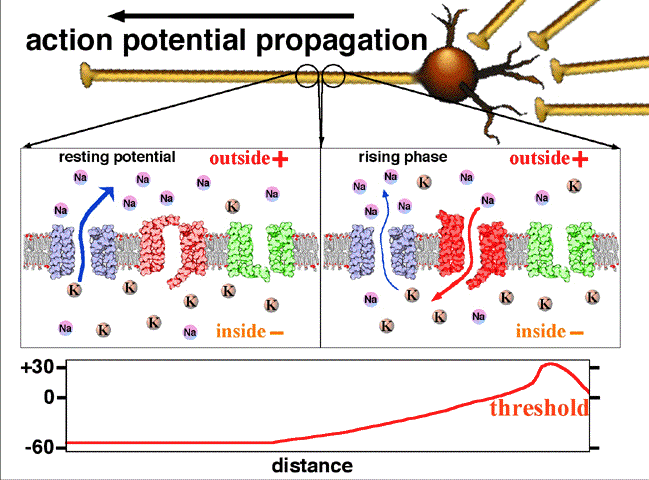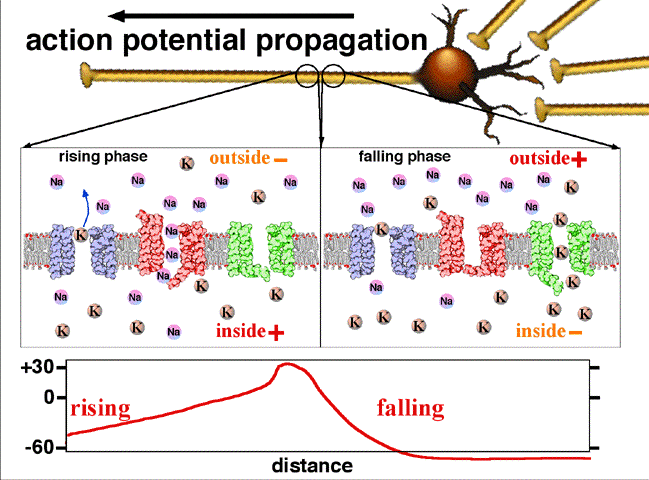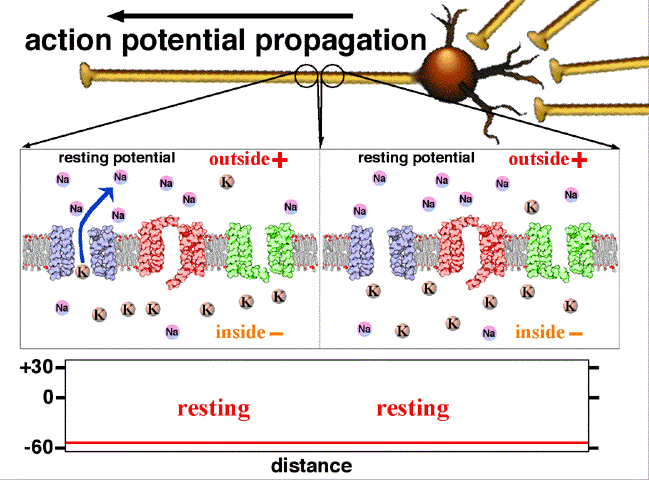
This summary contains the origin of biosignals as deep as how cells generate electricity and how living body can be illustrated as circuit.
Keywords: engineering medical electricity biosignal assignment
My Summary in Advanced Telecommunication Engineering Course
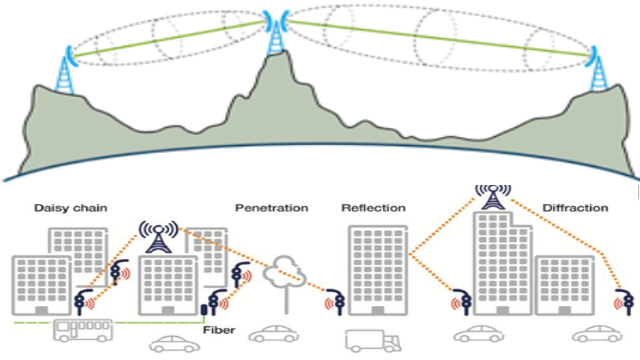
This summary contains materials about wireless communication, Maxwell equation, line of sight and nlos, circular polarization, and antennas.
Keywords: telecommunication line of sight circular polarization antenna assignment
The Stereo 3D on Future Drones
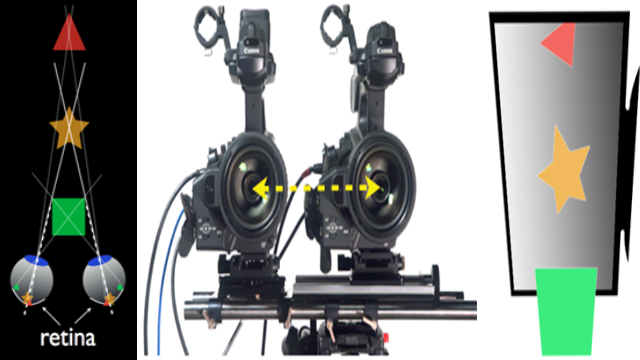
When using a drone we simply have to apply a control system so the drone will capture 2 image separately that fulfills the 3D requirements.
Keywords: technology computers drone perception 3D assignment
My opinion on affective media and wearables paper when I was a young student
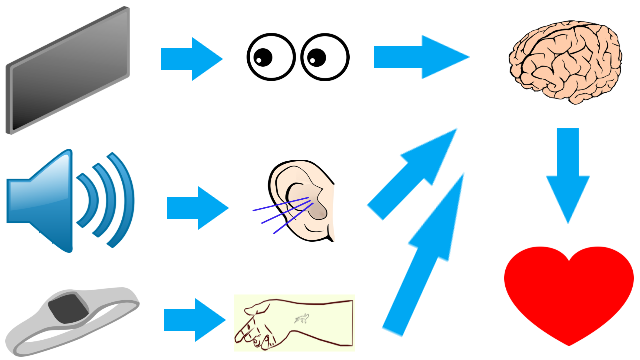
With the advance in technology we can use electronic devices to communicate with others in long distances but can it detect emotions?
Keywords: technology computers information perception emotion assignment
My Opinion on Digital Forensic Steps when I was a Young Student

The four steps of digital forensic are confiscating and isolating storage drive, cloning data, analyzing data, and writing a detail report.
Keywords: technology computers digital forensic assignment
My Opinion of XSS/CSS, Digital Forensic, and Digital Crime Investigation when I was a Young Student
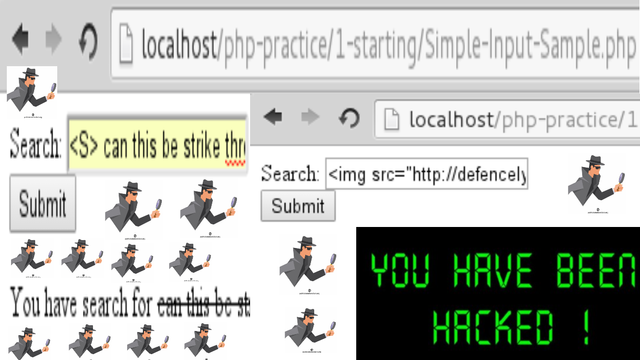
My Opinion of XSS/CSS, Digital Forensic, and Digital Crime Investigation when I was a Young Student
Keywords: technology computers XSSCSS digital forensic assignment
My Opinion of How Edward Snowden Breached the NSA when I was a Young Student
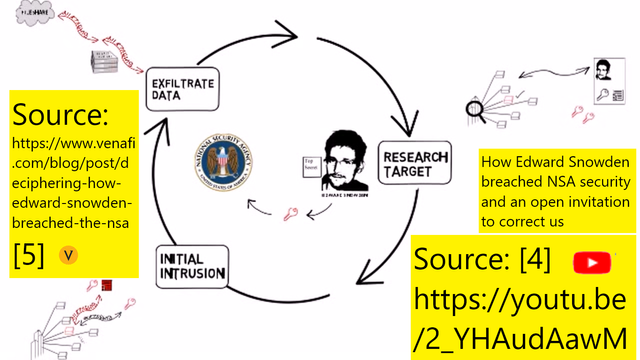
There are mainly 3 steps of breaching NSA using kill chain analysis which are researching the target, initial intrusion, and exfiltration.
Keywords: technology computers Edward Snowden NSA breach assignment
My Simple C Program Demonstrating Heap Buffer Overflow
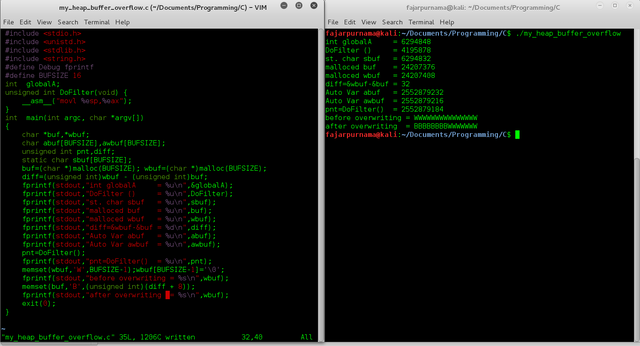
The statically assigned variables or local variables resides in the stack area and dynamically assigned variables resides in the heap area.
Keywords: technology computers buffer overflow heap C Program assignment
My Simple C Program Demonstrating Buffer Overflow
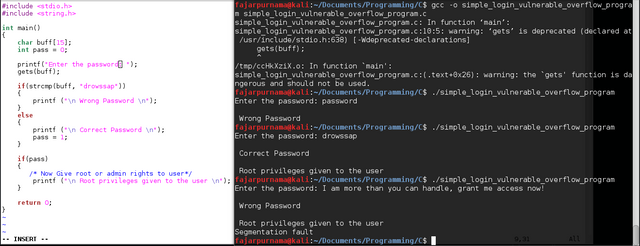
Buffer overflow overwrites other part of the memory. The simplest case is variable B if put too much data can flood to the next variable A.
Keywords: technology computers buffer overflow C Program assignment
My Examples on Reverse Engineering in Computers when I was a young student
Reverse engineering was originally applied only to hardware, reverse-engineering is now applied to software, databases and even human DNA.
Keywords: technology computers reverse engineering decompile assignment
My Comments on Malware and Spams in Email when I was a young student
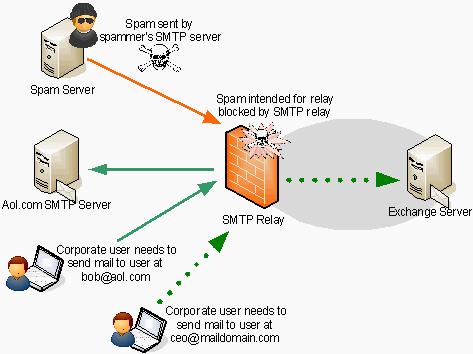
Use email anti virus (AV), outbound port 25 blocking & authentication, sender policy framework, domain key identified mail, identification.
Keywords: technology computers malware email spam assignment
My Comments on Malware Quarantine when I was a young student
In computer and information system the quarantine is used to isolate harmful data that could spread and infect other PC for example malware.
Keywords: technology computers malware quarantine assignment
Choosing Between Host and Network Intrusion Detection System
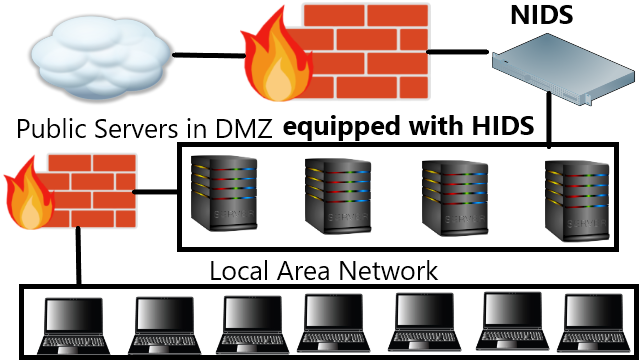
Which type of intrusion detection system should be placed? The best security choice is use both HIDS and NIDS but the problem is resource.
Keywords: technology computers intrusion detection system HIDS NIDS assignment
Intrusion Detection System Important Specifications
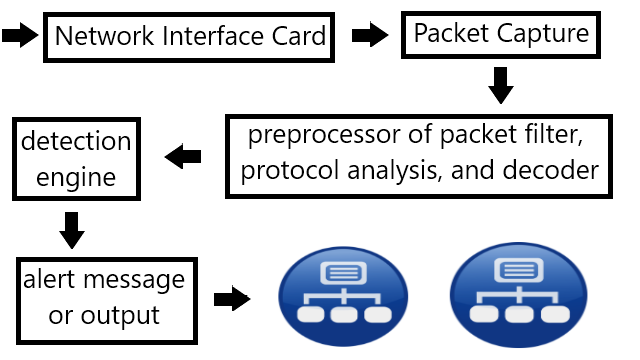
The important specifications are coverage, detection capability, processing power, false negative, and false positive, though there are more
Keywords: technology computers intrusion detection system specification assignment
Having Intrusion Detection System Despite Having Anti Virus and Firewall
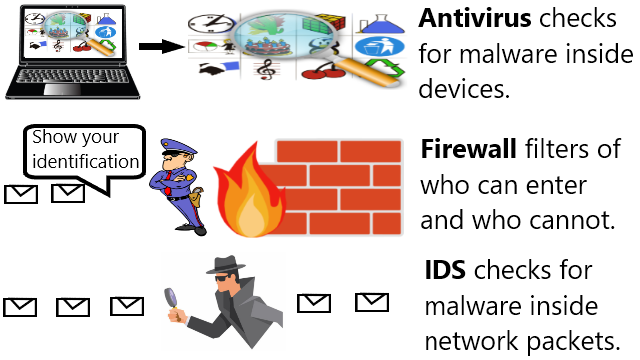
Antivirus handles malware inside devices, firewall filters packet based on identity, and intrusion detection system find malware in packets.
Keywords: technology computers antivirus firewall intrusion detection system assignment malware
Malware Counter Measure Standard Operation Procedure in Old Corporations

The counter measures are quarantining infected devices, plugging to an external malware cleaner, scan for infections, and delete infections.
Keywords: technology computers malware counter measure assignment
My Comments on Information Security Policy when I was a young student
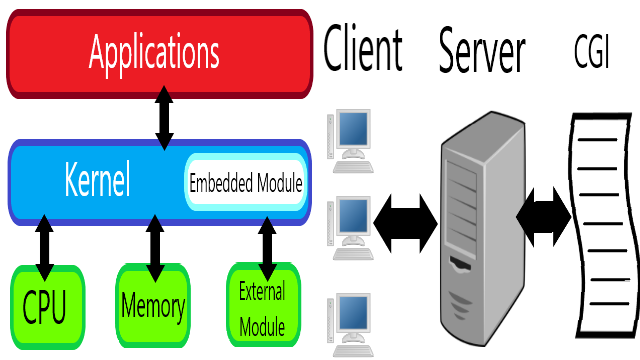
The lecture explained the policies when facing vulnerabilities in the kernel, server program, and server common gateway interface (CGI).
Keywords: technology information security policy assignment
Dealing with Malware for Ordinary Users
The countermeasures of Malicious Ware are mitigation, evasion, and treatment like any other measures to cope against harmful substances.
Keywords: technology computers antivirus malware assignment
My Comments on Network and Bots and Pentest when I was a young student
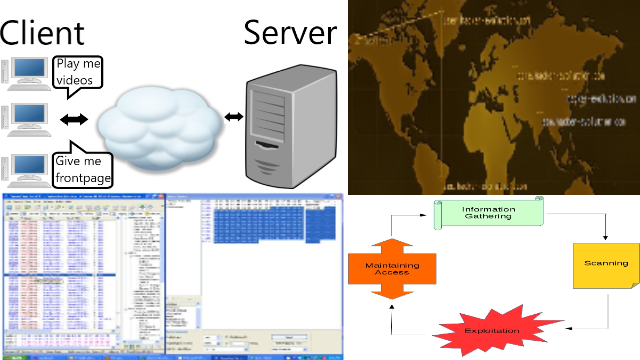
Network consists of clients and servers, there are many bots, and ddos and web defacements and sql injections are popular hacking methods.
Keywords: technology computer network bot penetration testing assignment hacking
Hand Carry Data Collecting Through Questionnaire and Quiz Alike Using Mini-computer Raspberry Pi
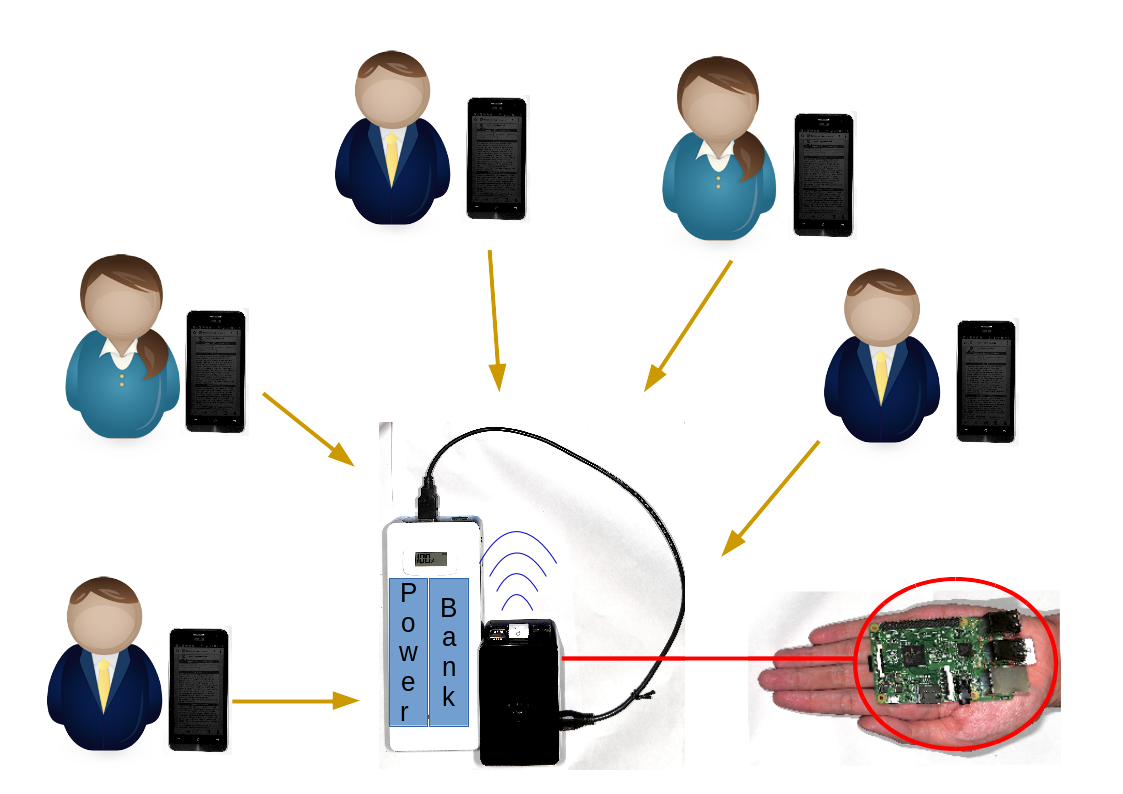
Our method involves in providing a portable hotspot device for correspondent to connect and access our local survey questionnaire website.
Keywords: single board computer hand carry server raspberry pi portable survey
Rsync and Rdiff Implementation on Moodle's Backup and Restore Feature for Course Synchronization over The Network

This paper proposed the synchronization of the existing backup and restore features. The file synchronization is performed between course's backup files based on rsync algorithm.
Keywords: rsync rdiff moodle network synchronization
Demonstration on Extending The Pageview Feature to Page Section Based Towards Identifying Reading Patterns of Users
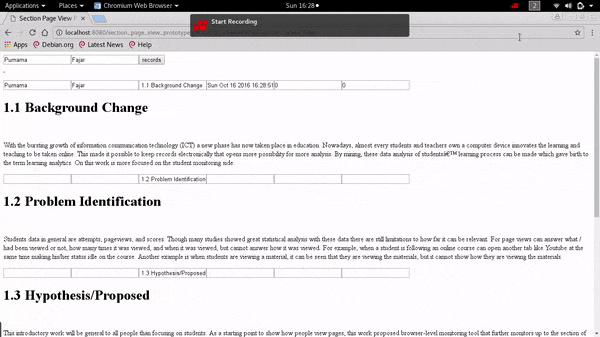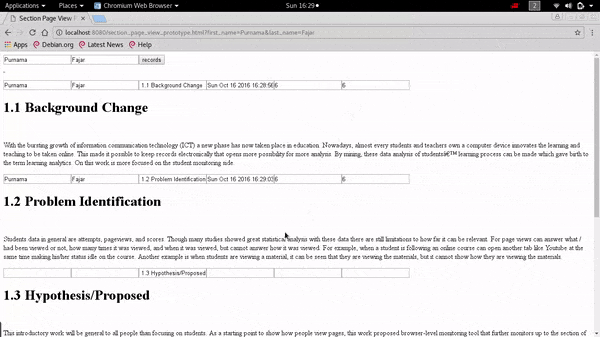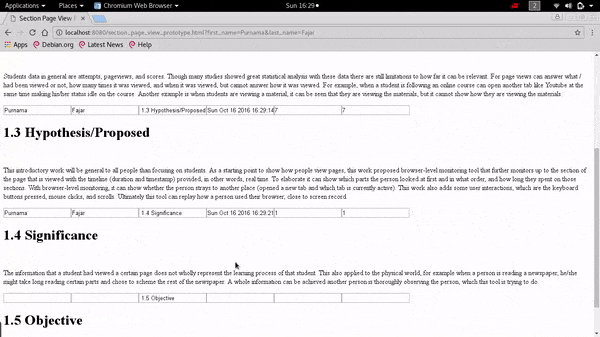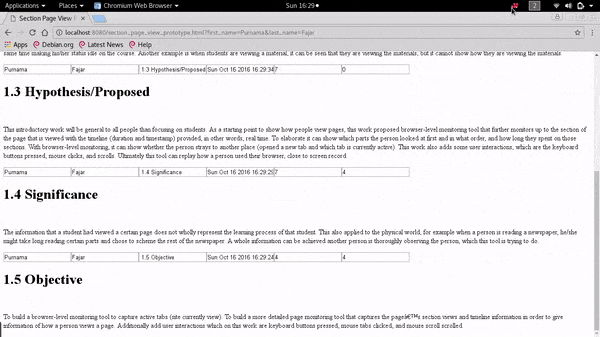
The web application can show the date accessed to a particular section and the duration spent on that section by the user. It can also provide data that shows the reading pattern of a reader which in the future can be used for analysis by other researchers.
Keywords: technology mouse tracking section based page view web analytic monitoring online
Introductory Work on Section Based Page View of Web Contents Towards The Idea of How a Page is Viewed
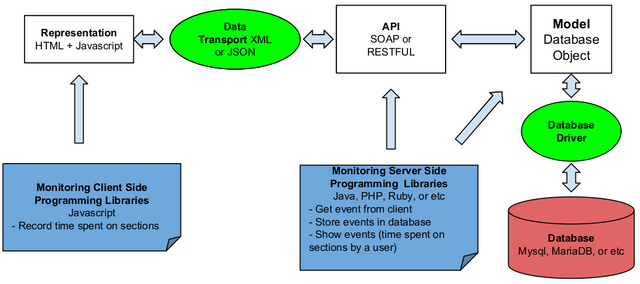
The data can answer what, when, and where, but cannot answer how a page is viewed. To answer that question it is needed to track as detail as the page section level.
Keywords: technology mouse tracking section based page view web analytic monitoring online
Publications
Keywords: masters school university research publication journal conference technical paper article manuscript slide