Cinema Mode
Settings & Custom List
Opacity: 1.0
Z-Index:
Music Player
Name: -
Album: -
Reference: -
Status: Not Ready
Advanced / Upload Custom JSON
Ready State:
Network State:
Background Colors
General HTML:
Header:
Menu:
Content Card:
Sidebar Widget:
Footer:
Font Sizes
Heading 1:
Heading 2:
Heading 3:
Heading 4:
Heading 5:
Heading 6:
Header:
Header Widget:
Menu:
Sidebar:
Footer:
Content:
Font Colors
Heading 1:
Heading 2:
Heading 3:
Heading 4:
Heading 5:
Heading 6:
Header:
Header Icons:
Menu:
Sidebar:
Footer:
Content:
Font Shadows
Heading 1:
Heading 2:
Heading 3:
Heading 4:
Heading 5:
Heading 6:
Header:
Header Icons:
Menu:
Sidebar:
Footer:
Content:
More styles coming soon...
Connect Wallet
Click the above image for basic sourced and click following button for processing token source code.
Ethereum and EVM (ETC, BSC, AVAX-C-Chain, Polygon, etc).
Telegram Open Network (TON) decentralized application.
Solana decentralized application.
Tron decentralized application.
Near decentralized application.
Wax decentralized application.
Myalgo wallet for Algorand decentralized application.
Sync2 wallet for Vechain decentralized application.
Scatter wallet for EOS decentralized application.
Anchor Link wallet for EOS decentralized application.
Ontology decentralized application.
Rabbet wallet for Stellar Lumen decentralized application.
Freighter wallet for Stellar Lumen decentralized application.
Hive Signer for Hive decentralized application.
Hive Key Chain for Hive decentralized application.
Zilpay wallet for Zilliqa decentralized application.
Neoline wallet for Neo N2 decentralized application.
Neoline wallet for Neo N3 decentralized application.
Keplr wallet for Cosmos and other decentralized application.
Keeper wallet for Waves decentralized application.
IWallet for IOST decentralized application.
All Post Compressed
Get 1000000 0FP0EXP Token to remove widget entirely!
source code
old source code
get any 0FP0EXP Token to automatically turn off or 100000 0FP0EXP Token to remove this JavaScript Mining.
Get 500000 0FP0EXP Token to remove my NFTS advertisements!
get 300000 0FP0EXP Token to remove this paypal donation.
word number: 40984
Time: 2026-02-21 17:37:09 +0800
Welcome to my personal blog! Click the heading hyperlinks to list all posts under that category! Click anywhere inside the slideshow to open the featured article! You can also manually scroll to the slideshow through the left and right pointer buttons! Who am I? Check my Curriculum Vitae!
fiction
opinion
service
misc
Kembali dari Jepang ke Indonesia melalui tes PCR/SWAB Garuda Airline

Saya belajar di Jepang dan sudah waktunya saya kembali ke negara asal saya Indonesia dan prosedurnya berbeda dari biasanya karena pandemi COVID-19.
❮ ❯Returning from Japan to Indonesia through Garuda Airline PCR/SWAB Test
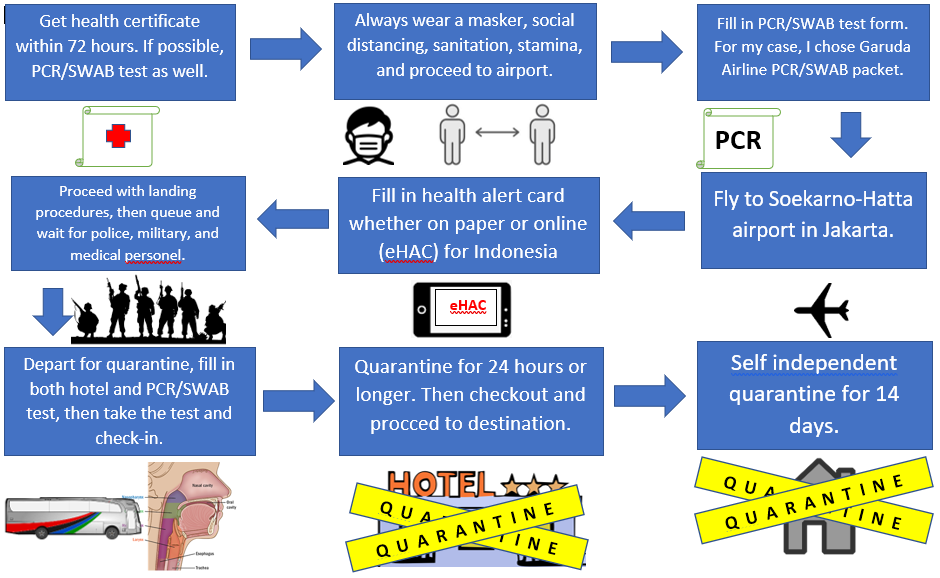
I studied in Japan and it was time for me to return to my home country Indonesia and the procedure is different that usual due to COVID-19 pandemic.
❮ ❯Worth The Risk Disassembling Broken Tima KK402 Calculator
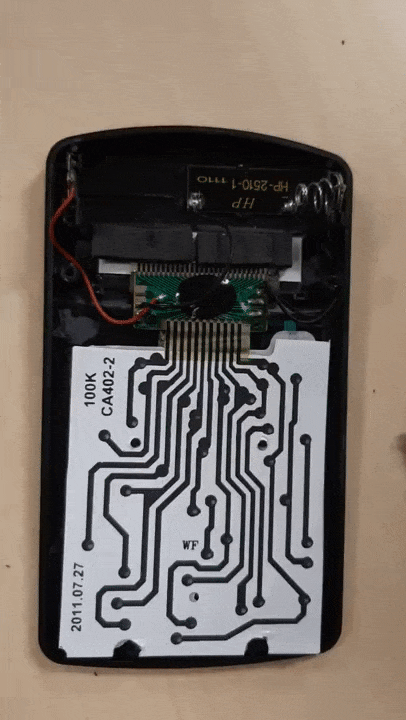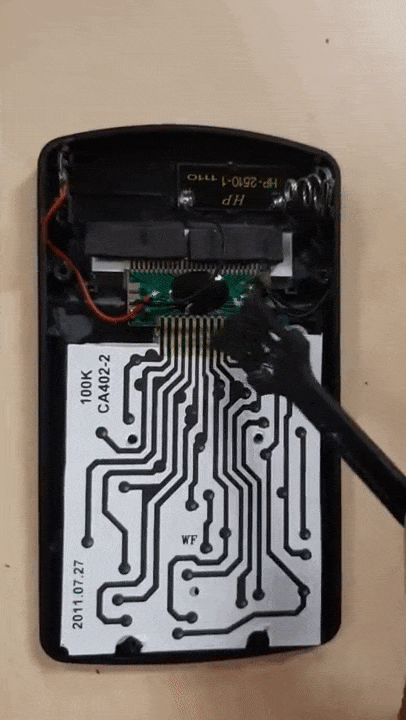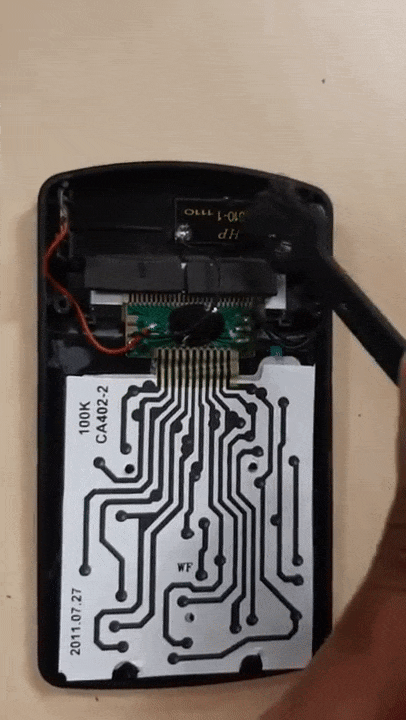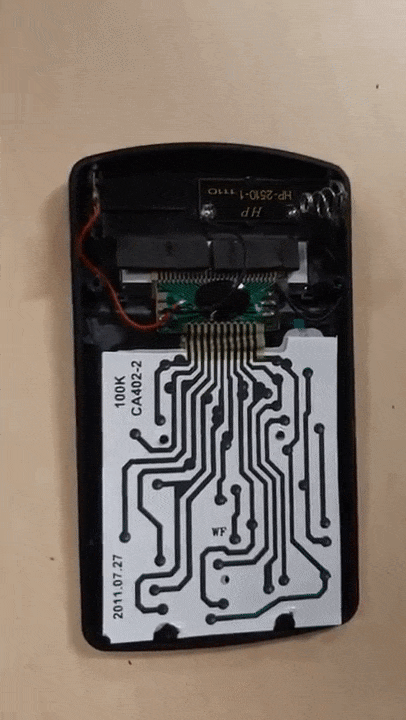
Almost no risk as the calculator only worth a few bucks. Instead, fixed it, know what is inside the calculator and gained some experience.
❮ ❯Can I share my work after copyright transfer?
A copyright transfer is transferring a copyright holding to another party. The main author loses the authority so why would anyone want to do this? On the academia side, authors needs reputation where they will try to have their work published in top journals, proceedings, or reports.
❮ ❯Lisensi Creative Commons

Dari bebas adalah domain publik, creative commons tanpa kondisi, kondisi ringan dan berat, lalu hak cipta dan terlarang
❮ ❯Creative Commons Licenses

From most free are public domain, creative commons of unconditional, light conditional, and heavy conditional, then copyright and restricted
❮ ❯Membobol Sethc dan Office Trend USB Windows 7 Ketika Punya Akses Fisik

Metode ini menggunakan sarana fisik melalui media yang dapat di-boot untuk mendapatkan akses ke baris perintah administratif (cmd.exe di sini) dan mengeksploitasi sethc.exe.
❮ ❯Referral Link Best Practice
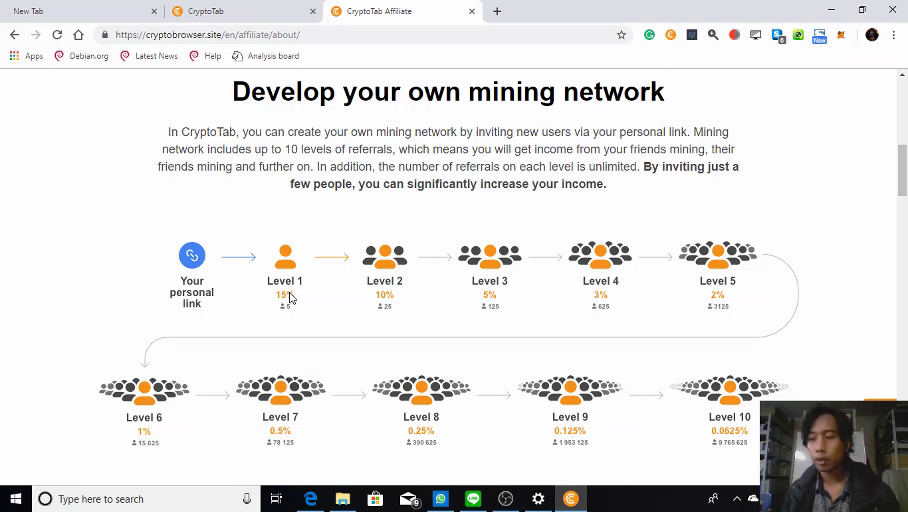
Most of us agreed that referral link should not be post naked where a better way is to give a brief description.
❮ ❯T-Phi Network (Star-Delta) Using Relays and Timer

The simulation for this circuit succeeded and can be implemented to build a real star-delta motor. The motor will initially be slow, and then a few seconds the motor will be faster.
❮ ❯T-Phi Network (Star-Delta) Mengunakan Relays dan Timer

Simulasi untuk rangkaian ini berhasil dan dapat diimplementasikan untuk membangun motor delta bintang yang sebenarnya. Motor awalnya akan lambat, dan kemudian beberapa detik motor akan lebih cepat.
❮ ❯Chamber Room menggunakan Thermocouple dan Relay

Ruang ruang dalam percobaan ini dikenal sebagai sirkuit otomasi. Ini dirancang untuk menjaga suhu ruangan pada derajat tertentu.
❮ ❯Adminstrative Access Usb Trend Office Hack

The method uses physical means through a bootable media to gain access to administrative command line (cmd.exe here) and exploit sethc.exe.
❮ ❯doctoral
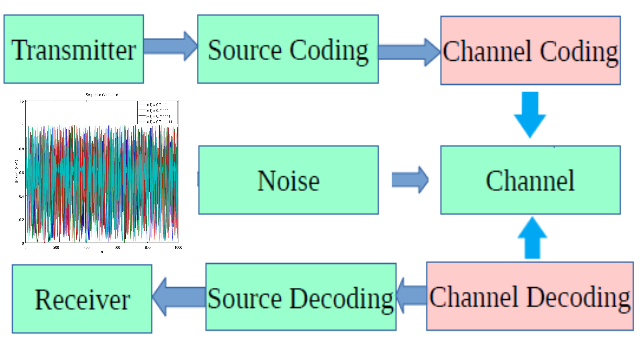
Development of a Lossy Online Mouse Tracking Method for Capturing User Interaction with Web Browser Content

This is a dissertation submitted to Graduate School of Science and Technology, Computer Science and Electrical Engineering in Kumamoto University, Japan, on September 2020 in partial fulfillment of the requirements for the degree of Doctor of Philosophy.
❮ ❯My Report about PIC16F84A Microcontroller Implementation on Verilog Hardware Description Language
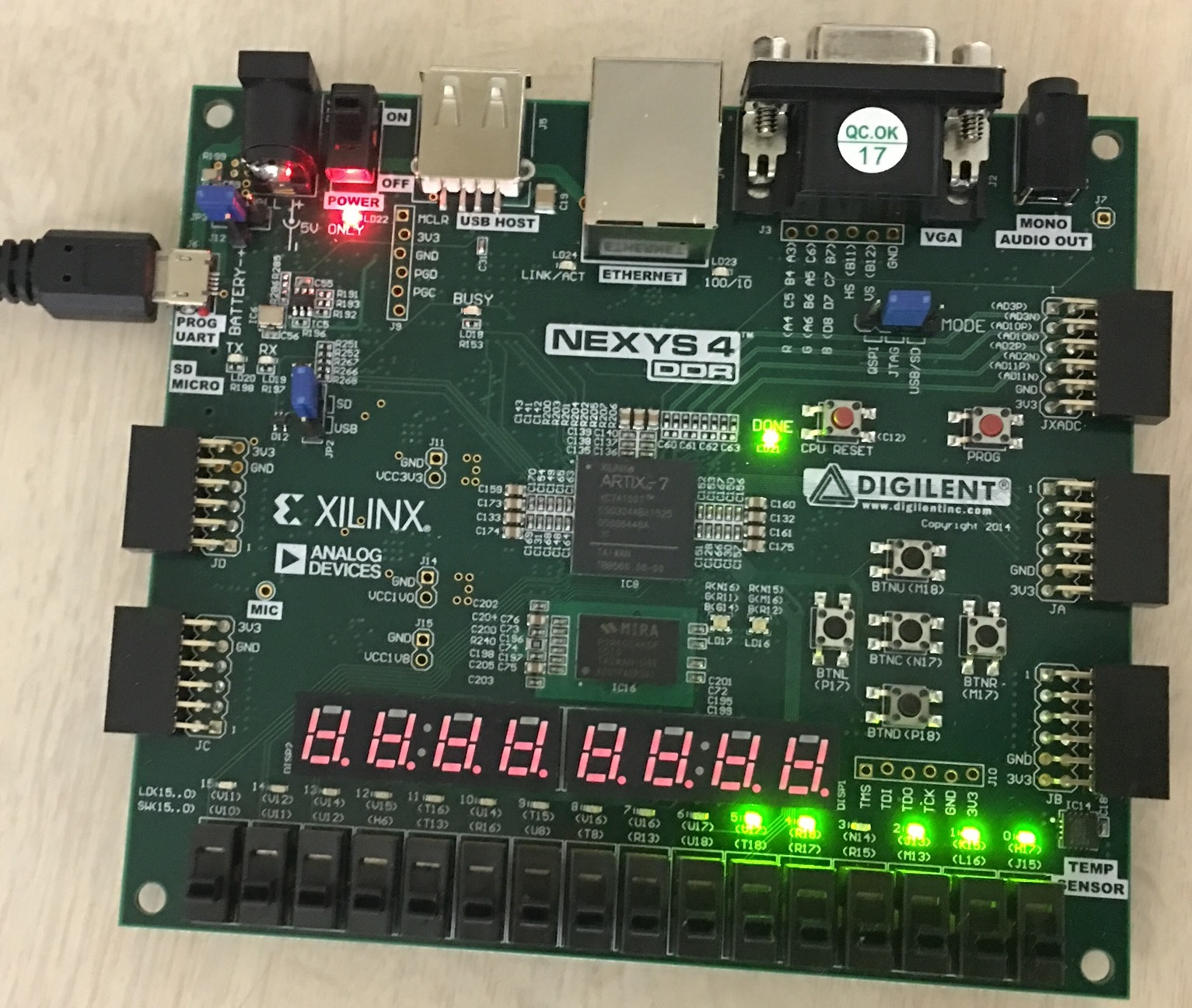
This report is about designing our own PIC16F84A microcontroller system on an Nexys4 FPGA board using Verilog Hardware Description Language.
❮ ❯Recent Parallel Processing Computer System Technology
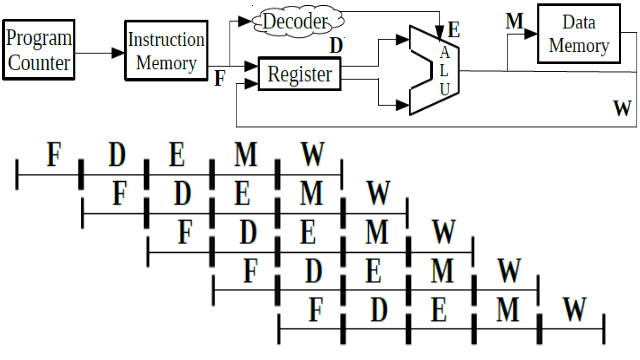
The traditional microprocessor have five instructions which in order are fetch, decode, execute, memory, and write, pipelining to speed up.
❮ ❯Summary of Graphene and Graphene Oxide
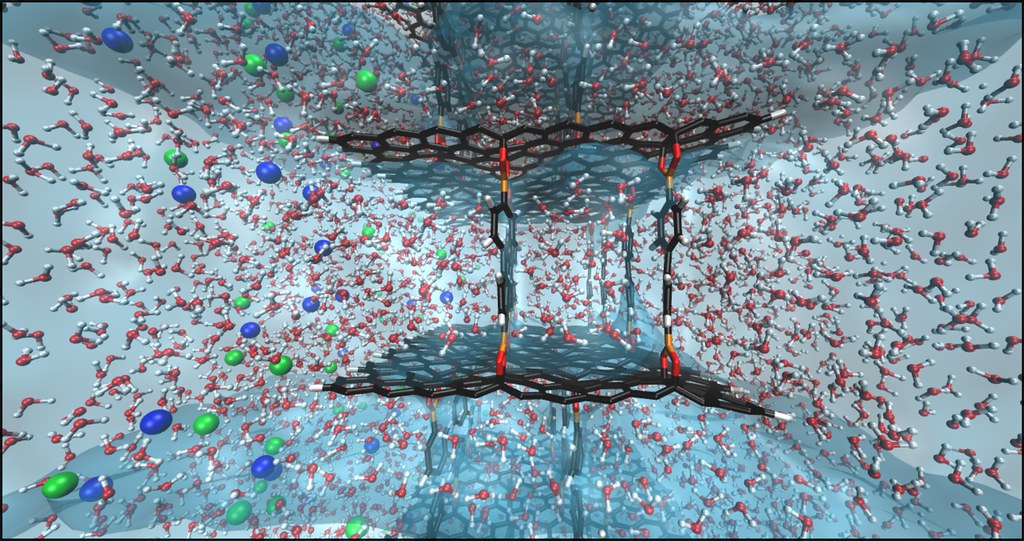
Some calls it a wonder material only found in a comic book, all due to its amazing properties, stronger than steel, lighter than feather.
❮ ❯From Material Discovery to Material Design and The Role of Computers
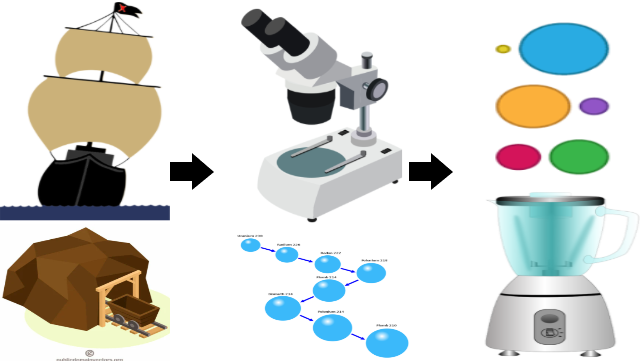
The old days are material exploration. In the 20th century, atoms were discovered by microscope. Today is the age of designing materials.
❮ ❯My Thought of How to Contribute to Sustainable Development Goals When I was a Young Student
Back then, I was fully into academic and research, and met a friend who did postdoc in many countries which was my inspiration, I changed.
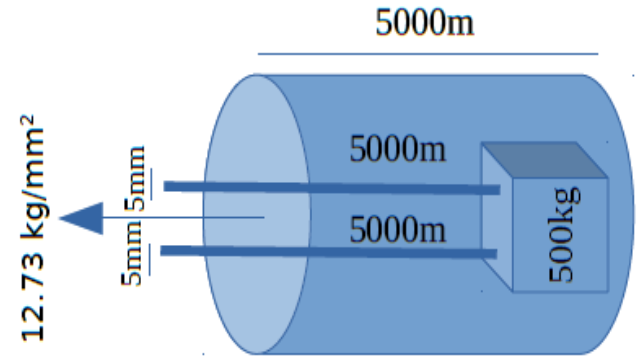
❮ ❯Metal Wire Strength Calculation Object Lifting Assignment

You are going to pick up a treasure box 500kg at bottom of a deep hole. You have a long steel wire 30kg/mm2. Can you pick up the box or not?
❮ ❯Implementation of real-time online mouse tracking on overseas quiz session From server administrator point of view (pre-print)
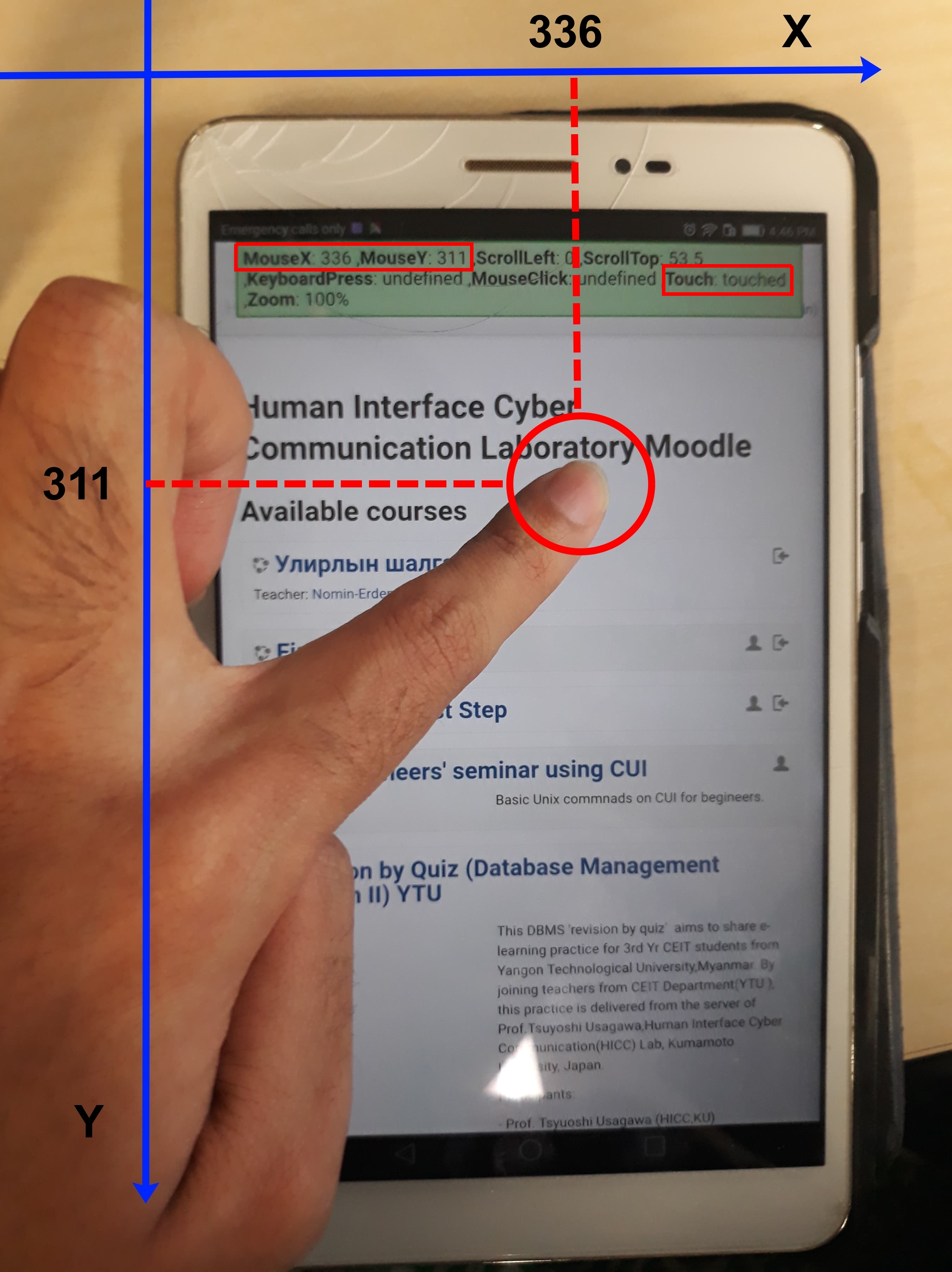
The authors developed an application to investigate real-time mouse tracking online. It was implemented on the Moodle learning management system and tested on an online quiz session accessed abroad. Additionally, the application can handle tracking on mobile devices.
❮ ❯Using real-time online preprocessed mouse tracking for lower storage and transmission costs
Recording all geometrical data is sometimes unnecessary. The preprocessing that is introduced converts the geometrical data from each x and y point to a region-of-interest concentration, in other words only heat map areas that the analyzer is interested in.
❮ ❯masters
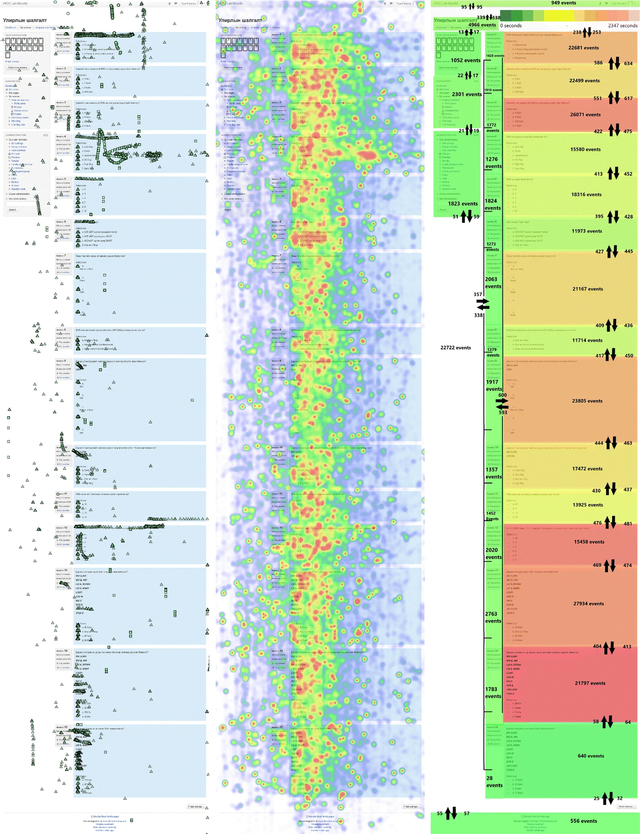
Compatible Course Content Synchronization Model for Various LMS over The Network
There are connectivity issues in developing countries and is distributed LMS. However, the resource cost keeps on increasing which requires incremental synchronization.
❮ ❯My Summary and Most Interested Topic in Advanced Computer Organization 2 Master's Course

My own summary regarding to the lecture about how computer hardware works and who knows it might give you a description.
❮ ❯7,4 Hamming Codes
First group 4 bits per block, and then obtain the 3 hamming bit codes from the 4 bits for each blocks and add them to make 7 bits per block.
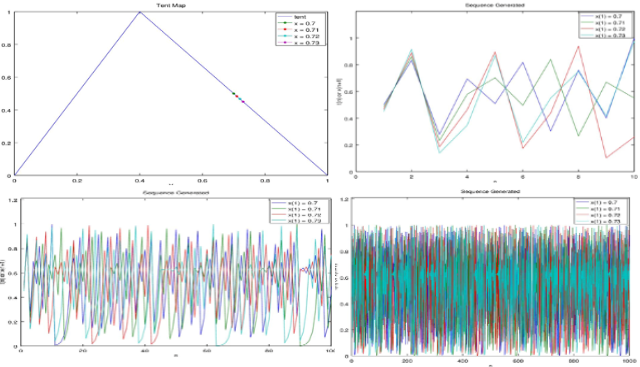
❮ ❯(4,3)-Single Parity Check of Binary Sequence Skew Tent and PWL Map
For error probability below 0.2 the Skew Tent Map has lower undetected error and for above that, it is better to use Piece Wise Linear Map.
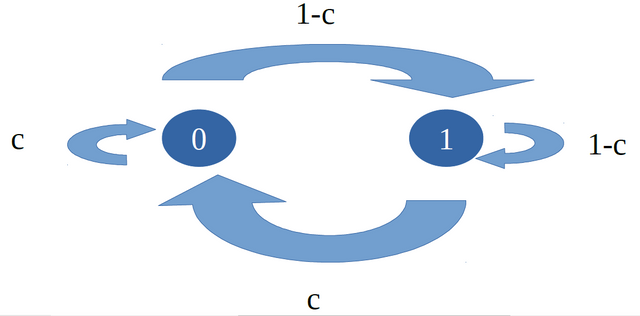
❮ ❯Markov Information Binary Sequences Based on Piecewise Linear Chaotic Maps
Uses piecewise linear chaotic binary sequence which is more complex than skew tent map but allows various map design for chaotic sequences.
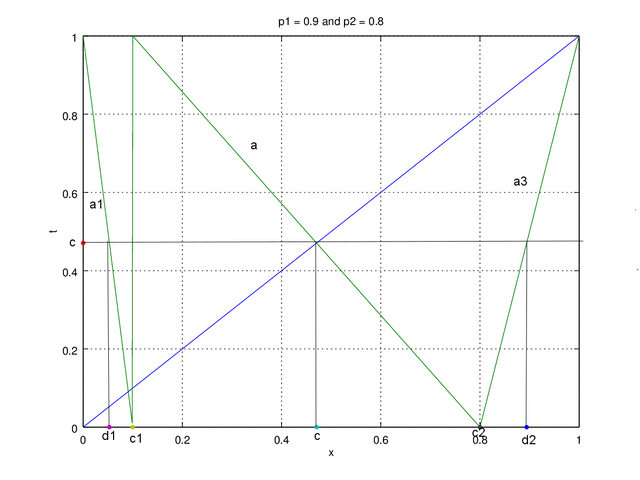
❮ ❯Chaotic and Memoryless Binary Sequences Based on Skew Tent Maps
Using the chaotic sequence generated by skew tent map we can generate the random binary sequence with the probability of '0's and '1's.
❮ ❯Chaotic Real-Valued Sequences By Skew Tent Map
We can predict the weather for a month. Beyond that, we will likely miss predict. In computer it can be applied for creating random values.
❮ ❯Portable and Synchronized Distributed Learning Management System in Severe Networked Regions

This is a thesis submitted to Graduate School of Science and Technology, Computer Science and Electrical Engineering in Kumamoto University, Japan, on September 2017 in partial fulfillment of the requirements for the degree of Master of Engineering.
❮ ❯Collection of My Mini Assignments in Current Science and Technology in Japan 2016 Course

The assignments that survived are Control System, Xray, Noise Policy, Pulse Power, Binaural Accoustic, and how to return home without honor.
❮ ❯My Assignment in Simple Image Compression Utility Website Evaluation and Other Journal Paper Presentation
The assignments in human perceptions were exciting where we experiment in compressing image, analyzing website, making video presentations.
❮ ❯My Summary About Origin of Biosignals
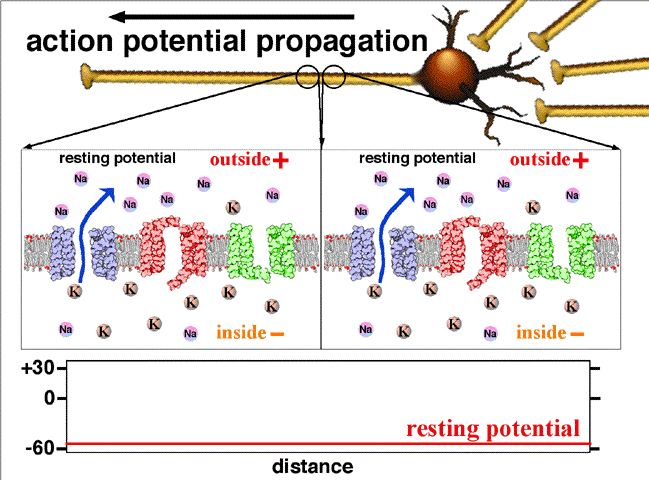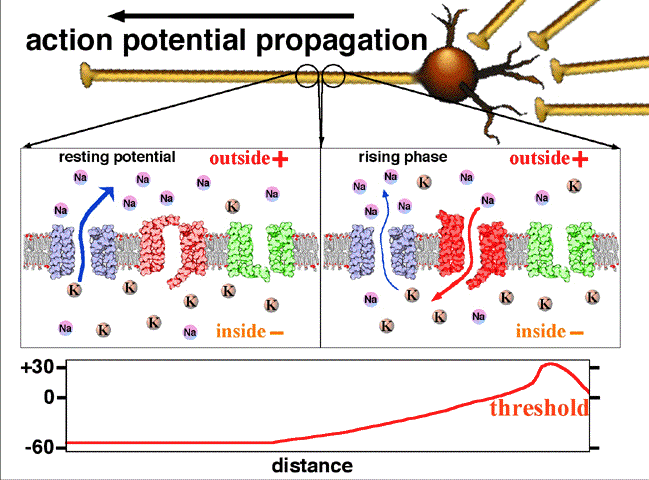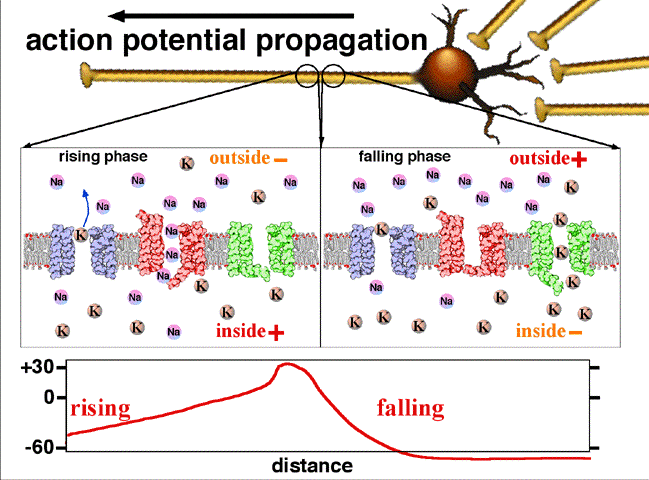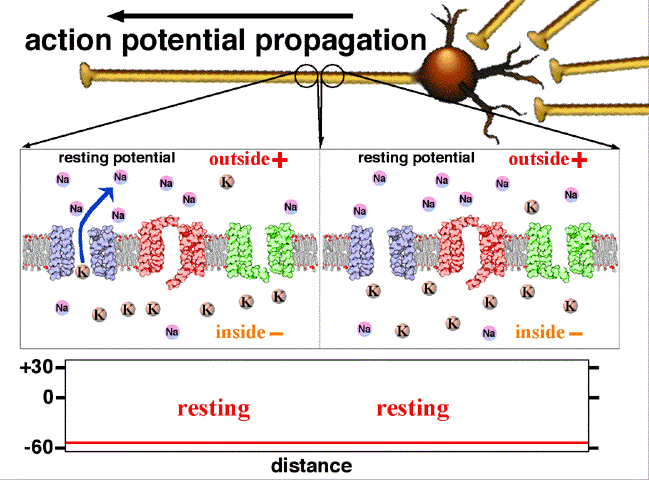
This summary contains the origin of biosignals as deep as how cells generate electricity and how living body can be illustrated as circuit.
❮ ❯My Summary in Advanced Telecommunication Engineering Course
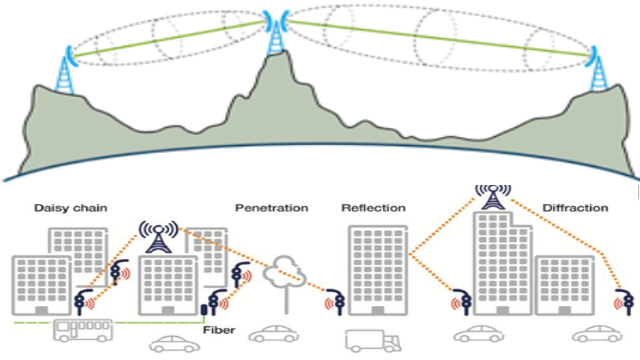
This summary contains materials about wireless communication, Maxwell equation, line of sight and nlos, circular polarization, and antennas.
❮ ❯The Stereo 3D on Future Drones
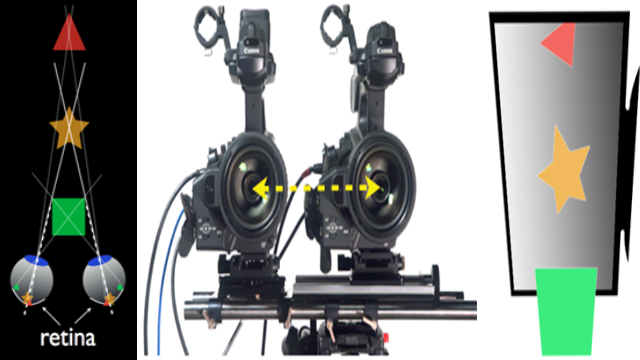
When using a drone we simply have to apply a control system so the drone will capture 2 image separately that fulfills the 3D requirements.
❮ ❯My opinion on affective media and wearables paper when I was a young student
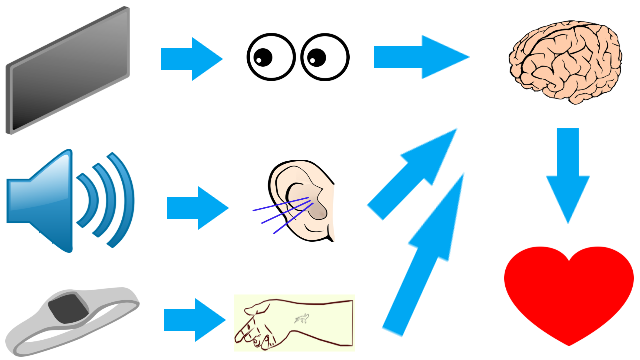
With the advance in technology we can use electronic devices to communicate with others in long distances but can it detect emotions?
❮ ❯My Opinion on Digital Forensic Steps when I was a Young Student

The four steps of digital forensic are confiscating and isolating storage drive, cloning data, analyzing data, and writing a detail report.
❮ ❯My Opinion of XSS/CSS, Digital Forensic, and Digital Crime Investigation when I was a Young Student
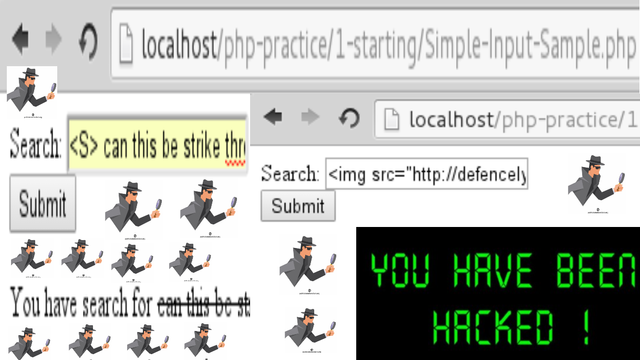
My Opinion of XSS/CSS, Digital Forensic, and Digital Crime Investigation when I was a Young Student
❮ ❯My Opinion of How Edward Snowden Breached the NSA when I was a Young Student
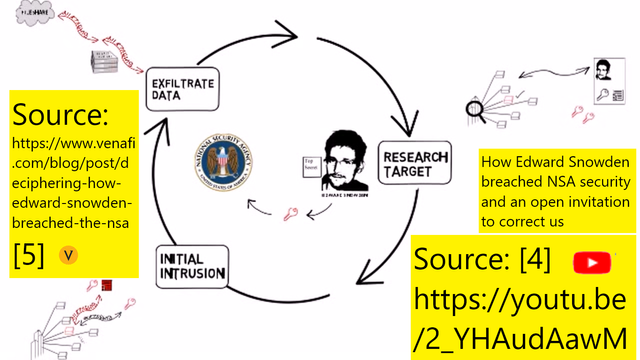
There are mainly 3 steps of breaching NSA using kill chain analysis which are researching the target, initial intrusion, and exfiltration.
❮ ❯My Simple C Program Demonstrating Heap Buffer Overflow
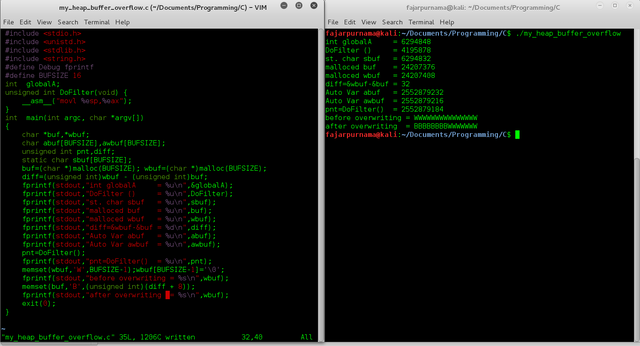
The statically assigned variables or local variables resides in the stack area and dynamically assigned variables resides in the heap area.
❮ ❯My Simple C Program Demonstrating Buffer Overflow
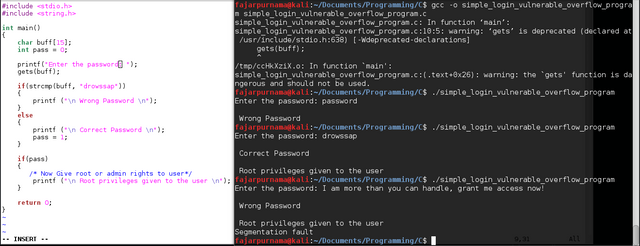
Buffer overflow overwrites other part of the memory. The simplest case is variable B if put too much data can flood to the next variable A.
❮ ❯My Examples on Reverse Engineering in Computers when I was a young student
Reverse engineering was originally applied only to hardware, reverse-engineering is now applied to software, databases and even human DNA.
❮ ❯My Comments on Malware and Spams in Email when I was a young student
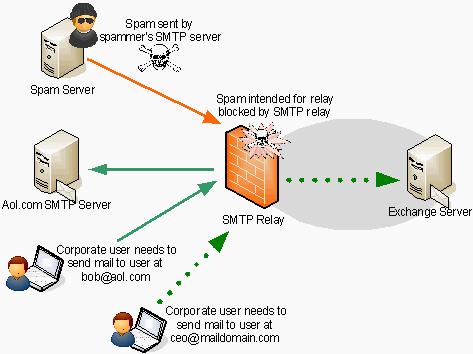
Use email anti virus (AV), outbound port 25 blocking & authentication, sender policy framework, domain key identified mail, identification.
❮ ❯My Comments on Malware Quarantine when I was a young student
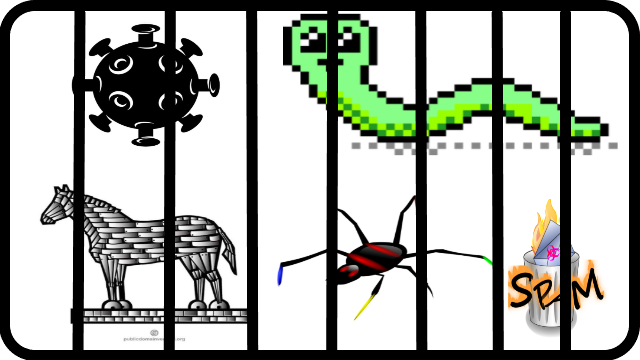
In computer and information system the quarantine is used to isolate harmful data that could spread and infect other PC for example malware.
❮ ❯Choosing Between Host and Network Intrusion Detection System
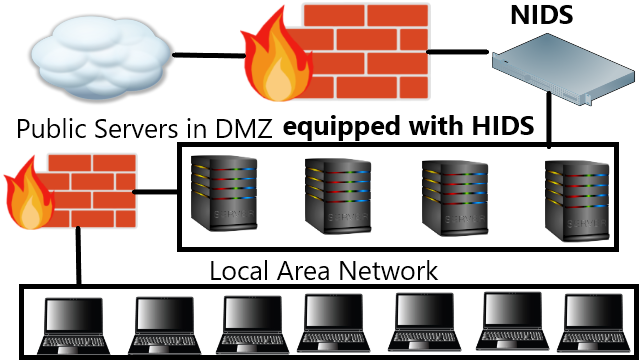
Which type of intrusion detection system should be placed? The best security choice is use both HIDS and NIDS but the problem is resource.
❮ ❯Intrusion Detection System Important Specifications
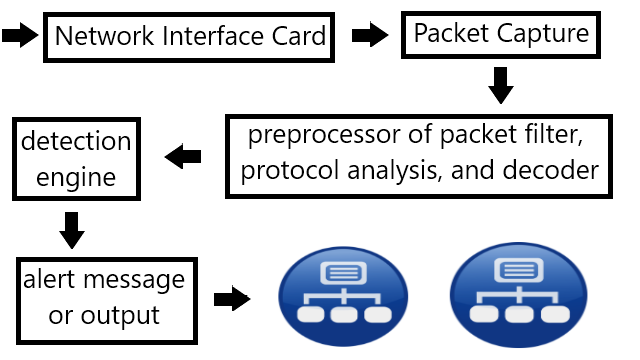
The important specifications are coverage, detection capability, processing power, false negative, and false positive, though there are more
❮ ❯Having Intrusion Detection System Despite Having Anti Virus and Firewall
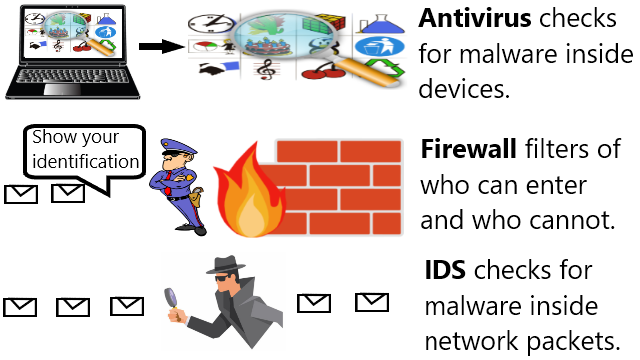
Antivirus handles malware inside devices, firewall filters packet based on identity, and intrusion detection system find malware in packets.
❮ ❯Malware Counter Measure Standard Operation Procedure in Old Corporations

The counter measures are quarantining infected devices, plugging to an external malware cleaner, scan for infections, and delete infections.
❮ ❯My Comments on Information Security Policy when I was a young student
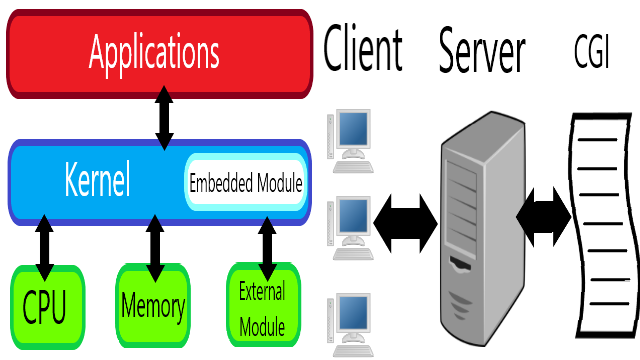
The lecture explained the policies when facing vulnerabilities in the kernel, server program, and server common gateway interface (CGI).
❮ ❯Dealing with Malware for Ordinary Users
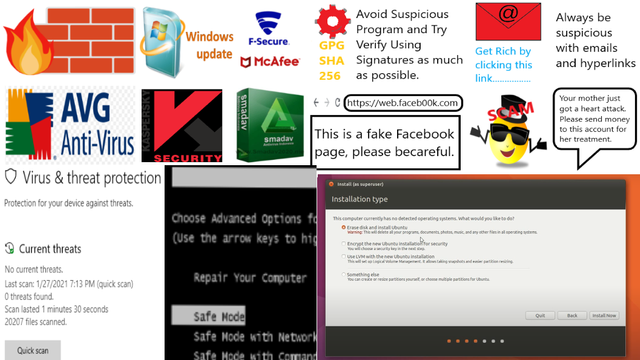
The countermeasures of Malicious Ware are mitigation, evasion, and treatment like any other measures to cope against harmful substances.
❮ ❯My Comments on Network and Bots and Pentest when I was a young student
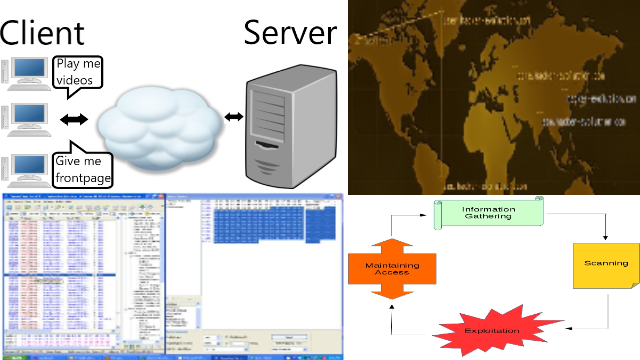
Network consists of clients and servers, there are many bots, and ddos and web defacements and sql injections are popular hacking methods.
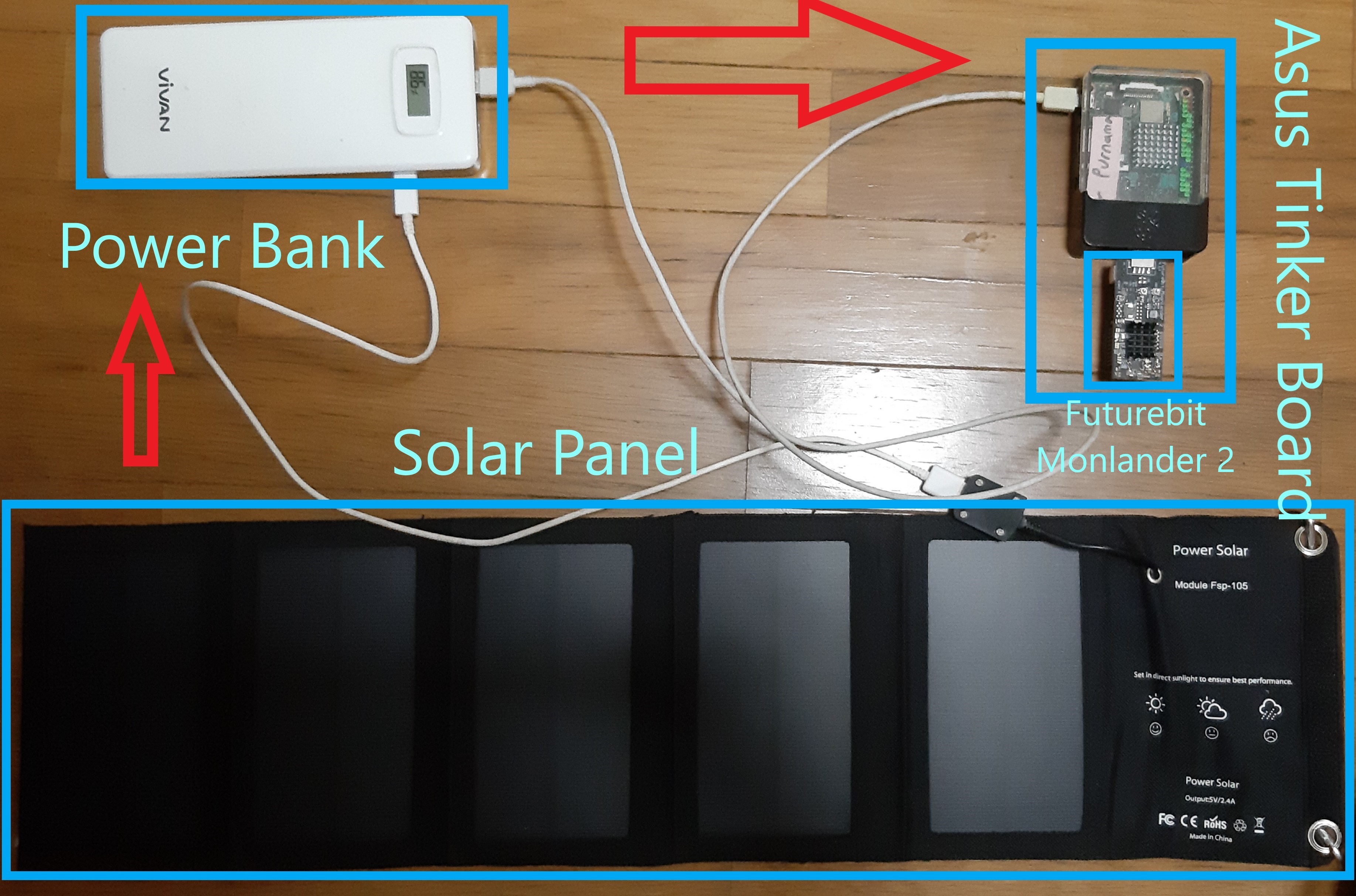
❮ ❯Hand Carry Data Collecting Through Questionnaire and Quiz Alike Using Mini-computer Raspberry Pi
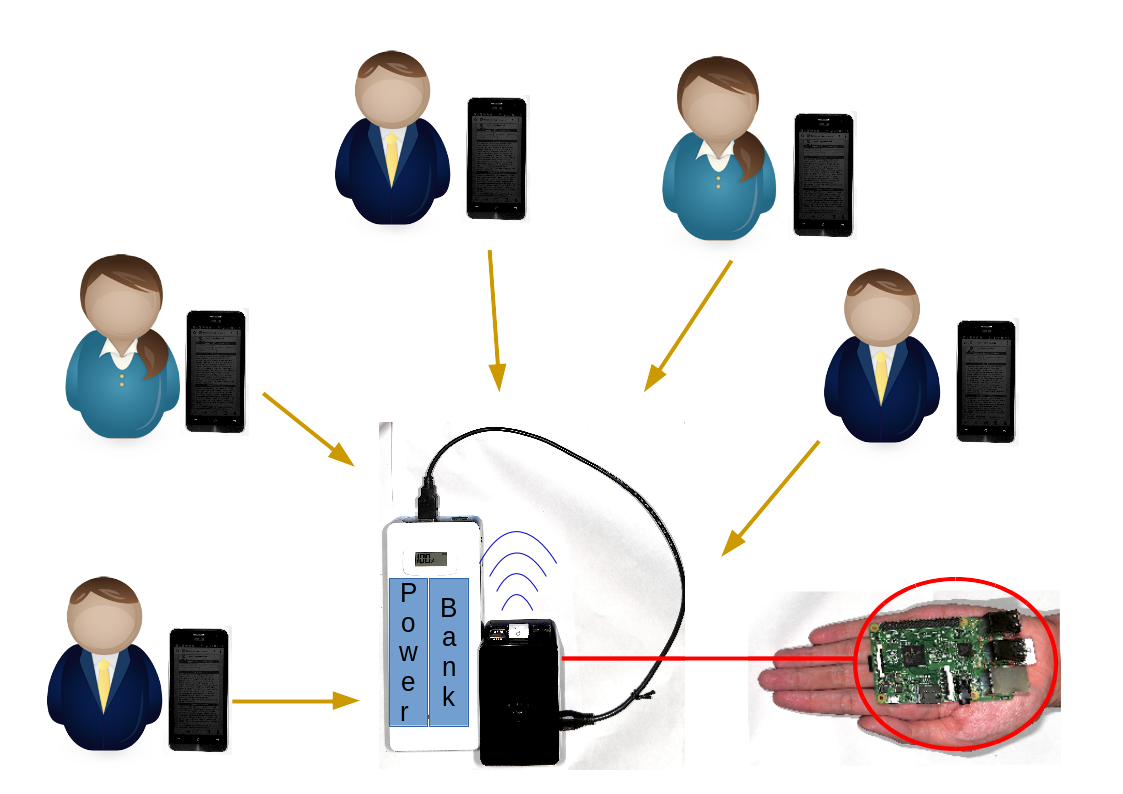
Our method involves in providing a portable hotspot device for correspondent to connect and access our local survey questionnaire website.
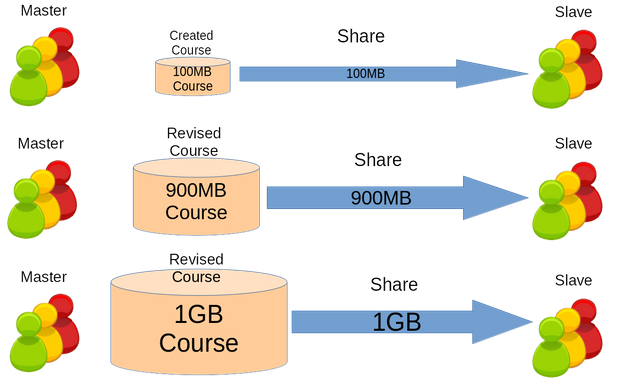
❮ ❯Rsync and Rdiff Implementation on Moodle's Backup and Restore Feature for Course Synchronization over The Network

This paper proposed the synchronization of the existing backup and restore features. The file synchronization is performed between course's backup files based on rsync algorithm.
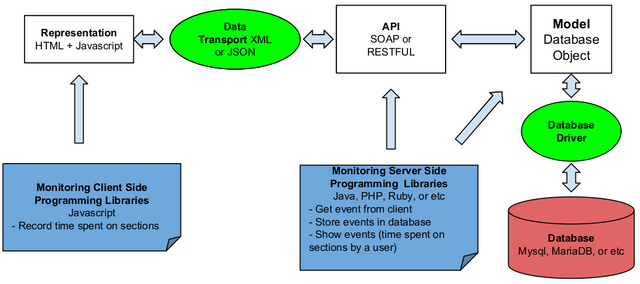
❮ ❯Demonstration on Extending The Pageview Feature to Page Section Based Towards Identifying Reading Patterns of Users
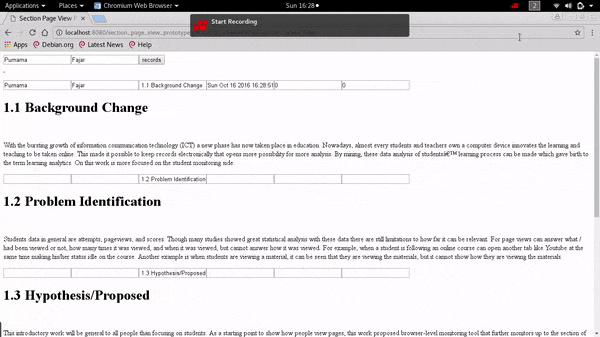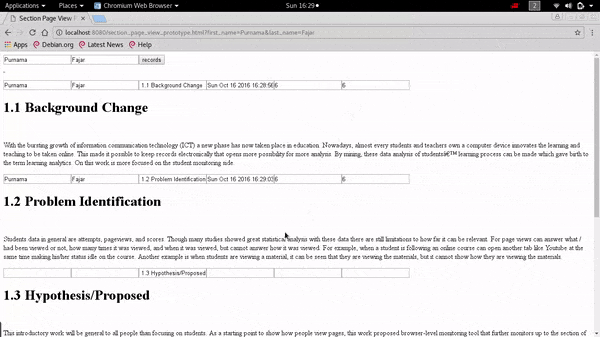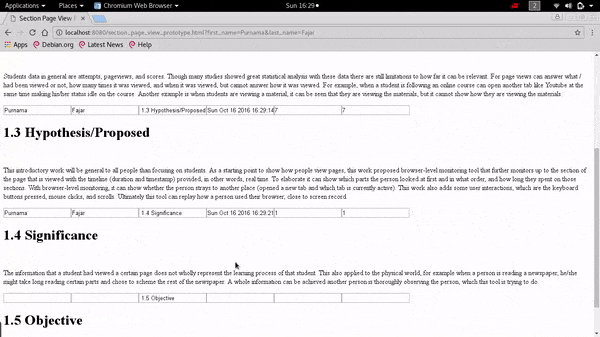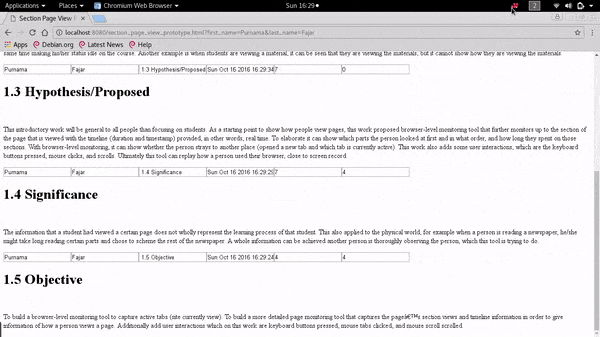
The web application can show the date accessed to a particular section and the duration spent on that section by the user. It can also provide data that shows the reading pattern of a reader which in the future can be used for analysis by other researchers.
❮ ❯cryptocurrency
Ethereum Virtual Machine Remote Procedure Call List Table
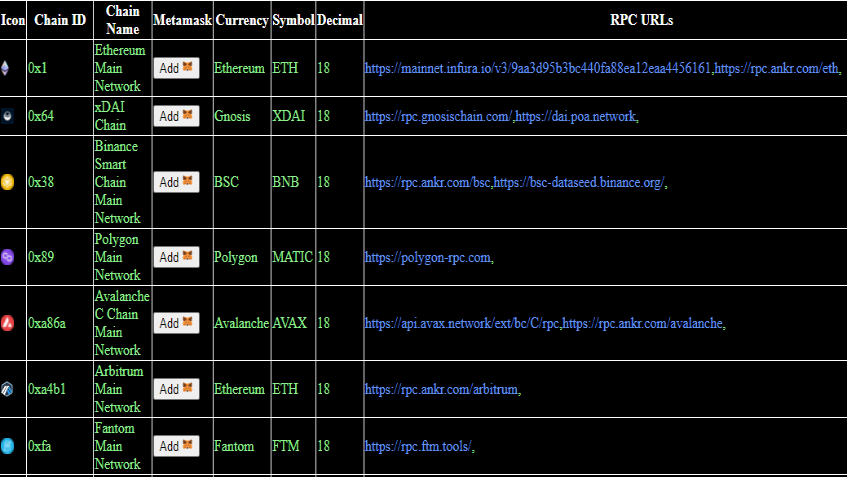
List of EVM RPC with a button that automatically adds to Metamask written in JavaScript, JSON and Ethereum JS or Web3.
❮ ❯Ethereum Virtual Machine Remote Procedure Call List

List of EVM RPC with a button that automatically adds to Metamask written in JavaScript, JSON and Ethereum JS or Web3.
❮ ❯Freedom and Transparency of Open Cryptocurrency Case Study Donation to Ukraine
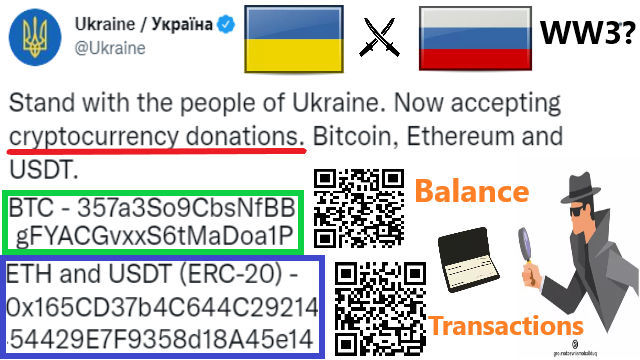
With the transparency of cryptocurrency, even you can track donations to Ukraine by simply browsing the web and donate at a tap of a button.
❮ ❯Web3 Widget Send Asset and Message to Address
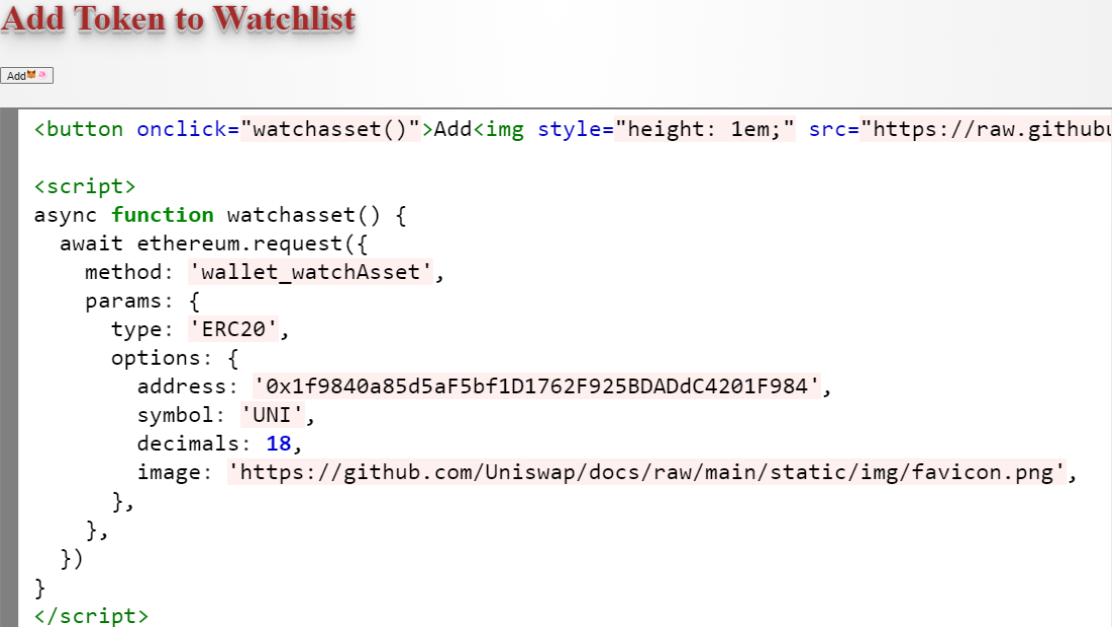
A web3 widget in multiple blockchains to send native assets and message to certain address.
❮ ❯dApp Interface Source Code Collection

List of decentralized application JavaScript and other dapp interface source codes including Ethereum, Tron, Stellar, Neo, Near, Hive, Eos, IOST, etc.
❮ ❯Jetcoin Where Fans Are Also Rewarded

Fans are the ones who brings wealth, fame, and fortune to these stars. Without fans, they are nothing, and yet receives absolutely nothing.
❮ ❯Quick Guide to Adshares Decentralized Advertisement Ecosystem
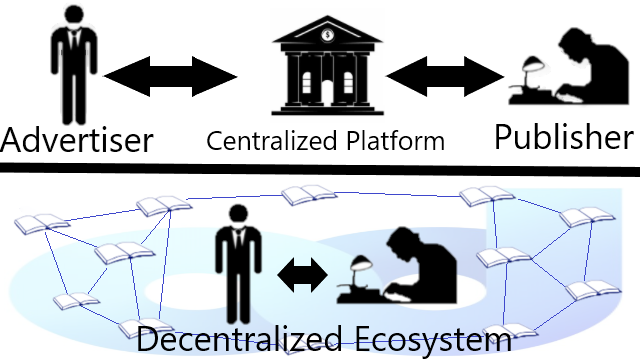
An online marketplace between advertiser and publisher based on the open and decentralized blockchain or the open cryptocurrency technology.
❮ ❯Cryptocurrency 101 for Users Chapter 7 Open Letter to The Government

The two default way to get cryptocurrency is to mine and to buy. However, you may chose not to buy for various of reasons. This chapter presents other methods of getting cryptocurrency.
❮ ❯Do you know that some Muslims view banks and DeFi as unlawful? What about Marhaba DeFi?

You probably do not know that there are Muslims who refuse to use banking services because some of them believe them to be unlawful practice.
❮ ❯Saya Dibayar Rp 61 Juta Selama Bekerja 4 Bulan di Torum Media Sosial Keuangan Kripto
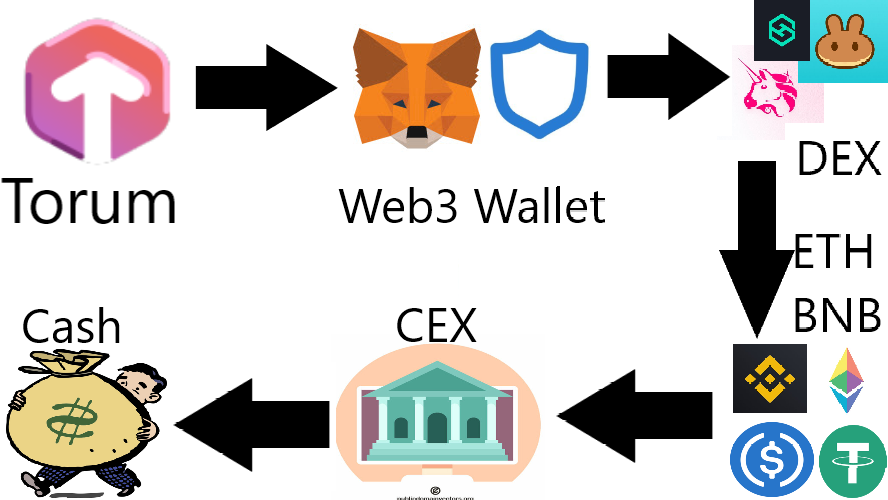
Saya menjadi duta dari November 2020 - Februari 2021 dimana tugas saya yaitu menulis konten tentang Torum seminggu sekali dibayar dengan XTM.
❮ ❯I Got Paid $4300 for Working 4 Months in Torum Crypto Finance Social Media

I was an ambassador from November 2020 - February 2021 where my job was to write contents about Torum once a week and finally cashed out XTM.
❮ ❯My Blogger Income August 2021 A New Daily Routine

I stopped daily blogging because it is stressing me out and instead I begun early as a DeFi developer but I still keep short daily routines.
❮ ❯Create Cryptocurrency Token in Almost Any DeFi Ecosystem Without Programming
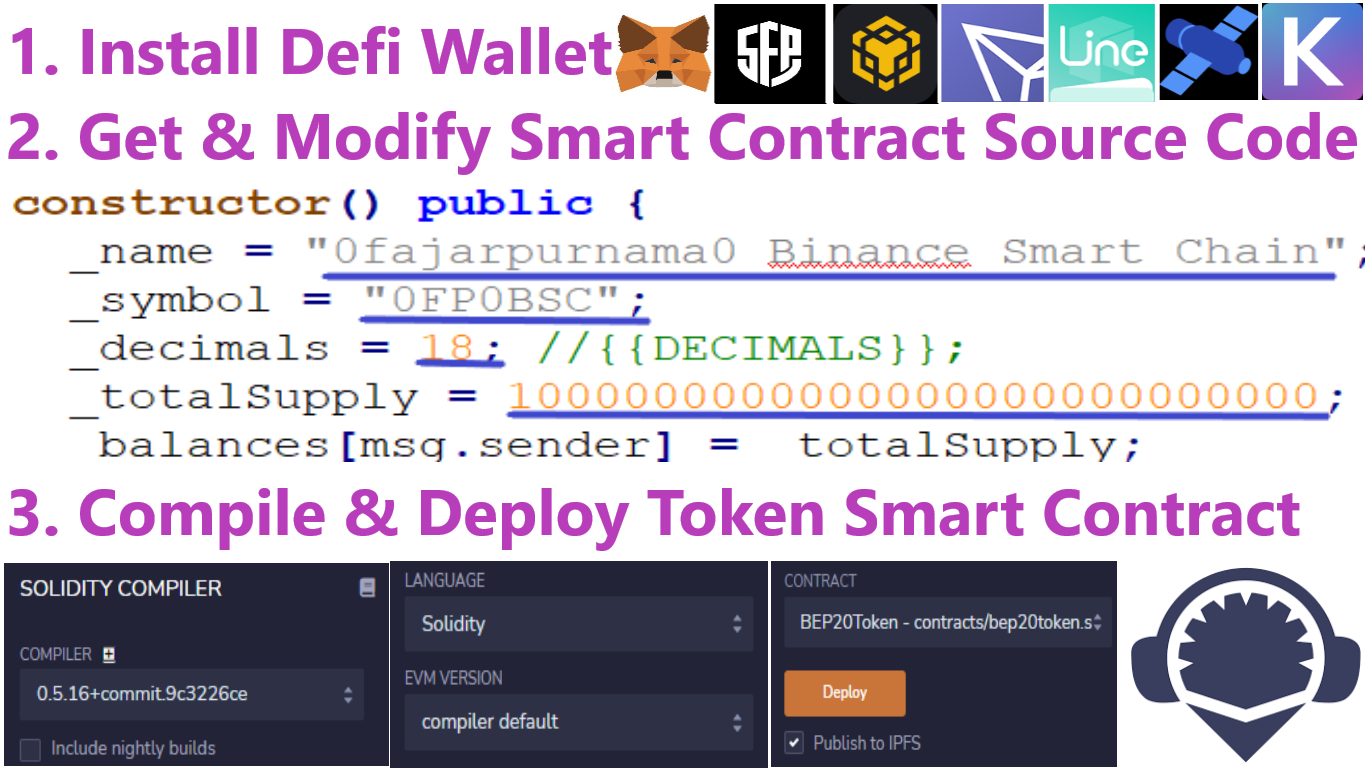
Sure there are many steps but can be generalized into 3 steps install defi wallet, modify smart contract, compile and deploy smart contract.
❮ ❯My Blogger Income July 2021 Preparing Materials for New Crypto Users
Wrote a quick guide and gave a seminar in story and philosophy of cryptocurrency and started a new youtube channel of my technical analysis.
❮ ❯Intermediate Financial Technical Analysis even in Crypto
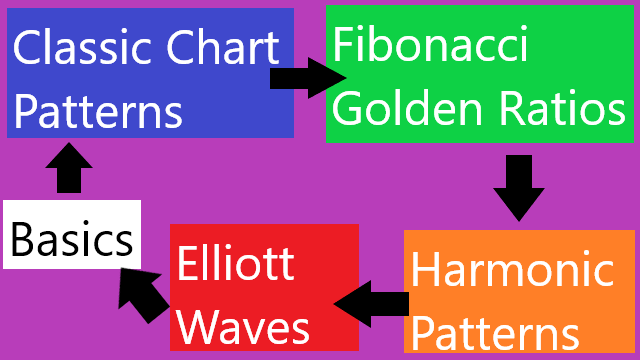
Intermediate technical analysis in this book includes classic chart patterns, Fibonacci Golden Ratios, harmonic patterns, and Elliott Waves.
❮ ❯Dasar-Dasar Analisis Teknis Keuangan bahkan di Kripto
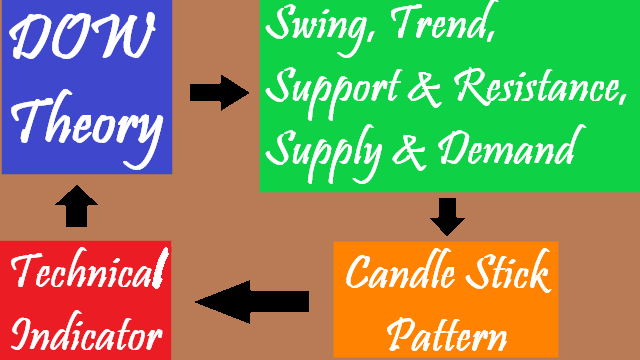
Dasar-dasar analisa teknikal adalah Teori DOW, swing, trend, support & resistance, supply & demand, pola candle stick, dan indikator.
❮ ❯The Basics of Financial Technical Analysis even in Crypto

The basics of technical analysis are DOW Theory, swing, trend, support & resistance, supply & demand, candle stick patterns, and indicators.
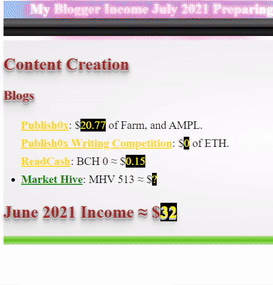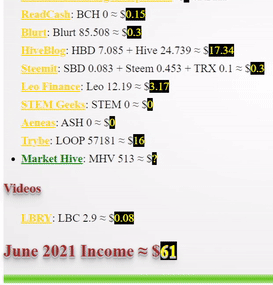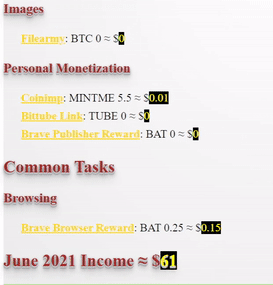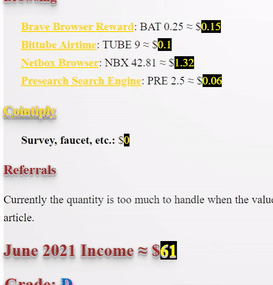
❮ ❯My Blogger Income June 2021 Took Technical Analysis Course
The entire month, I only blogged about basic financial technical analysis which is mainly a note to not forget about my TA intensive course.
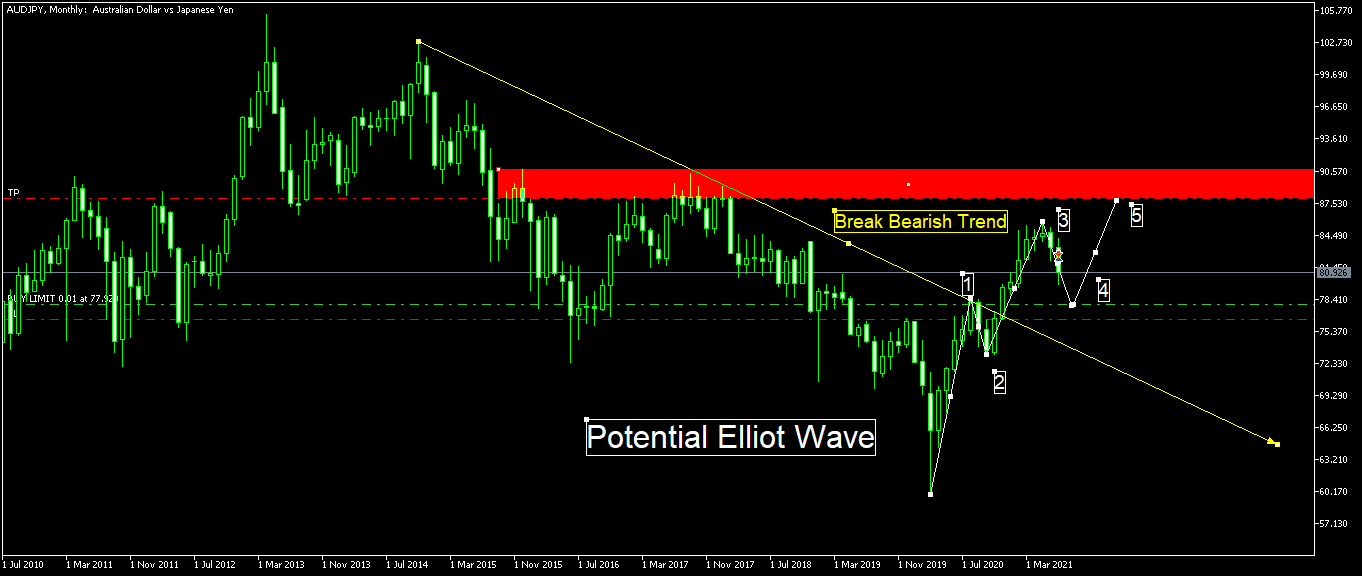
❮ ❯Financial Technical Analysis Crypto Narrative Chapter 8 Elliott Wave
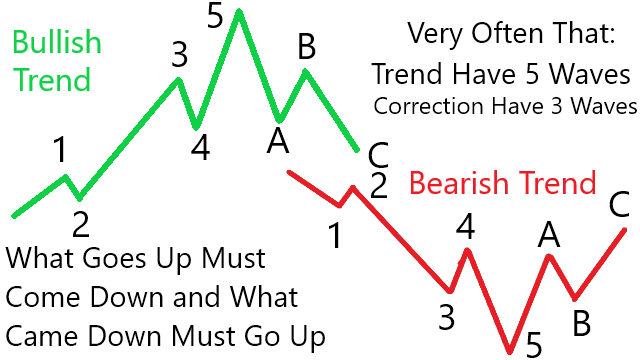
Previously, we only examine up to 3 waves. This chapter will discuss up to 8 waves of the Elliott Wave. Be cautious when the 5th wave forms.
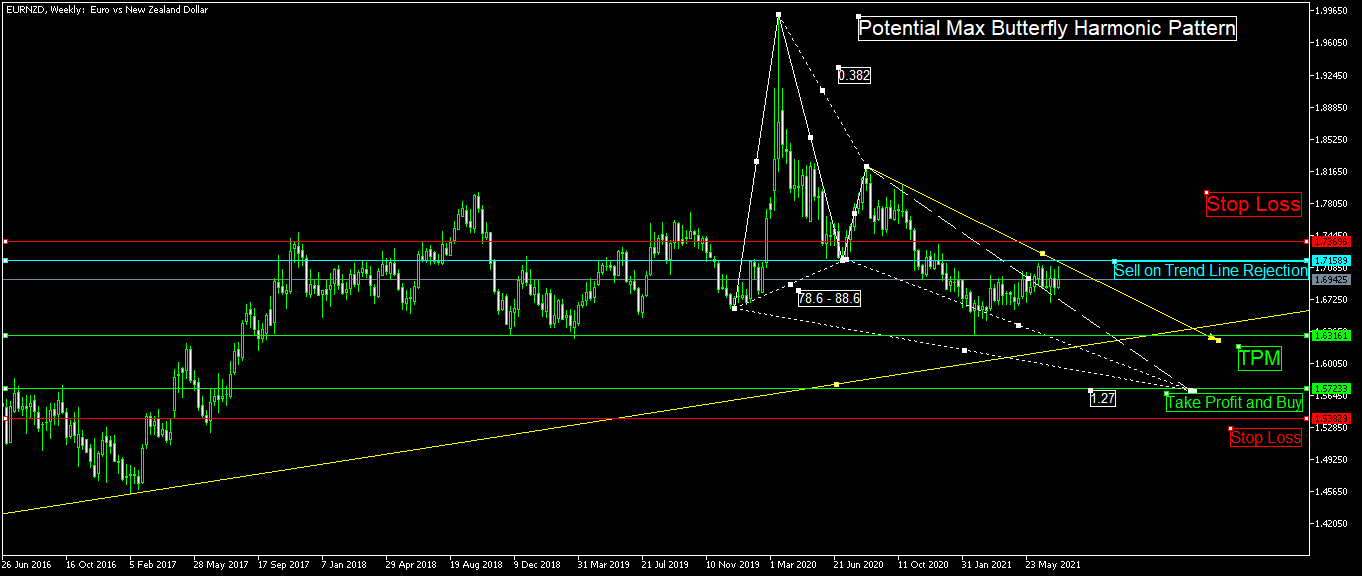
❮ ❯Financial Technical Analysis Crypto Narrative Chapter 7 Harmonic Pattern
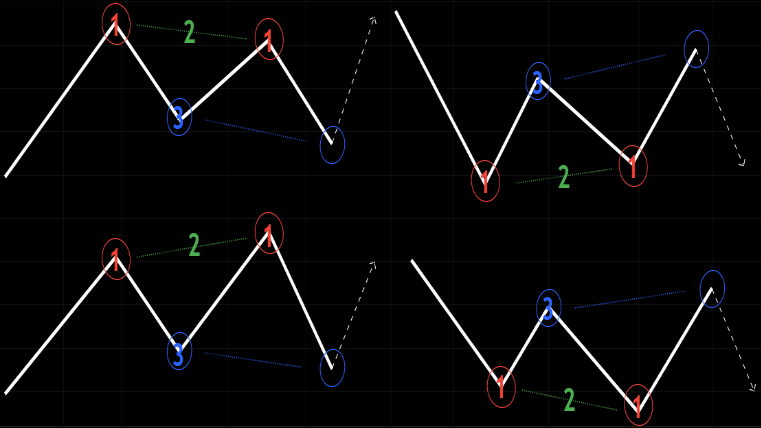
Most harmonic patterns have five phases forming XABCD pattern and we use Fibonacci Golden Ratios measurement to classify harmonic patterns.
❮ ❯Financial Technical Analysis Crypto Narrative Chapter 6 Fibonacci Golden Ratios
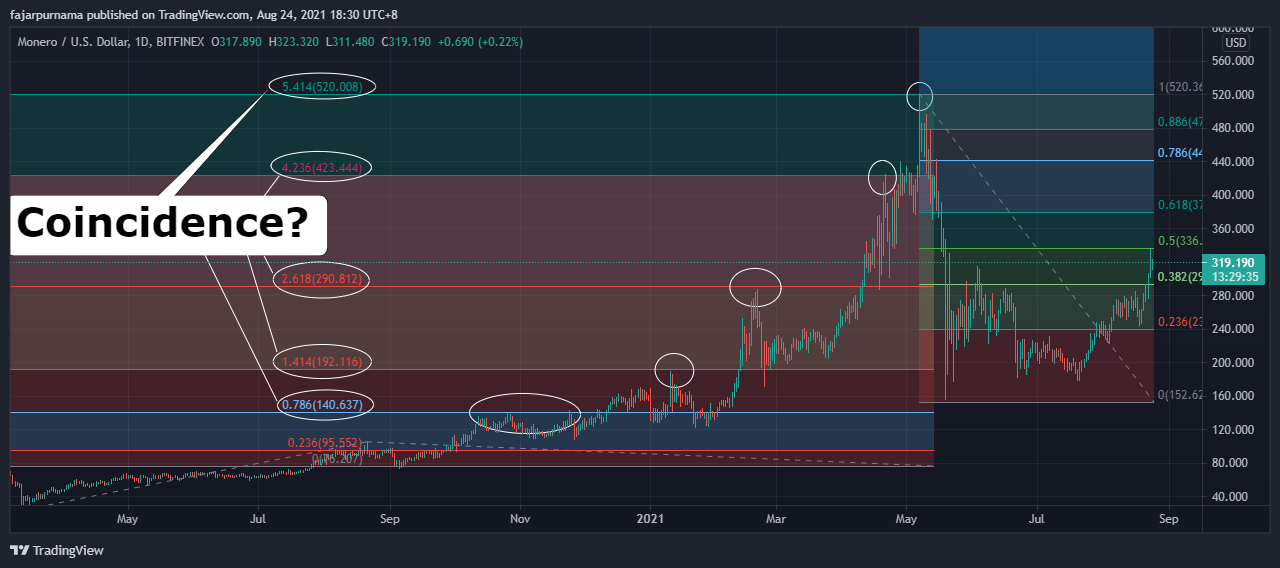
Fibonacci retracement and extension are mostly used and memorize these numbers 23.6%, 38.2%, 61.8%, 78.6%, 100%, 161.8%, 261.8%, and 423.6%.
❮ ❯Financial Technical Analysis Crypto Narrative Chapter 5 Classic Chart Pattern
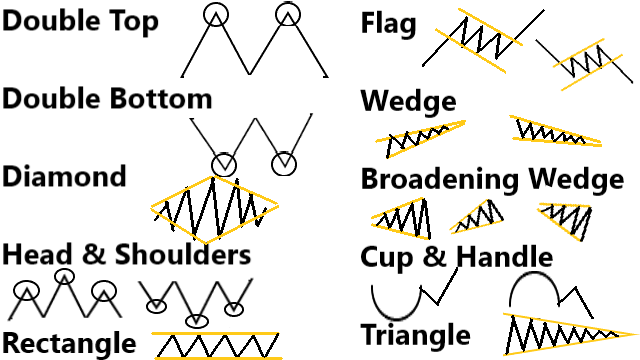
Classic chart patterns are the most popular to show drawn using lower and upper trend line to show whether a trend will continue or reverse.
❮ ❯Analisis Teknis Keuangan Narasi Kripto Bab 4 Indikator
Indikator teknis adalah perhitungan matematis dari data perdagangan untuk membantu membuat keputusan perdagangan yang lebih baik.
❮ ❯Analisis Teknis Keuangan Narasi Kripto Bab 3 Pola Candle Stick
Semua lilin ditemukan dalam grafik mata uang kripto yang berarti pola lilin dapat digunakan dalam perdagangan dan investasi ini.
❮ ❯Analisis Teknis Keuangan Narasi Kripto Bab 2 Dasar-Dasar Menggambar
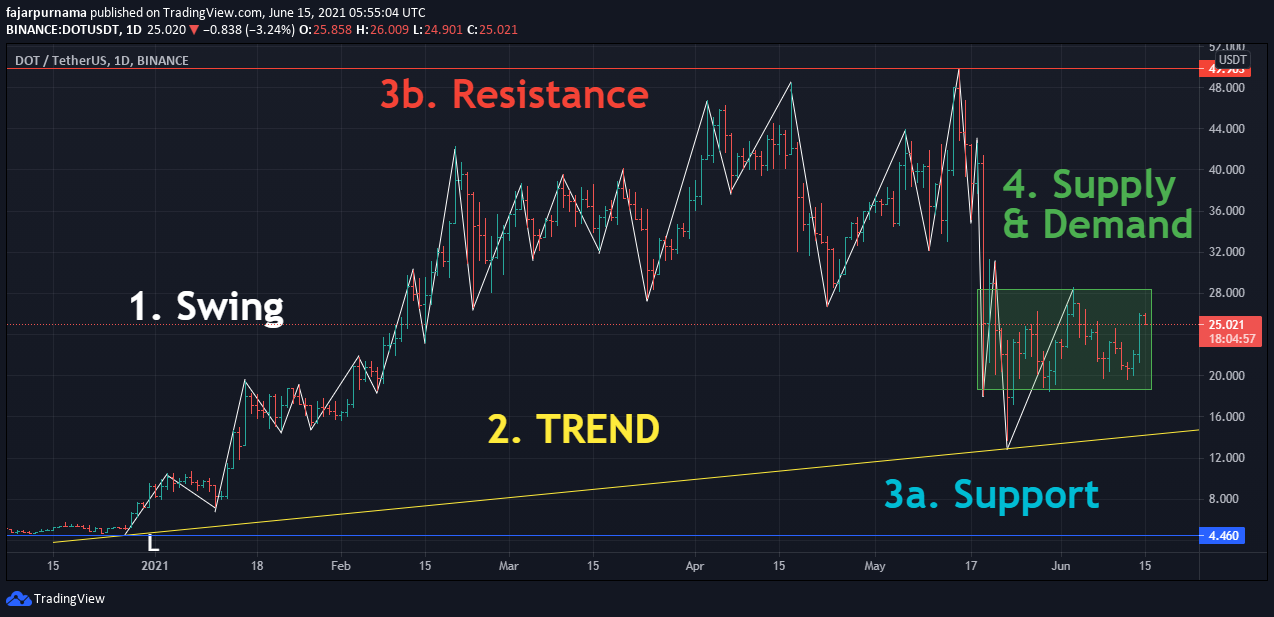
Sebelum pola grafik, bangunlah fondasi yang kuat pada dasar-dasar menggambar swing, tren, support & resistance, dan supply & demand.
❮ ❯Analisis Teknis Keuangan Narasi Kripto Bab 1 Teori DOW

Disini saya akan menulis Teori DOW berdasarkan pengalaman kripto dan kursus analisis teknis dimana saya membayar menggunakan keuntungan saya.
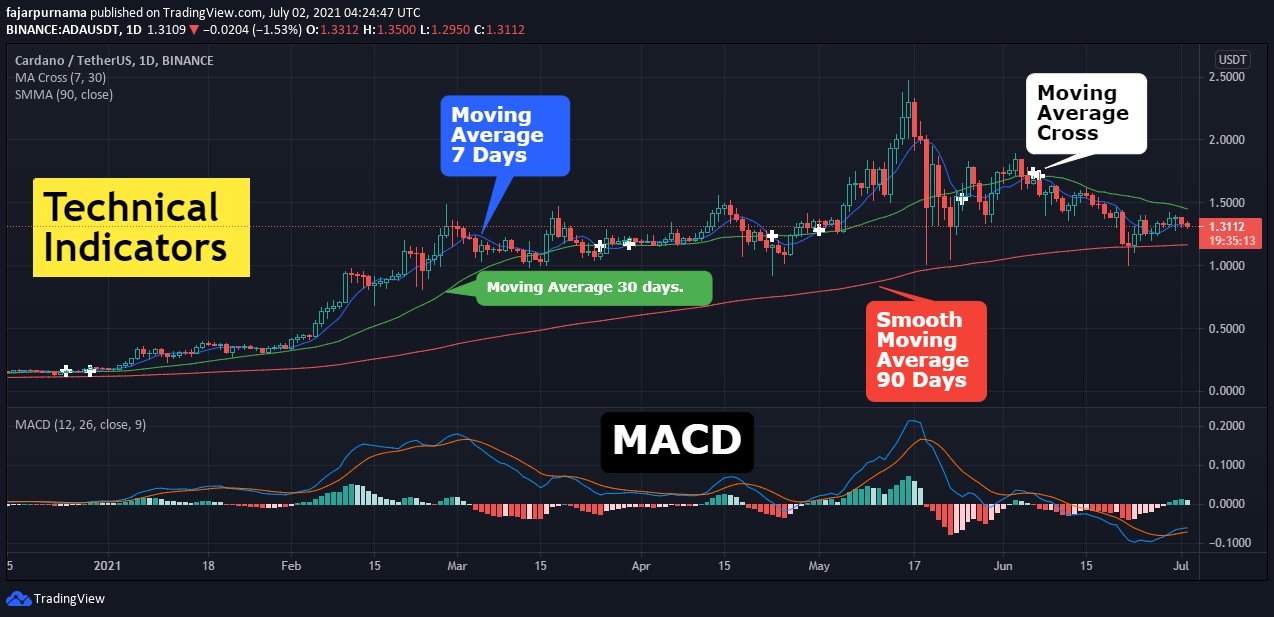
❮ ❯Financial Technical Analysis Crypto Narrative Chapter 4 Indicators

Technical indicators are mathematical calculations of historical trading data which helps traders in making better trading decision.
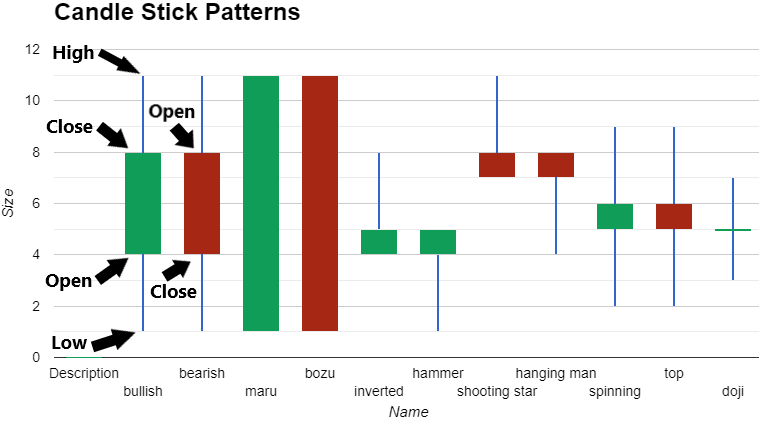
❮ ❯Financial Technical Analysis Crypto Narrative Chapter 3 Candle Stick Patterns

All the candles here are found in cryptocurrency charts which means that even candle patterns can be used in crypto trading and investing.
❮ ❯Financial Technical Analysis Crypto Narrative Chapter 2 Basic Drawings

Before the chart patterns, build a solid foundation on the basics of drawing swings, trends, supports & resistances, and supplies & demands.
❮ ❯Financial Technical Analysis Crypto Narrative Chapter 1 DOW Theory

Here I will write the DOW Theory based on my crypto experience and financial technical analysis course where I paid using my crypto profits.
❮ ❯My Blogger Income May 2021 End of The Previous Bull Market but More Newcomers

All my peers in college, I can count using my fingers who actually know about crypto. How will the price be if crypto becomes main stream?
❮ ❯How User Friendly Zilliqa DeFi Ecosystem is Today?

Zilliqa the first smart contract platform to implement Sharding protocol in 2017 which is a method for processing transactions in parallel.
❮ ❯How User Friendly Terra Luna DeFi Ecosystem is Today?

Terra Luna will strive to become the decentralized finance of tokenize real world assets but how user friendly is its DeFi ecosystem today?
❮ ❯How User Friendly Solana DeFi Ecosystem is Today?

Many users already know that Solana can run fifty thousands smart contracts per second but how user friendly is Solana DeFi ecosystem today?
❮ ❯How User Friendly Polygon (Matic) DeFi Ecosystem is Today?

Coinbase wallet supports Polygon and crypto.com supports its deposit and withdrawal, many for portfolio generator, and many trading tools.
❮ ❯How User Friendly Binance Smart Chain DeFi Ecosystem is Today?

Trust wallet supports BSC and Binance supports its direct deposit and withdrawal, many for portfolio generator, and DEX Guru trading tools.
❮ ❯Now Avalanche C-Chain is as User Friendly as Other DeFi Ecosystem
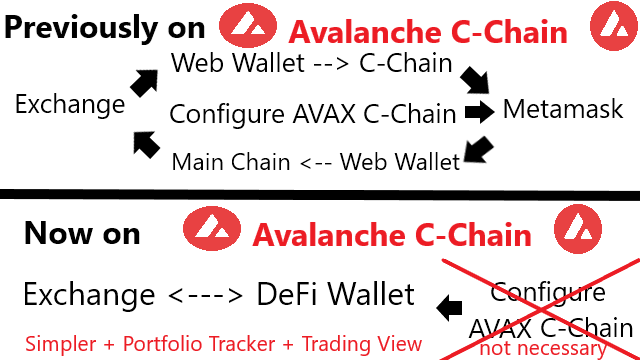
Trust wallet supports AVAX C-Chain, Binance supports direct deposit and withdrawal, Markr for portfolio, and DEX Guru provides trading tools.
❮ ❯Kesalahpahaman tentang Minimum 1 Lot dan Investasi dan Trading Itu Mahal

Pertama kali saya bilang harga Bitcoin kepada generasi lebih tua, tanggapan mereka harganya sangat mahal dan mereka tidak punya Rp 700 juta.
❮ ❯Misconception of The Minimum 1 Lot and The Investing and Trading is Expensive
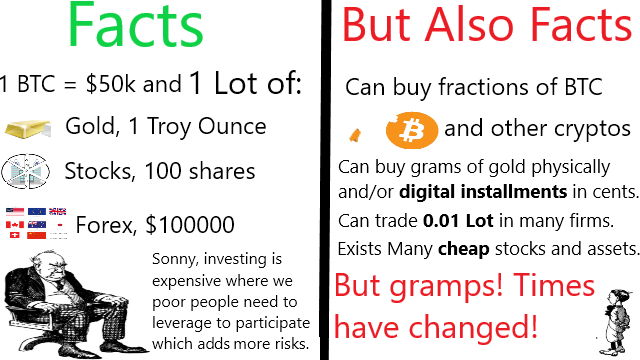
The first time I showed Bitcoin price to older generations their immediate respond was that it is very expensive and they do not have $50000.
❮ ❯Panduan Singkat Kucoin Mobile
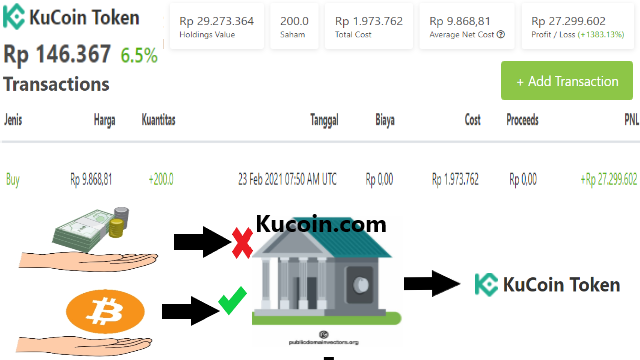
Bitcoin dan Ethereum tersedia di setiap bursa sementara permata tersembunyi seperti Kucoin Share KCS hanya tersedia di bursa Kucoin.
❮ ❯Quick Guide to Kucoin Mobile
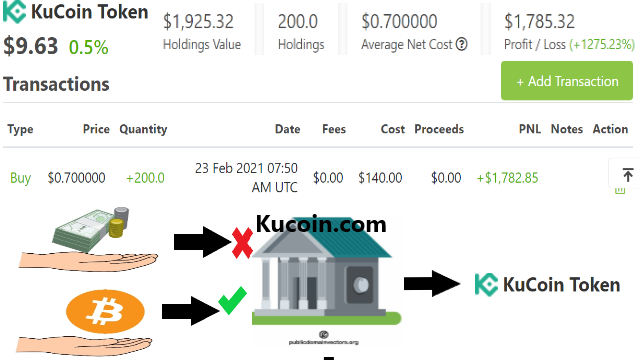
Bitcoin and Ethereum are probably available in every exchange while a hidden gem like Kucoin Share KCS is only available in Kucoin exchange.
❮ ❯Panduan Singkat Tokocrypto Mobile
Ini adalah panduan singkat untuk Tokocrypto bursa mata uang kripto lokal di Indonesia, merupakan salah satu kebutuhan untuk memulai kripto.
❮ ❯Quick Guide to Tokocrypto Mobile
This is a quick guide to Tokocrypto a local cryptocurrency exchange in Indonesia which can be one of the necessities to begin in crypto.
❮ ❯Panduan Singkat Trust Wallet Mobile

Panduan singkat untuk Trust Wallet dompet mata uang kripto pribadi non-kustodian, merupakan salah satu kebutuhan untuk memulai dalam kripto.
❮ ❯Quick Guide to Trust Wallet Mobile

This is a quick guide to Trust Wallet a personal and non-custodial cryptocurrency wallet which is one of the necessities to begin in crypto.
❮ ❯Panduan Singkat Coingecko Mobile
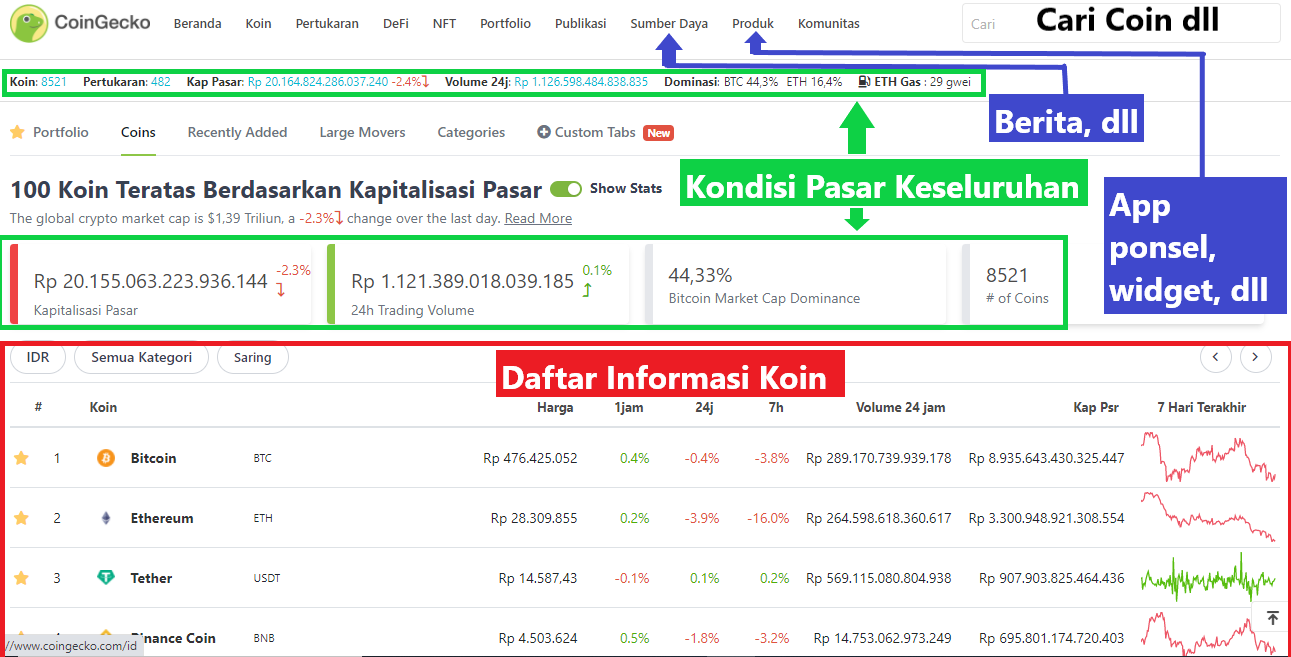
Merupakan panduan singkat untuk coingecko mobile, salah satu sumber informasi mata uang kripto yang dibutuhkan untuk memulai dalam kripto.
❮ ❯Quick Guide to Coingecko Mobile
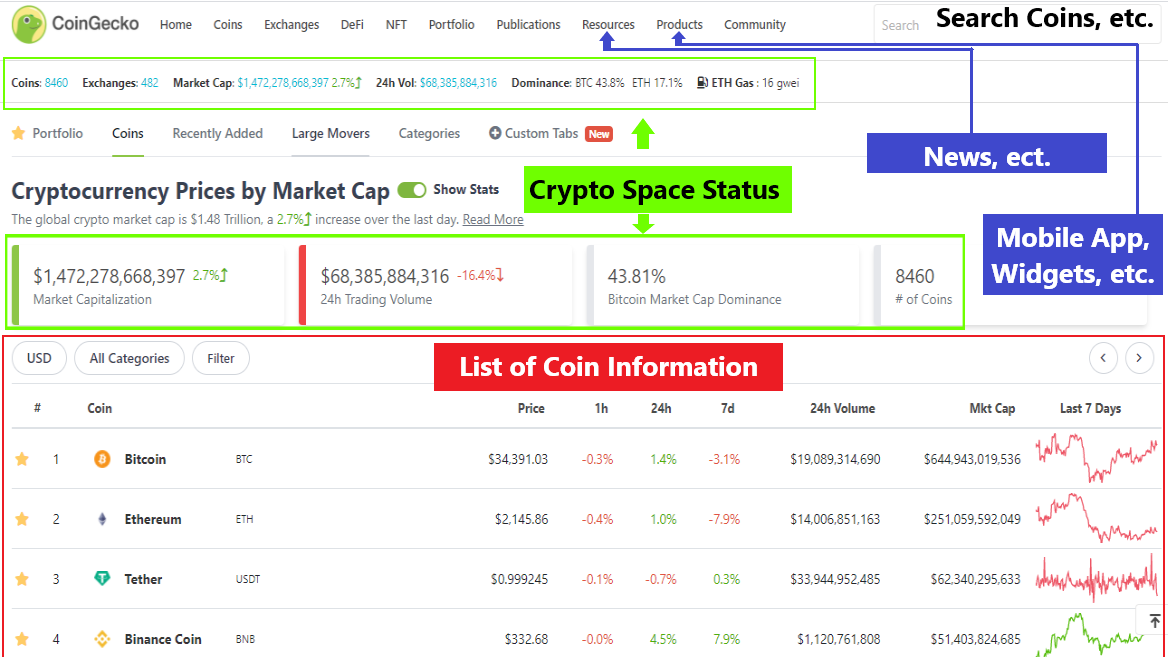
This is a quick guide to coingecko mobile, one of the sources of cryptocurrency information, one of the necessities to begin in crypto.
❮ ❯Panduan Singkat Mata Uang Kripto untuk Pengguna Baru
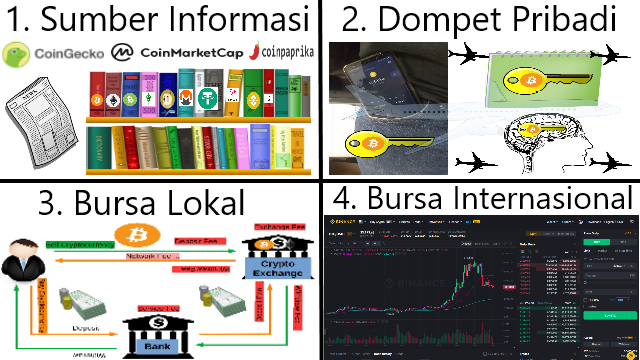
Hal-hal penting untuk mulai menggunakan mata uang kripto adalah sumber informasi, dompet pribadi, bursa lokal, dan internasional.
❮ ❯Quick Guide to Cryptocurrency for New Users
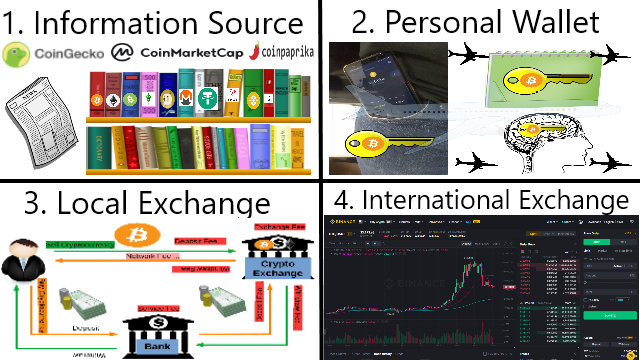
The quick essentials to start using cryptocurrency are information sources, personal wallets, local exchanges, and international exchanges.
❮ ❯My Blogger Income April 2021 Less Blogging Chasing The Bull Market
April was the middle of the bull market and I decided to stop blogging and chase the profits through gem hunting.
❮ ❯Why Harvest Finance is Better even though Binance Smart Chain Low Fees

In Binance Smart Chain, Harvest Finance saves around a hundred dollar assuming auto compounding everyday, then how much saved on Ethereum?
❮ ❯Flano Swap Potentially The First to Lead DeFi on Cardano
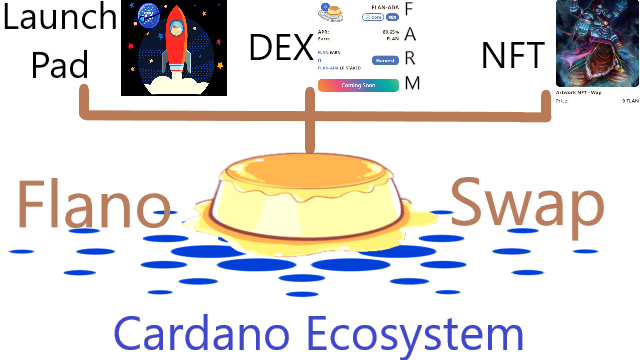
Flano Swap can potentially be the first and leading AMM DEX with Yield Farming, ADA Launchpad, and NFT Market Place on Cardano blockchain.
❮ ❯Binance Smart Chain and Yield Farming Portfolio Tools Early 2021

While in Ethereum there are Zerion and Dextools, in Binance Smart Chain there are Ape Board Finance, Yield Watch, Poo Coin, and JDI Yield.
❮ ❯List of Yield Farming Craziness DEX on BSC Early 2021

On average there is one DEX on each chain (AVAX, MATIC, NEO, TRX, EOS, TOMO, NRG, IOST, QTUM, SOL, ZIL) while BSC have crazy amount of DEXs.
❮ ❯Low Risk Yield Farming Using Fiat Stable Coins Early 2021
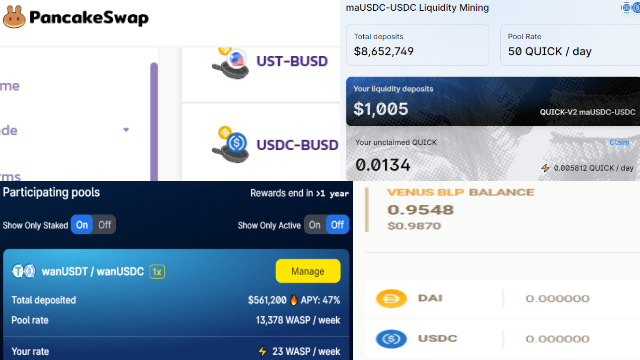
While yield farming using cryptocurrency coins are attractive it is susceptible to price devaluation but farming using stable coin does not.
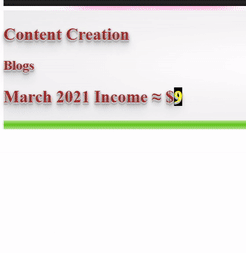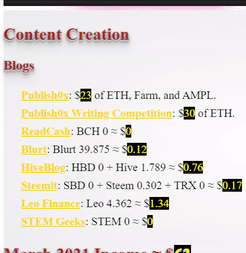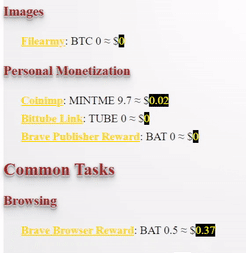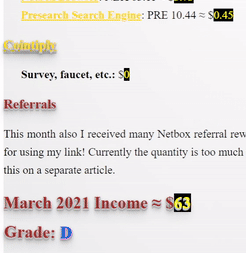
❮ ❯My Blogger Income March 2021 New Profession
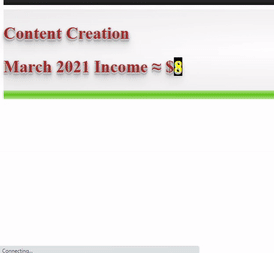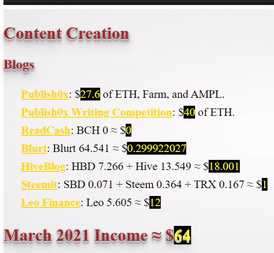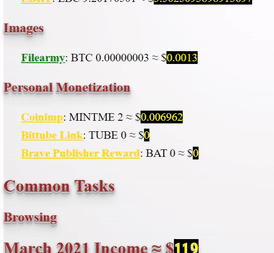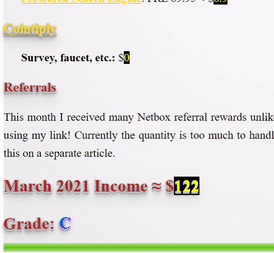
This month I have made my determination to charge through the walls despite not reaching my goal which was to win 1000 months worth salary.
❮ ❯Presearch to be Decentralized Search Engine for New Users and Investors
Presearch is transparent because it is built on the blockchain with the future vision to be driven by the community and respect our privacy.
❮ ❯List of Decentralized Exchanges that Emerged in Early 2021 Outside of Ethereum with Affordable Fees

Other than Ethereum there are Binance Smart Chain, Tron, Tomo Chain, Polygon, Neo, Zilliqa, Solana, Avalanche, Energi, QTUM, OKEX, Cosmos...
❮ ❯My Blogger Income February 2021 Busy and Missed Out
The bull market started when I was recruited for the current project, busy that I even missed the news of Elon Musk in Bitcoin and Dogecoin.
❮ ❯My Story About Upland Earth Metaverse on EOS Blockchain for New Players
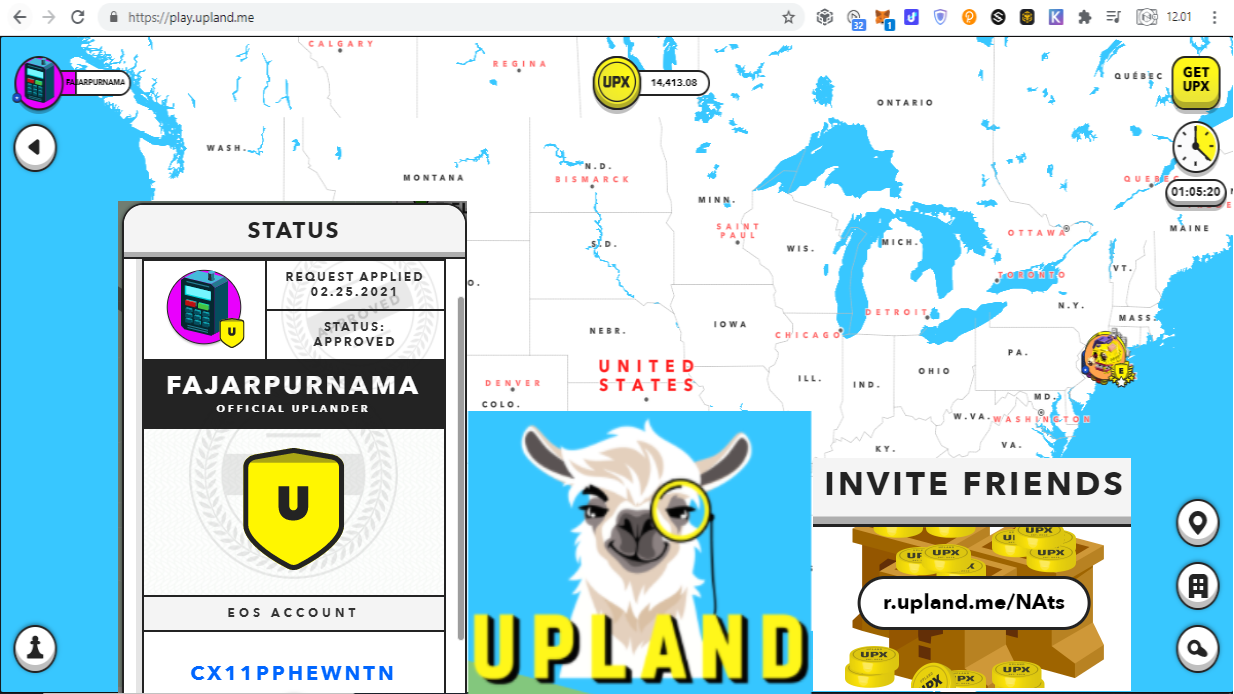
Upland is a decentralized application (dapp) currently on the EOS blockchain and all our assets are recorded on chain proving our ownership.
❮ ❯Torum Media Sosial Kripto Situs Mobile Tayang
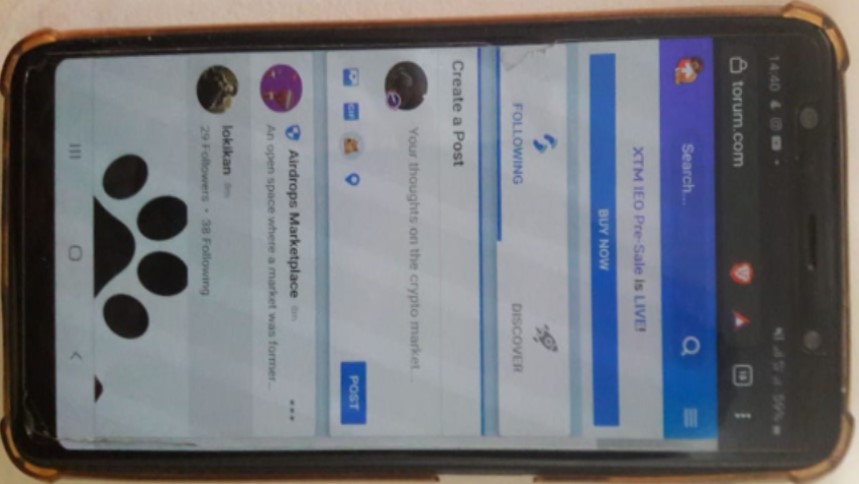
Sebelumnya kami tidak bisa mengakses Torum menggunakan mode mobile dan harus pindah ke mode desktop, akhirnya mereka merilis website mobile.
❮ ❯Torum Crypto Social Media Mobile Website Live
Previously, we cannot access Torum using mobile mode and have to switch to desktop mode everytime, they finally released the mobile website.
❮ ❯Paid IEEE Membership With Bitcoin Through Vandle Cryptoable Prepaid Visa Card

Good thing I applied for and got a Visa Card during my time in Japan that can be topped up with cryptocurrency to pay for IEEE membership.
❮ ❯Should We Farm? My Yield Farming Theoretical Calculation Opinion

Other than the fees and the APY, it really depends on the future value both assets and harvests. To Farm, not farm, or just buy the harvest.
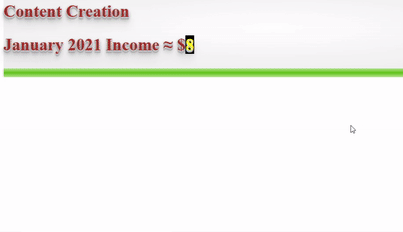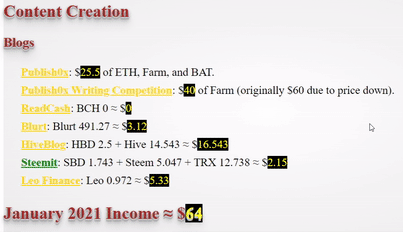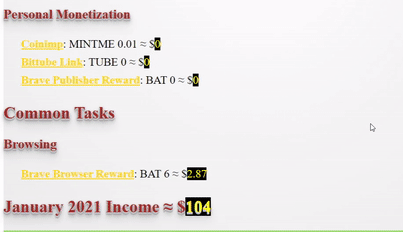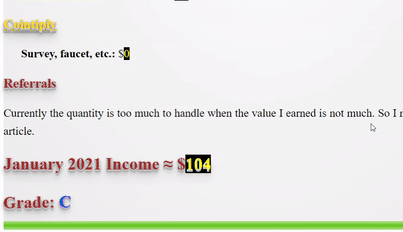
❮ ❯My Blogger Income January 2021 Being Lazy but Unexpected

I made $89 by crypto blogging which was unexpected because I was slacking off after new year and maybe because cryptocurrency price increase
❮ ❯Mendukung Media Sosial Kripto Torum Seperti Duta Besar dengan Menanggapi Posting Terkait Lainnya
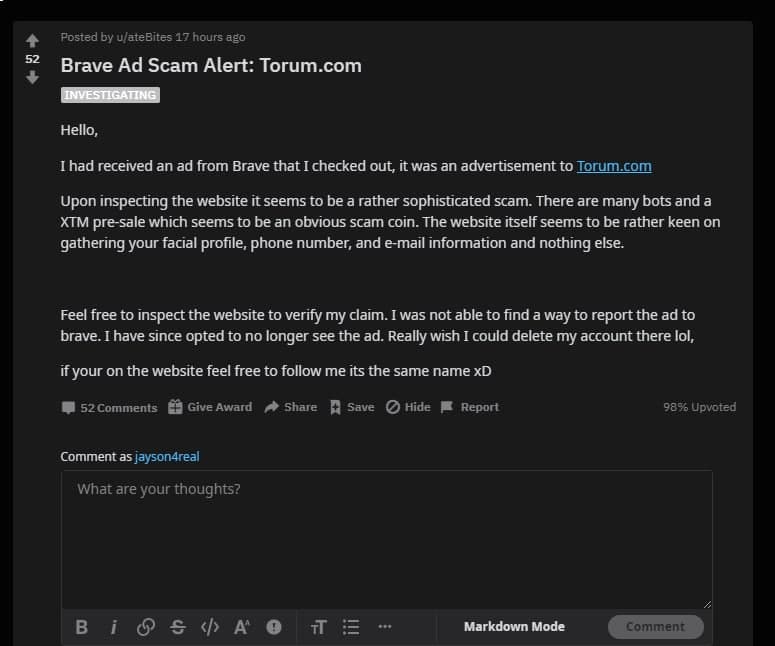
Saya tahu empat pendekatan yaitu sebagai pendukung, sebagai pihak ketiga yang objektif, sebagai penjahat ketiga, dan sebagai pelapor.
❮ ❯Supporting Crypto Social Media Torum Like an Ambassador by Responding to Others Related Posts
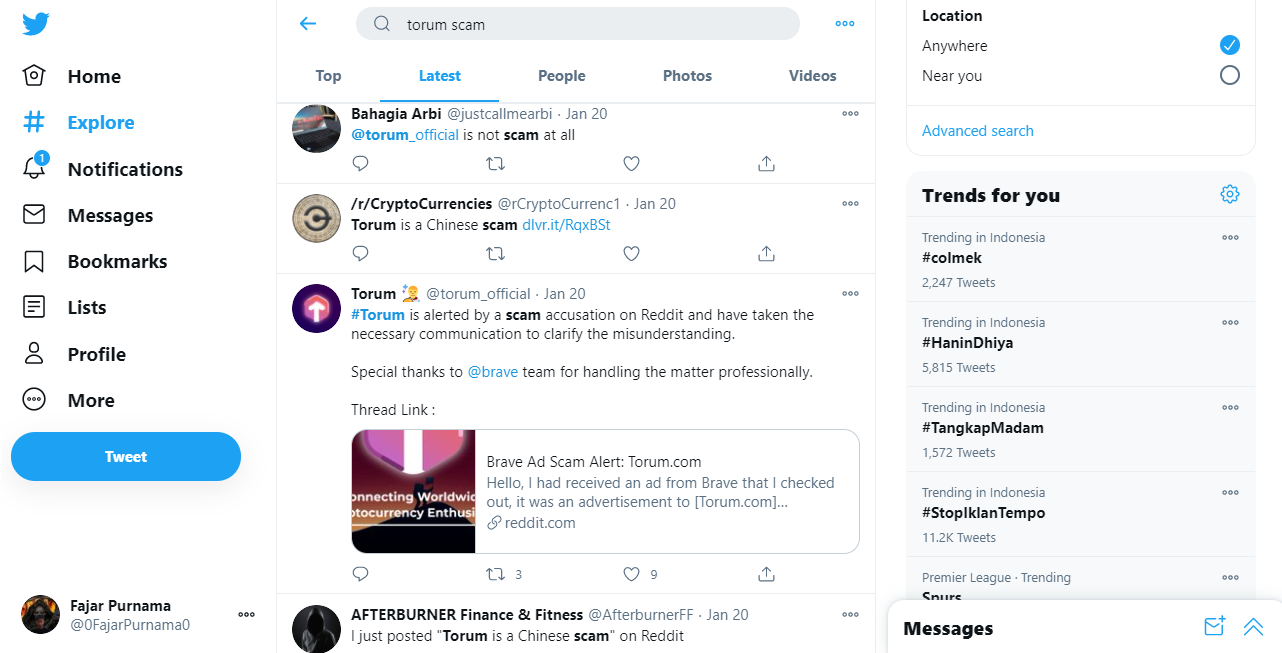
I know four approaches which are as a supporter up to an evangelist, as an objective 3rd party, as a 3rd party villain, and as an informer.
❮ ❯Bagaimana Mendukung Crypto Social Media Torum di Platform Lain
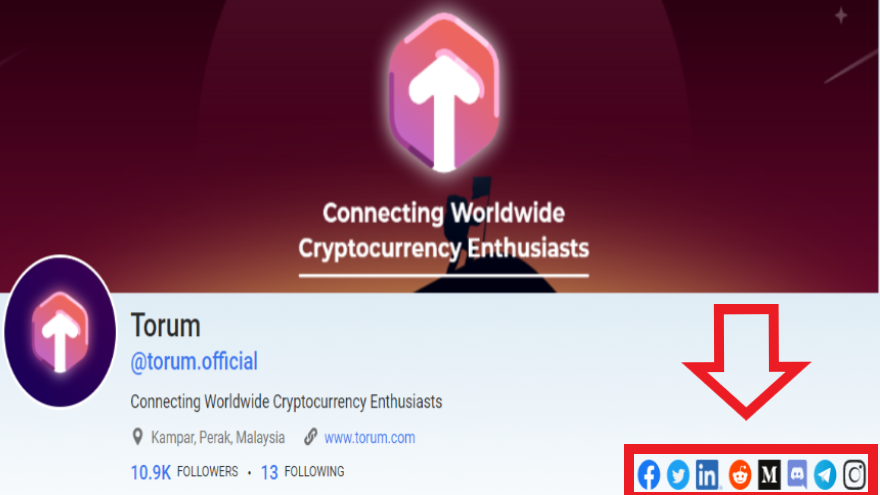
Dengan mendukung akun mereka yang lain akan meningkatkan kehadiran mereka di platform lain, dan akan menarik lebih banyak pengguna ke Torum.
❮ ❯How to Support Crypto Social Media Torum on Other Platforms
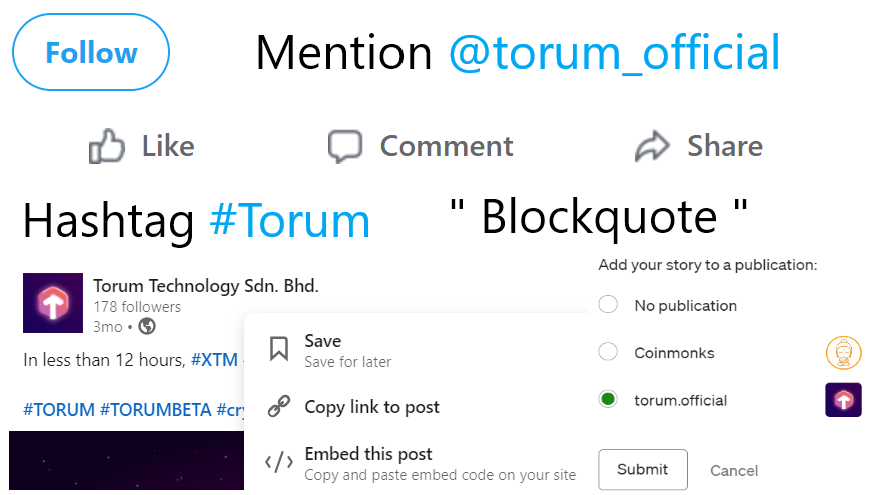
By supporting their other accounts will increase their presence on other platforms and thus attracting more users to Torum and help it grow.
❮ ❯Hubungan komunitas krypto lebih dekat dengan klan dan perusahaan di Torum tetapi apa yang terlewatkan?

Meskipun fitur klan dan perusahaan di Torum menyatukan komunitas kripto, masalahnya adalah kurangnya tokoh terkenal dan peniruan identitas.
❮ ❯Crypto community closer relationship with clan and company in Torum but what are they missing?
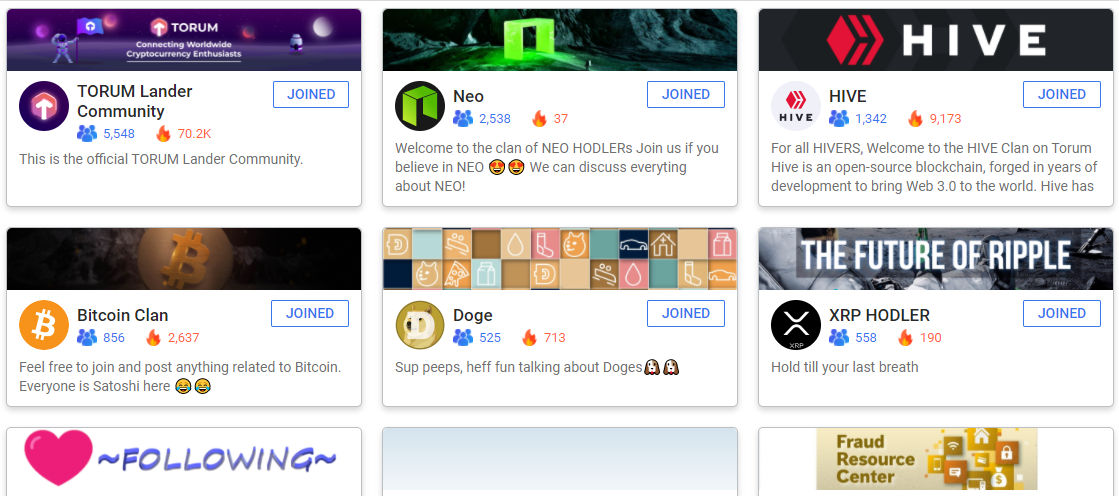
While clan and company feature in Torum attracts crypto communities together but the problem is lack of famous figures and impersonations.
❮ ❯Grandma is shocked by the multiplying Ampleforth and shocked again by the missing Ampleforth
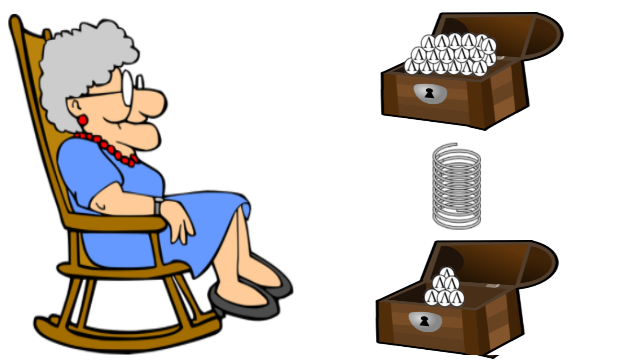
If the price is above $1 then more people demands more coins. If the price is below $1 then there is too much coins and less people demands.
❮ ❯My End of Year 2020 Cryptocurrency Investment Report
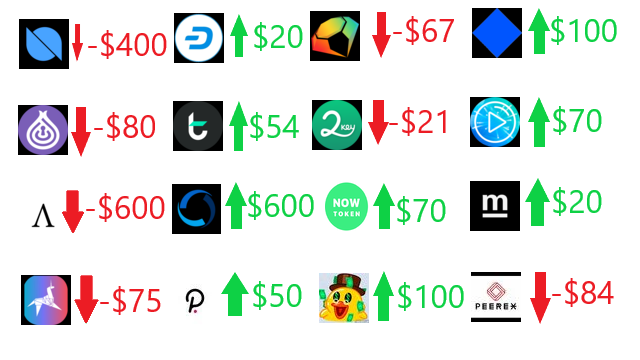
I lost almost $1000 in 2019 but survived in 2020. I learned that I should invest small so that I can grab more opportunity in the future.
❮ ❯My End of Year 2020 Blogging Income Report
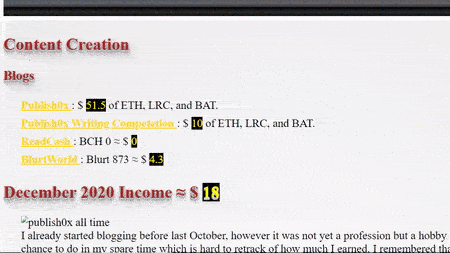
I made $88 by crypto blogging this month with total $771 this year, most of my urgent personal mission had finished but hope I can continue.
❮ ❯Tema dan NFT Hadiah kripto Torum
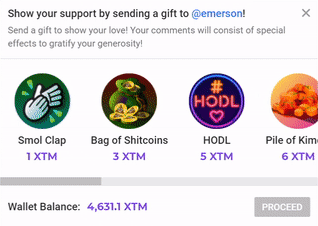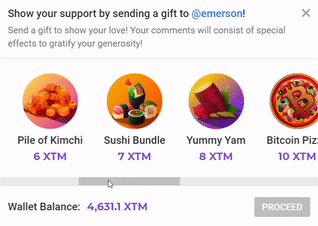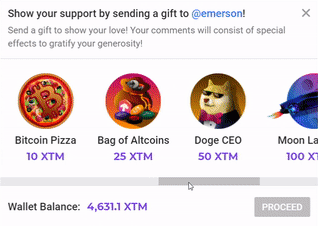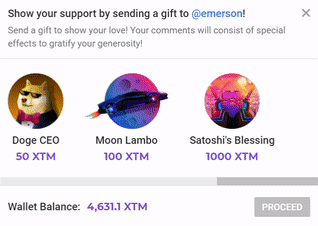
Hanya memberi XTM membosankan, lebih asyik memberikan kartu hadiah artistik dan akhirnya kartu hadiah memiliki beberapa utilitas dengan NFT.
❮ ❯Torum's Crypto Gift Themes and NFTs
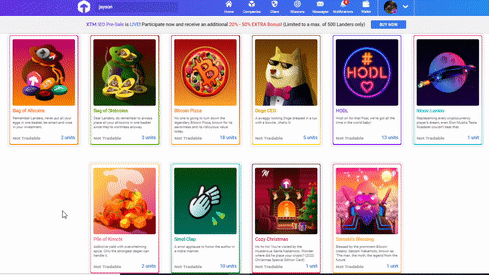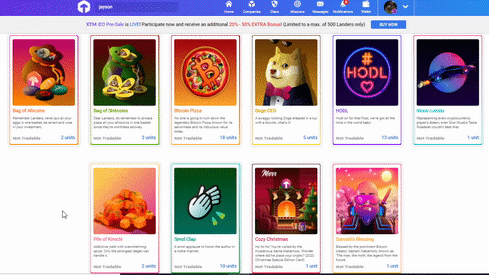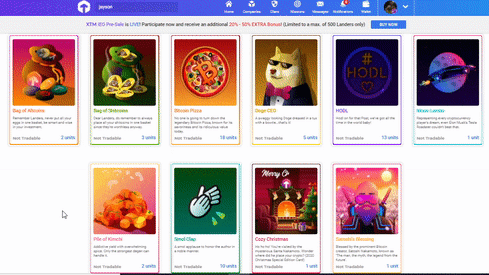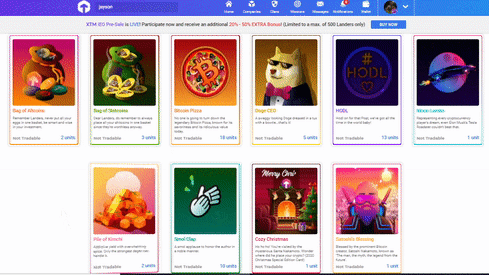
Instead gifting the boring x amount of XTM, we give artistic gift cards and finally they have some utilities where NFTs of them are made.
❮ ❯Permintaan Awal Saya Tentang Media Sosial Kripto Torum
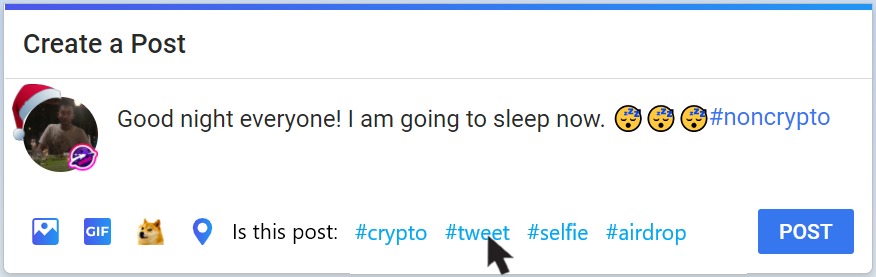
Lima tuntutan saya adalah penyortiran pos, pengategorian pemberitahuan, peniti utas, preferensi tanda pagar, dan pengingat tanda pagar wajib
❮ ❯My Early Demands on Torum Crypto Social Media
My five demands are post sorting, notification categorizing, thread pinning, hashtag and sorting preference, and hashtag must use reminder.
❮ ❯Torum juga dibombardir oleh spam tetapi mengapa kita tidak perlu khawatir untuk saat ini.
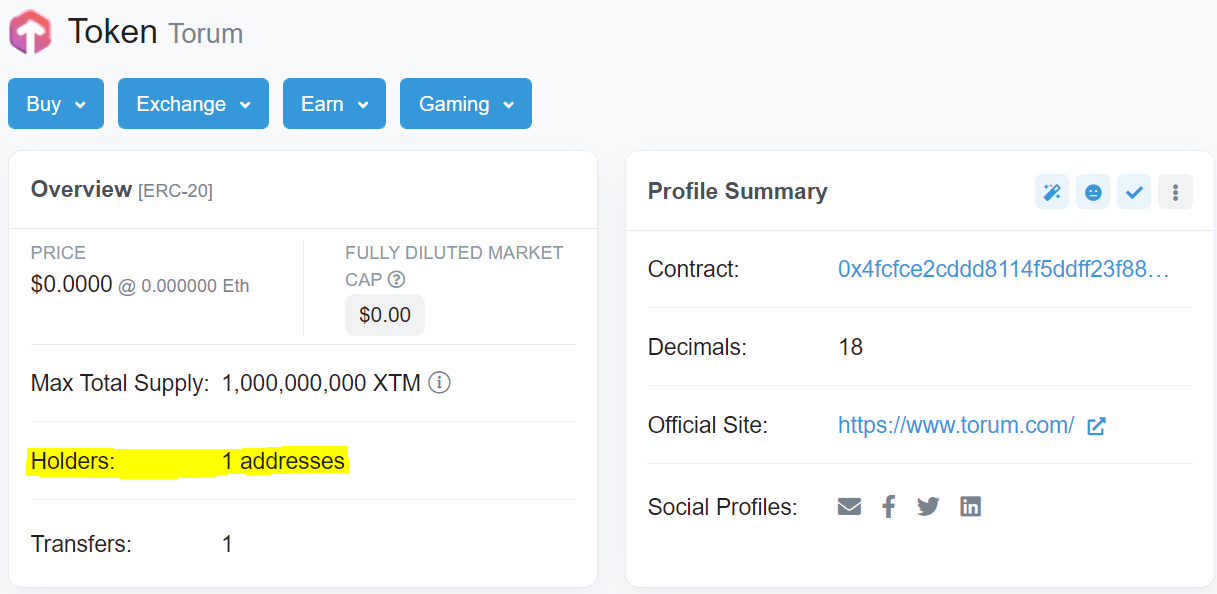
Hampir semua spammer mencuri XTM untuk dijual, jadi apresiasi harga turun tetapi jangan khawatir untuk saat ini.
❮ ❯Torum also got bombarded by spams but why you should not worry for now.
Almost all spammers steals XTM to sell, so the price appreciation drops but do not worry for now as none of these can happen now.
❮ ❯About RFND Investment and the first SLP token I knew
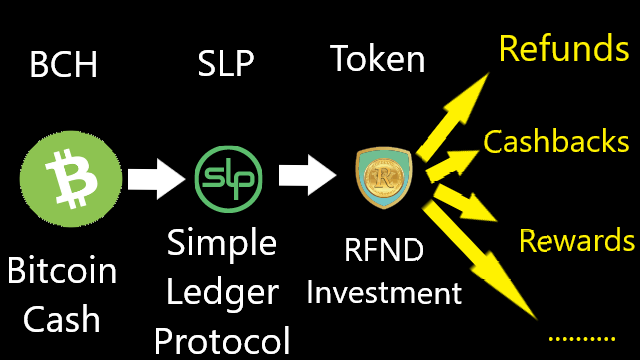
The chronological order to understand $RFND is to learn Bitcoin Cash, Simple Ledger Protocol, the token's past events, finally light paper.
❮ ❯Bityard Cryptocurrency Contract Exchange Mobile Friendly Website Exploration

These are not screenshots of their mobile application but screenshots of their mobile friendly website on the browser to enjoy copy trading.
❮ ❯Mata Uang Kripto 101 untuk Pengguna BAB 5 Gerbang ke Pasar Bebas

Anda bisa jadi memilih untuk tidak membeli karena berbagai alasan. Bab ini menyajikan metode lain untuk mendapatkan mata uang kripto.
❮ ❯Cryptocurrency 101 for Users Chapter 5 Gate to The Free Market

The two default way to get cryptocurrency is to mine and to buy. However, you may chose not to buy for various of reasons. This chapter presents other methods of getting cryptocurrency.
❮ ❯Send Your ETH to Smart Contract to Convert to ETH 2.0 (Is this a scam?! BEWARE!!)
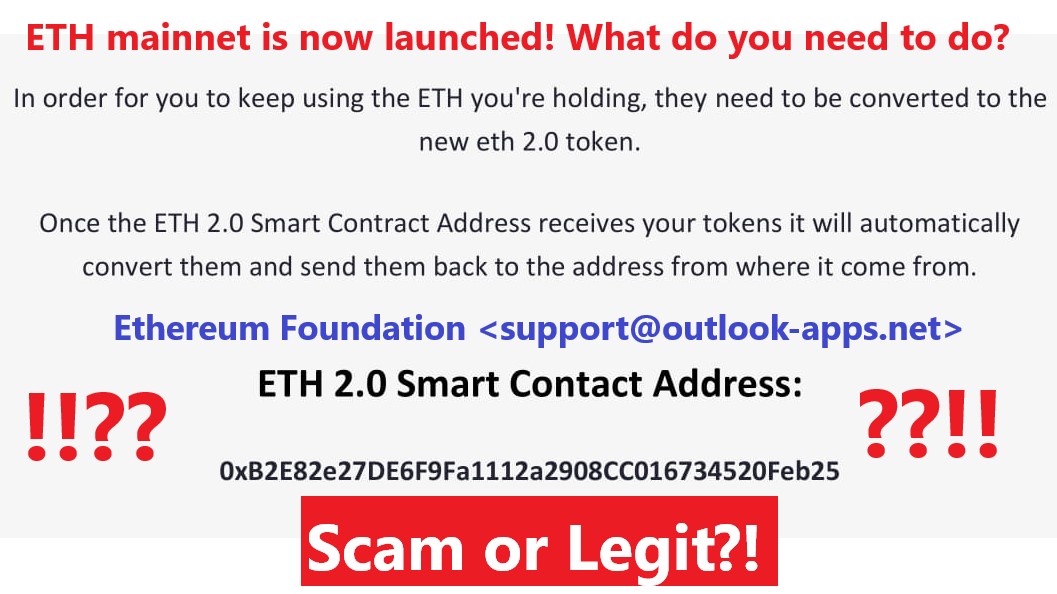
ETH users are asked to sent to a claimed to be a smart contract address to convert to ETH 2.0 while most transactions are irreversible which could be a scam.
❮ ❯Pengingat untuk tidak Melampaui Harapan Kebebasan di Torum

Selain dari segi layanan, tim dan kantor pusatnya diketahui yang bisa menjadi sasaran regulator, sehingga tidak bisa seenaknya.
❮ ❯Reminder to not Exceed your Freedom Expectation in Torum
Other than its terms of services, the team and headquarter are known which can be targeted by regulators, thus you cannot expect total freedom.
❮ ❯Tim & Kantor Pusat dan Siapa yang Harus Diikuti di Torum
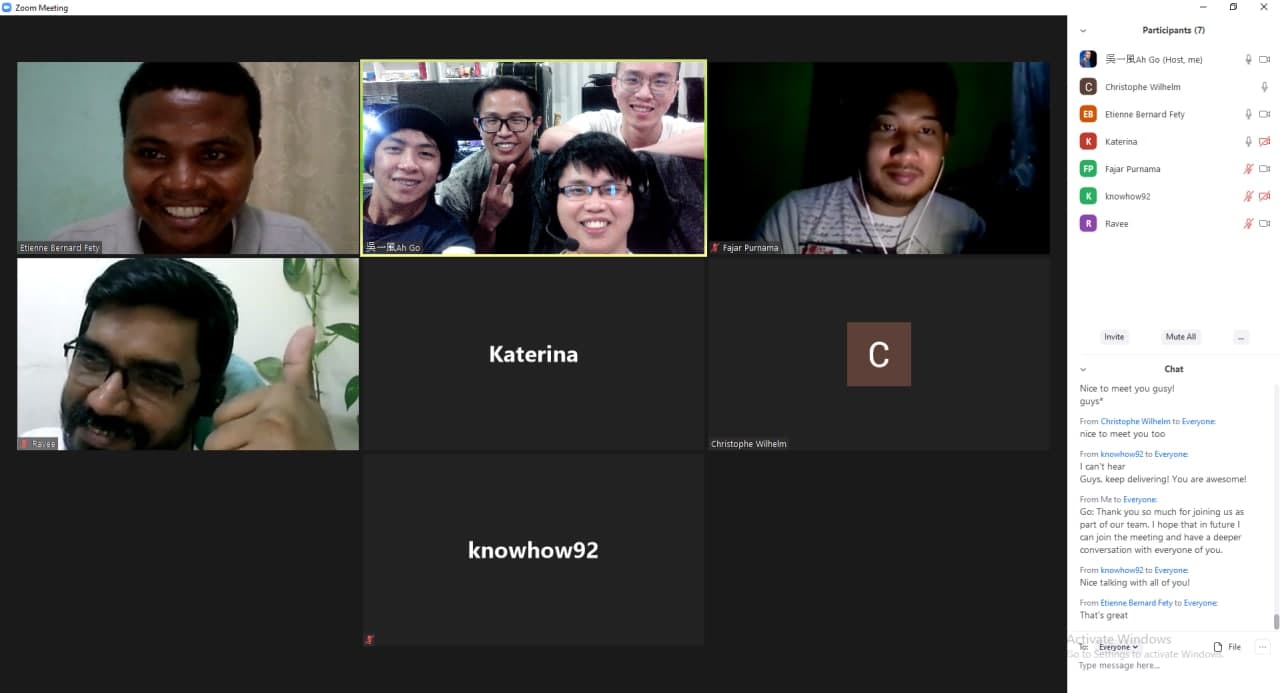
Dimana kantor pusat Torum? Berita eksklusif tidak ditulis di situs web dan whitepaper mereka. Siapa tim dan siapa yang harus diikuti?
❮ ❯The Team & Headquarter and Who to Follow on Torum
Where is Torum's headquarter? Exclusive news not currently written on their website and whitepaper. Who are the teams and who to follow?
❮ ❯This is my Story and Lesson about my First Big Wreck in Trading Ampleforth
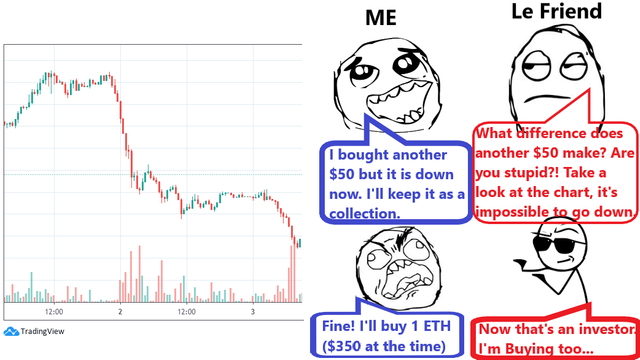
The story is I loss $600 trading AMPL and the lesson learned to always make my own decision and never invest more than I can afford to lose.
❮ ❯My Blogger Income November 2020 and Personal Missions
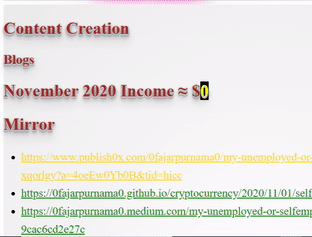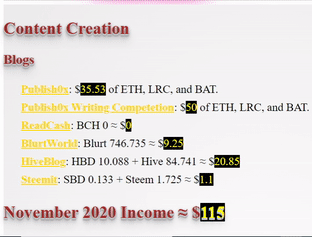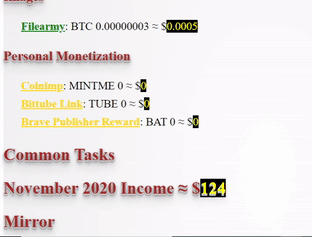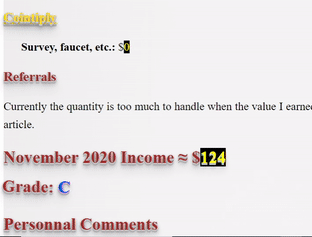
I made $126 by crypto blogging and I have personal missions to accomplish before I am willing to let go of this job.
❮ ❯Torum Menuju Gamifikasi Ekosistem Media Sosial Kripto
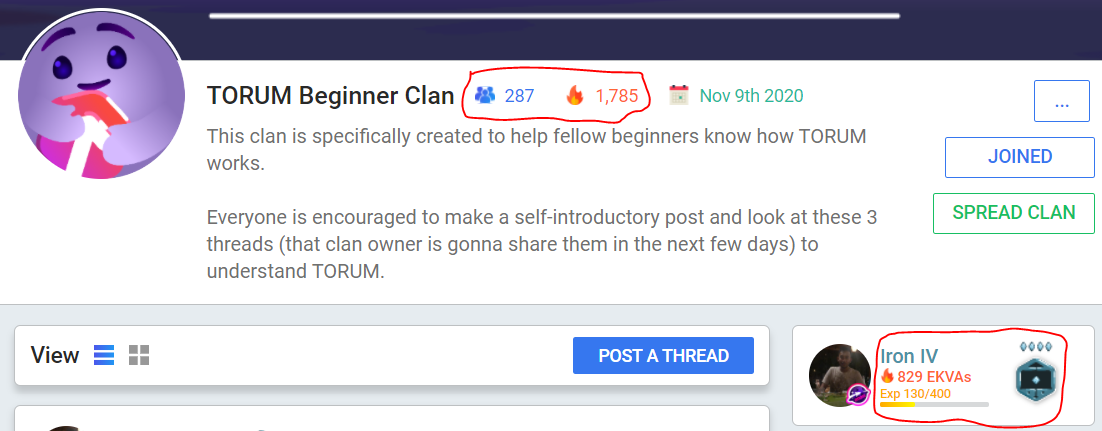
Sebelumnya, saya menulis tentang hadiah misi dan sekarang tentang referral, tip, klan, dan sistem perusahaan saat ini.
❮ ❯Torum Towards Gamifying The Crypto Social Media Ecosystem

Previously, I wrote about the mission rewards and now is about the current referral, tipping, clan, and company system.
❮ ❯Variasi Misi dapat membuat Media Sosial Kripto Torum Menyenangkan
Platform media sosial kripto Torum menyenangkan melalui gamifikasi. Siapa sih yang tidak menyukai berbagai misi, terutama para gamer?
❮ ❯Various Missions Makes Torum Crypto Social Media Fun
Torum cryto powered social media platform fun through gamification. Who does not love various missions, especially gamers?
❮ ❯The Crops Utilities a Homework for DeFi Farming
What is this yield farming craziness? it is just putting your tokens and get a new token with fancy food names.
❮ ❯My Unemployed or Selfemployed Income as a Blogger October 2020
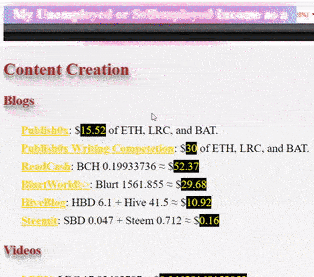
I made $142 by crypto blogging which is enough for a month but if I don't improve, I have to give up due to society pressure and find a job.
❮ ❯Can DEXG Speculative AMM Minimize Price Manipulation and Distribute Ownerships?

Speculative AMM defines price differently. Therefore whales should not be able to pressure the price on DEXG exchange as much as on regular exchanges.
❮ ❯Mata Uang Kripto 101 untuk Pengguna BAB 4 Bagaimana Mendapatkannya Jika Tidak Bisa Membelinya

Anda bisa jadi memilih untuk tidak membeli karena berbagai alasan. Bab ini menyajikan metode lain untuk mendapatkan mata uang kripto.
❮ ❯Cryptocurrency 101 for Users Chapter 4 How to Obtain if You Cannot Buy

The two default way to get cryptocurrency is to mine and to buy. However, you may chose not to buy for various of reasons. This chapter presents other methods of getting cryptocurrency.
❮ ❯Mata Uang Kripto 101 untuk Pengguna BAB 1 Kebebasan Finansial dan Kekayaan
Dengan Bitcoin dan mata uang kripto lainnya, secara regulatori dapat dilarang tetapi secara teknis tidak dapat dihentikan atau disensor, secara teknis tidak dapat disita dimana satu-satunya cara adalah dengan membujuk, menekan, atau menipu pemilik untuk menyerahkan diri.
❮ ❯Cryptocurrency 101 for Users Chapter 1 The Freedom of Finance and Wealth

With Bitcoin and other cryptocurrency, regulatorily can be banned but technically cannot be stopped or censored, technically cannot be confiscated where the only way is to persuade, pressure, or social engineer the owners to hand over themselves.
❮ ❯Mata Uang Kripto 101 untuk Pengguna BAB 2 Memasuki Ruangan

Untuk memasuki ruang mata uang kripto diperlukan media disebut dompet mata uang kripto yang dapat dibawa ke mana saja di dunia.
❮ ❯Cryptocurrency 101 for Users Chapter 2 Entering The Space

To enter the cryptocurrency space, you need a medium that can receive, send, and perform other interactions with those coins. A simple medium is called a cryptocurrency wallet which you can carry to anywhere in the world. The first category division of a wallet is divided into three either custodial, semi-custodial or non-custodial.
❮ ❯Statera's' Twist Deflation and Balancer Loop

For deflation to be attractive, it must occur due to market movement. Like BOMB, Statera burns 1% of each transaction. Now, the question is, how to make people perform more transaction? Ofcourse, the answer is to deliver value. One of the best way to deliver value is to have a product and what product does Statera provides? A balancer, a great product to twist deflation.
❮ ❯ChangeNOW your Crypto with no Registration and Integrate Wigdet on your Website
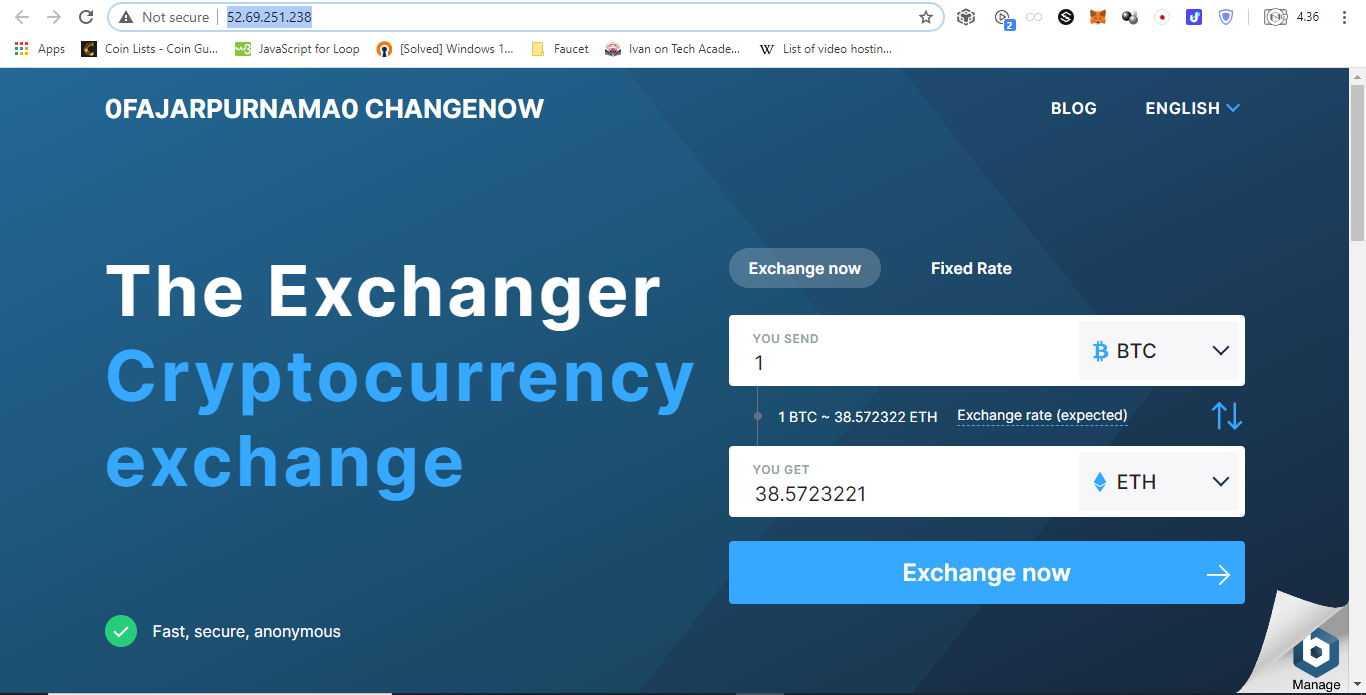
ChangeNOW is one of the platforms that provides widgets for bloggers like me where all you need to do is to paste the code provided on your widget section.
❮ ❯Mata Uang Kripto 101 Untuk Pengguna Bab 3 Koneksi ke Sistem Perbankan Sekarang
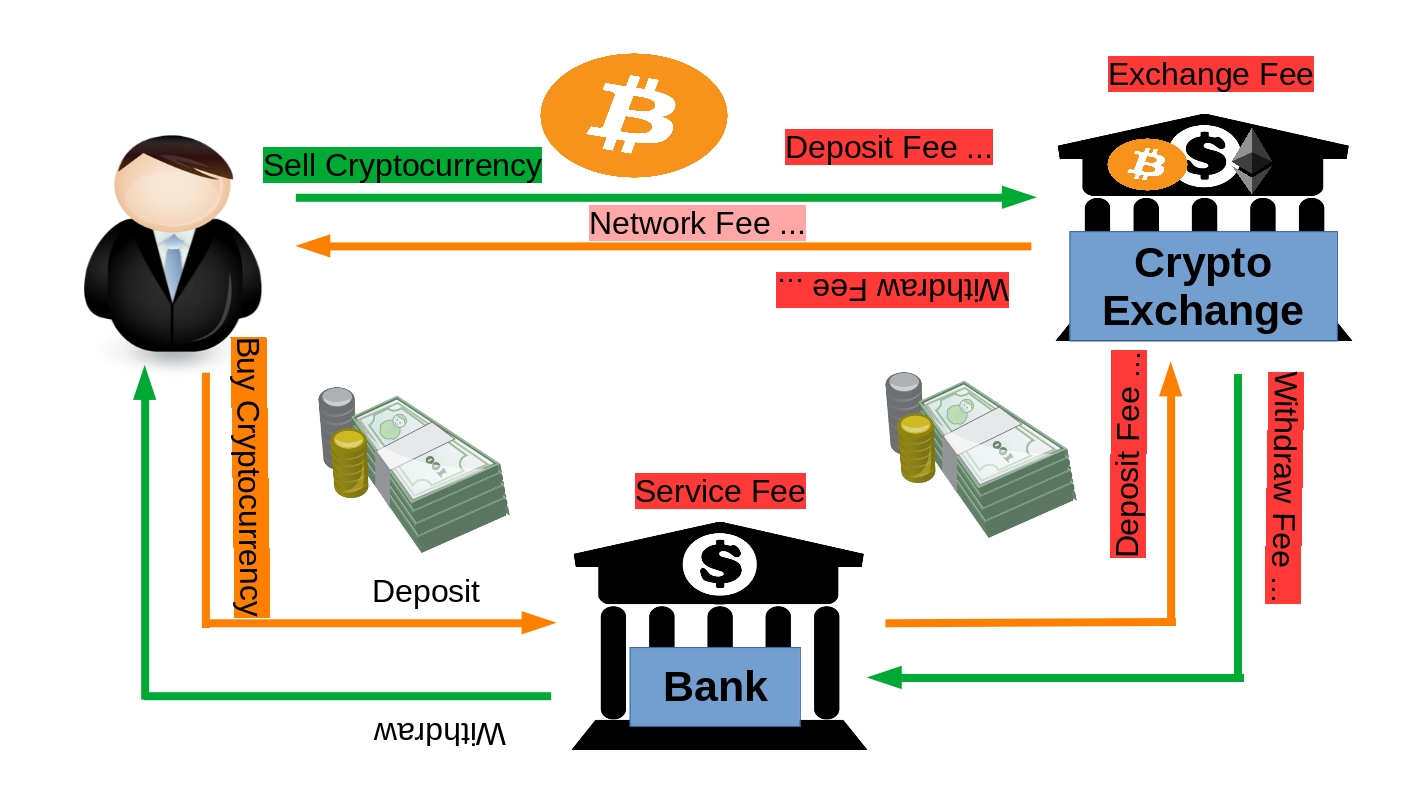
Sekalipun mata uang kripto berpotensi menjadi revolusi di bidang keuangan, itu tetap hanya sebuah potensi. Ini berarti Anda tidak dapat beralih dari sistem fiat tersentralisasi saat ini ke sistem desentralisasi baru seperti menjentikkan sakelar atau mengubah bit dari 0 ke 1 dan sebaliknya. Ini karena era desentralisasi keuangan belum tiba.
❮ ❯Cryptocurrency 101 for Users Chapter 3 Connection to Current Banking System

Eventhough cryptocurrency can potentially be a revolution in finance, is still only a potential. This means that you cannot switch from the current centralized fiat system to the new decentralized system like flicking a switch or changing a bit from 0 to 1 and vice versa. This is because the age of decentralized finance has not yet come.
❮ ❯Essential User Interface Checklist for Atomic Wallet
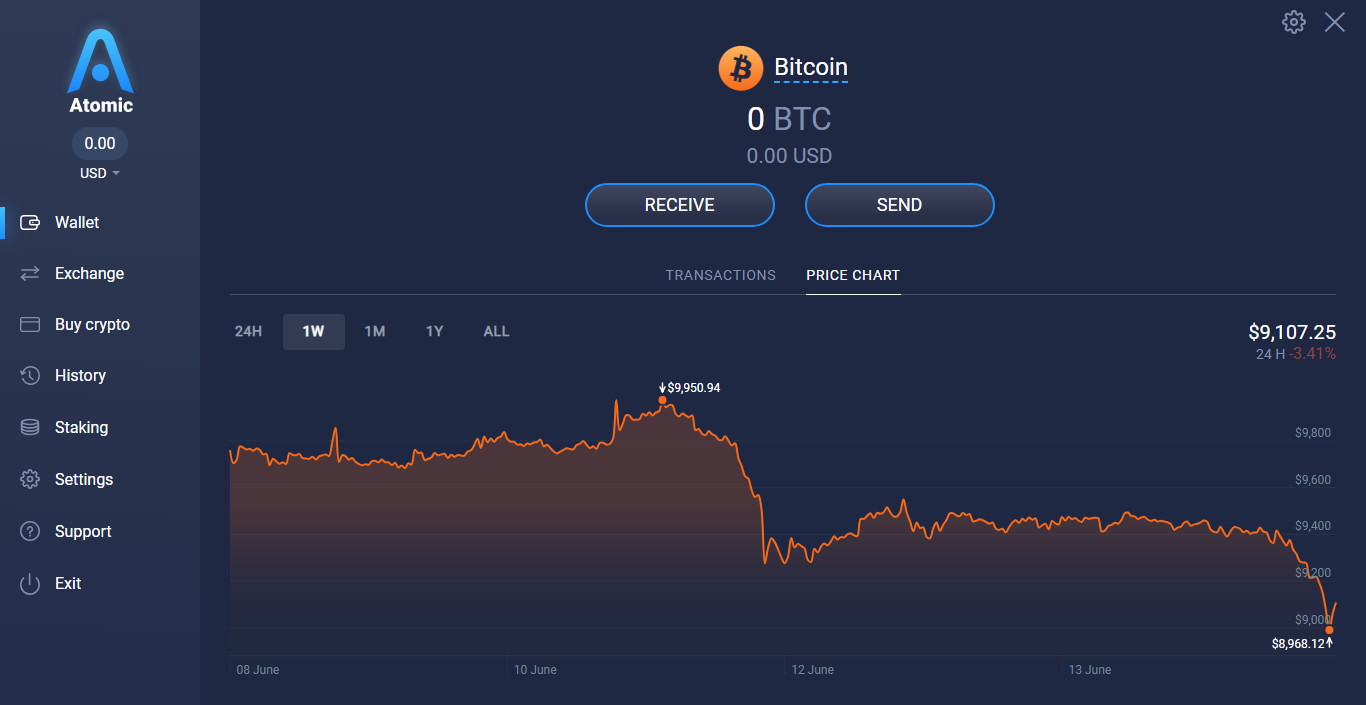
One of my favorite feature is in wallet staking. Atomic wallet allows you to stake while keeping your private keys.
❮ ❯Publish0x Content Platform that Tips both Publishers and Readers in Crypto Tokens

The tipping does not come from your pocket, Publish0x sponsors your tipping and you can get a share of that tipping. In other words, both you the reader and the writer gets paid. Technically, you decide how Publish0x monetize the readers and the writers.
❮ ❯Publish0x Platfom Konten yang Mengasih Token Kripto ke Penulis dan Pembaca

Tipping tidak datang dari saku Anda tetapi Publish0x mensponsori tip Anda dan Anda bisa mendapatkan bagian dari tip itu. Dengan kata lain, Anda sebagai pembaca dan penulis dibayar. Secara teknis, Anda memutuskan bagaimana Publish0x menghasilkan uang dari pembaca dan penulis.
❮ ❯Pengalaman Pertama menggunakan Loopring.io DEX
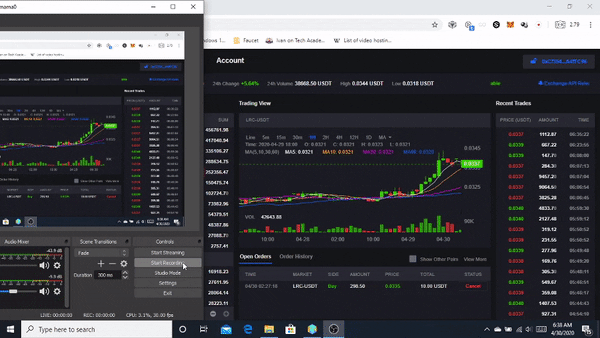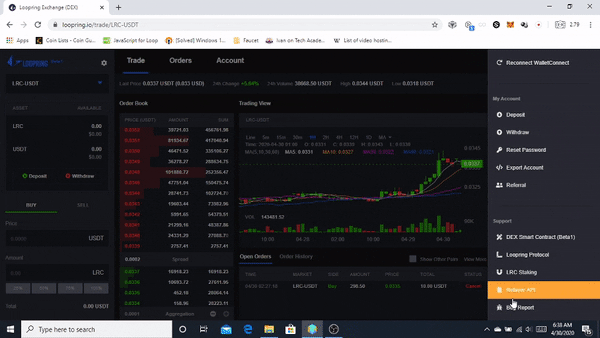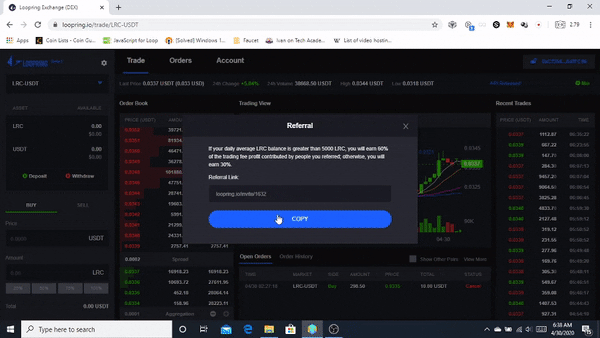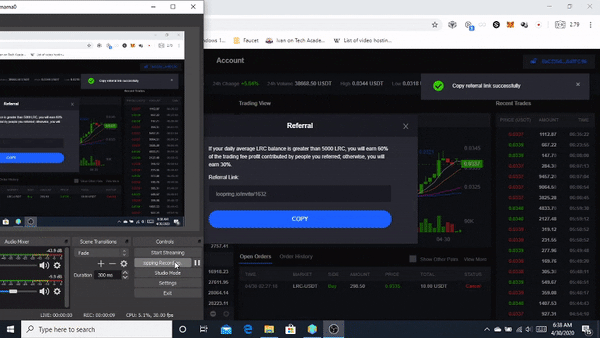
Loopring memungkinkan siapa saja untuk membangun pertukaran berbasiskan throughput, non-penahanan, orderbook di Ethereum dengan memanfaatkan Zero-Knowledge Proofs. Loopring diklaim aman, throughput tinggi, dan biaya rendah.
❮ ❯First Experience using Loopring.io DEX

Loopring allows anyone to build high-throughput, non-custodial, orderbook-based exchanges on Ethereum by leveraging Zero-Knowledge Proofs. Loopring is claimed to be secure, high throughput, and low cost.
❮ ❯Investment Watchlist Desktop Widget
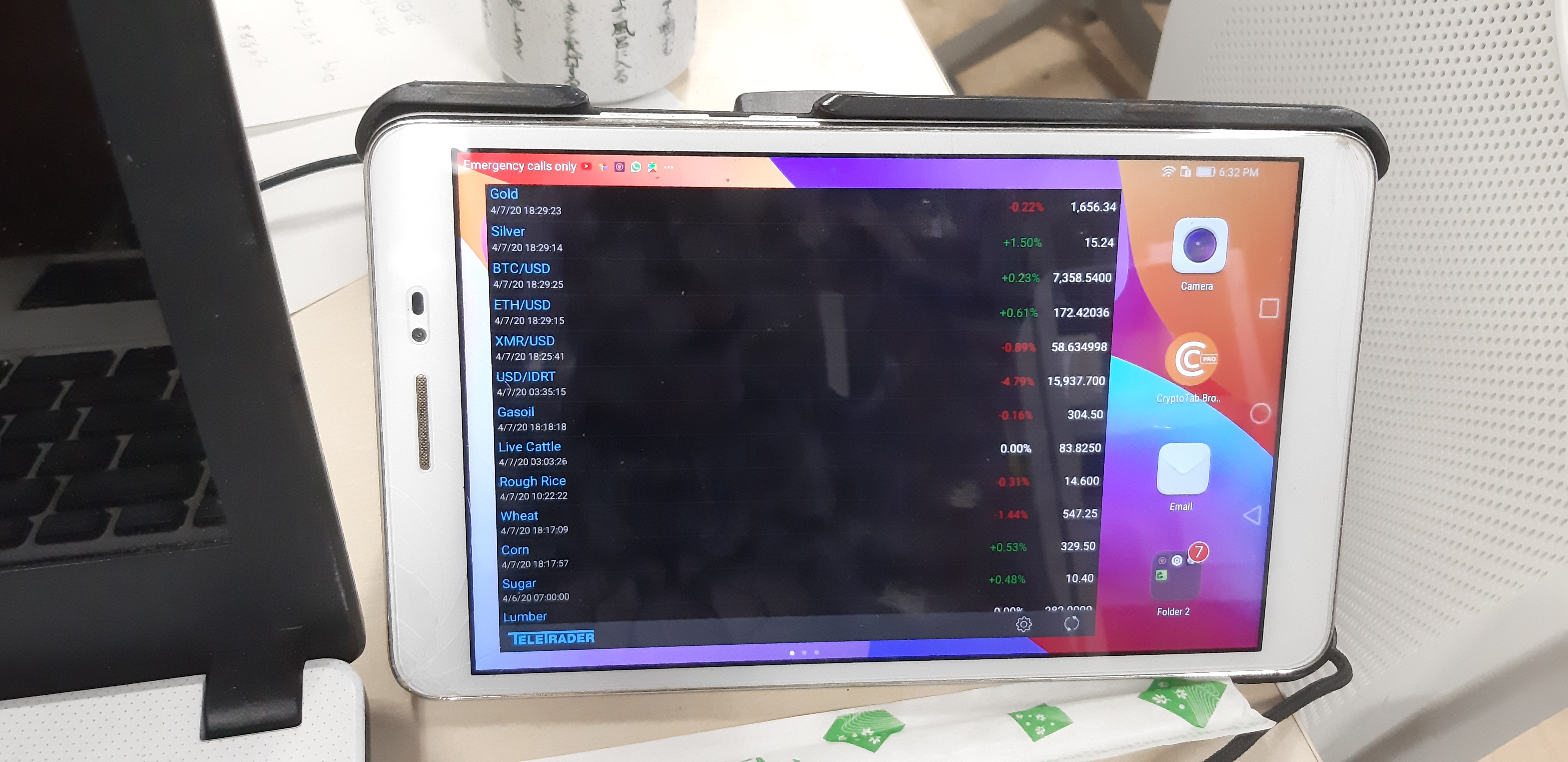
You may find yourselves having frequent urges to see the price. It happened to me, and I felt like wasted a lot of time and energy doing so.
❮ ❯Desktop Widget Pantauan
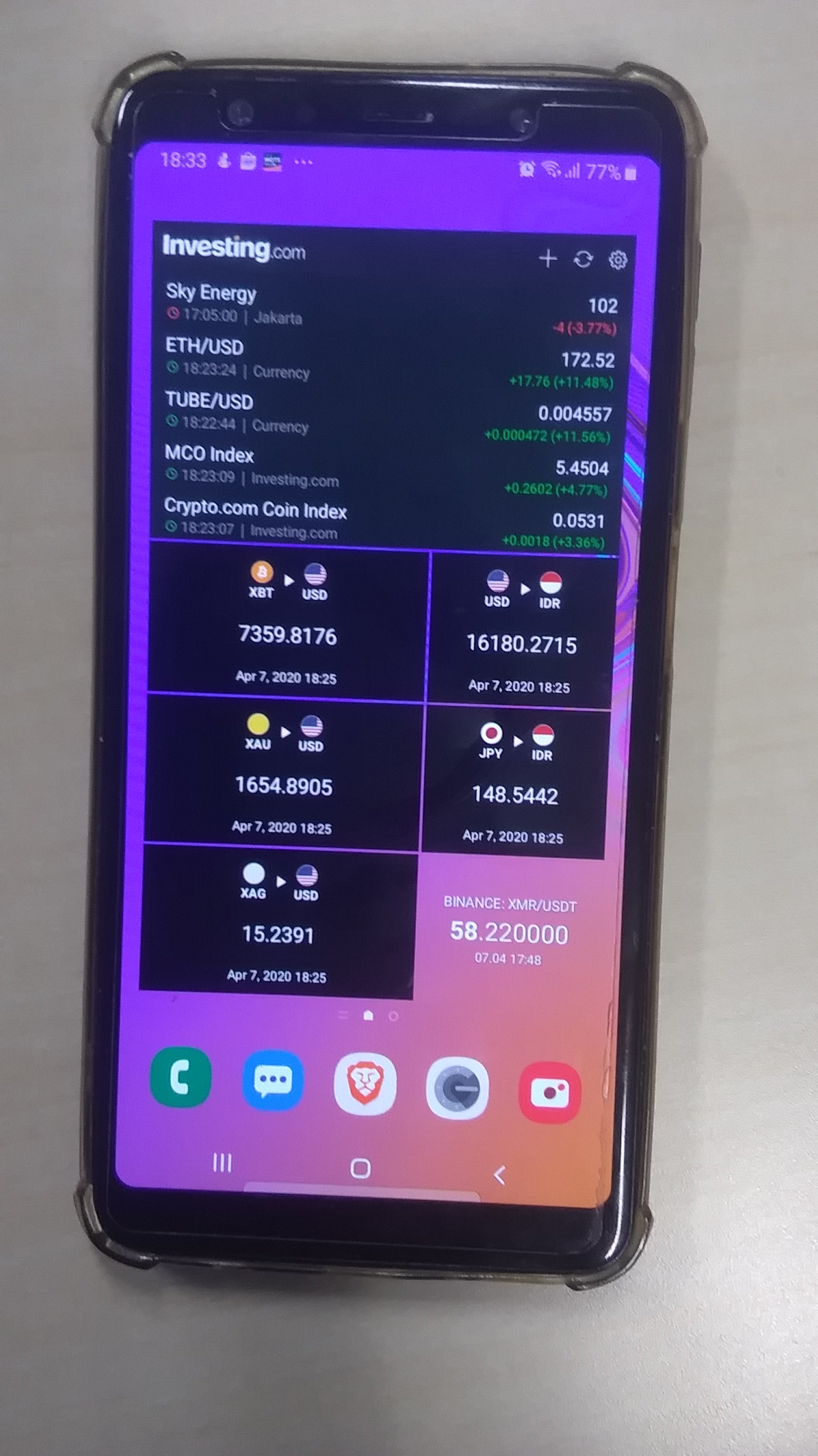
Anda mungkin sering merasa ingin melihat harga asset investasi. Itu terjadi pada saya, dan saya merasa membuang banyak waktu dan energi untuk itu.
❮ ❯Question Checklist Before You Buy Bitcoin
In 2 days the bitcoin price crashed from around $9000 to $5000. Have you learned your lesson? This is a question directed not to professional traders, supporter, or technologist, but to you who are only here to get rich quick.
❮ ❯BTCBOX Crypto Exchange Japan
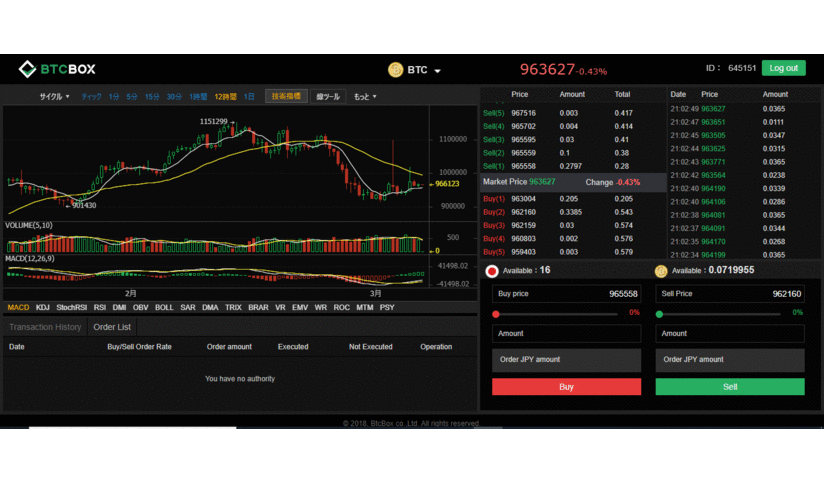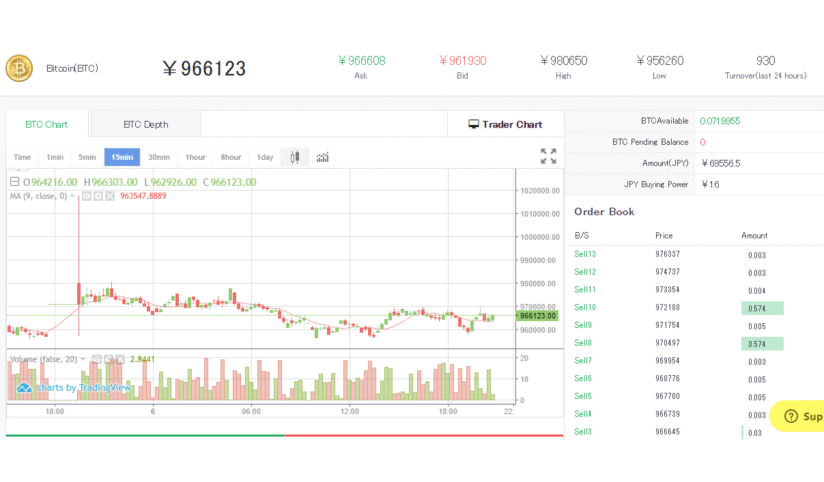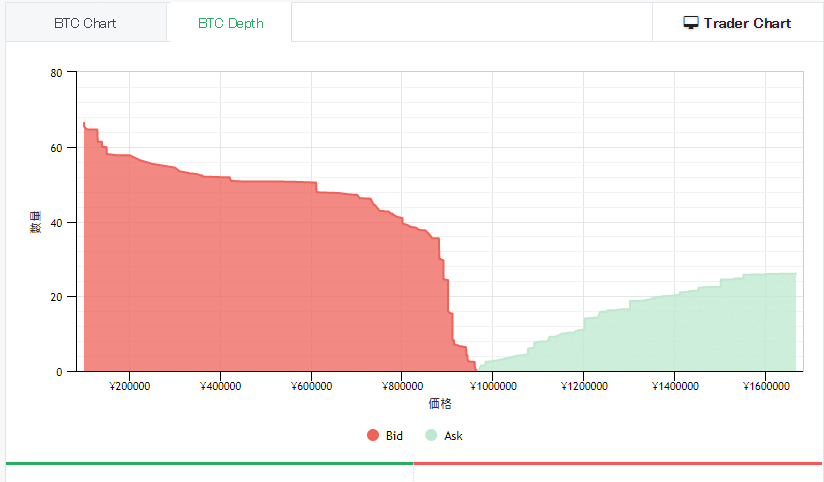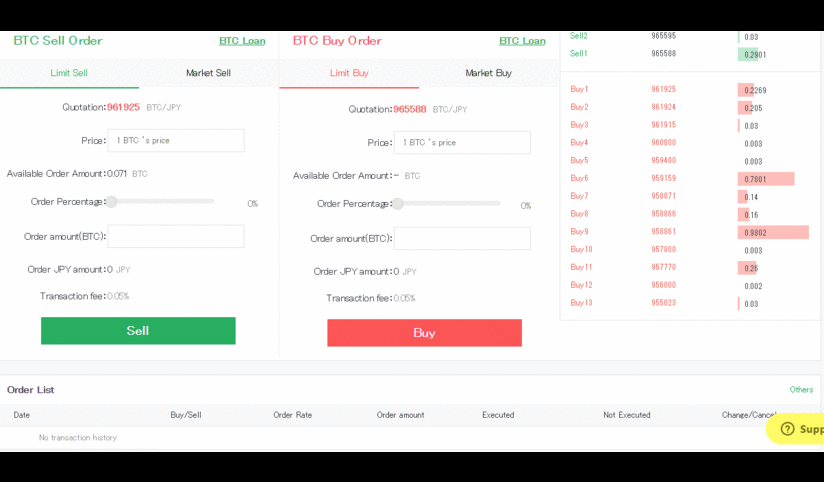
Use my code HNRCWSLFLF when registering at https://www.btcbox.co.jp and we both get ¥500. Don't miss the chance especially if you are in Japan.
❮ ❯Learn and Earn on Coinbase $50 per hour
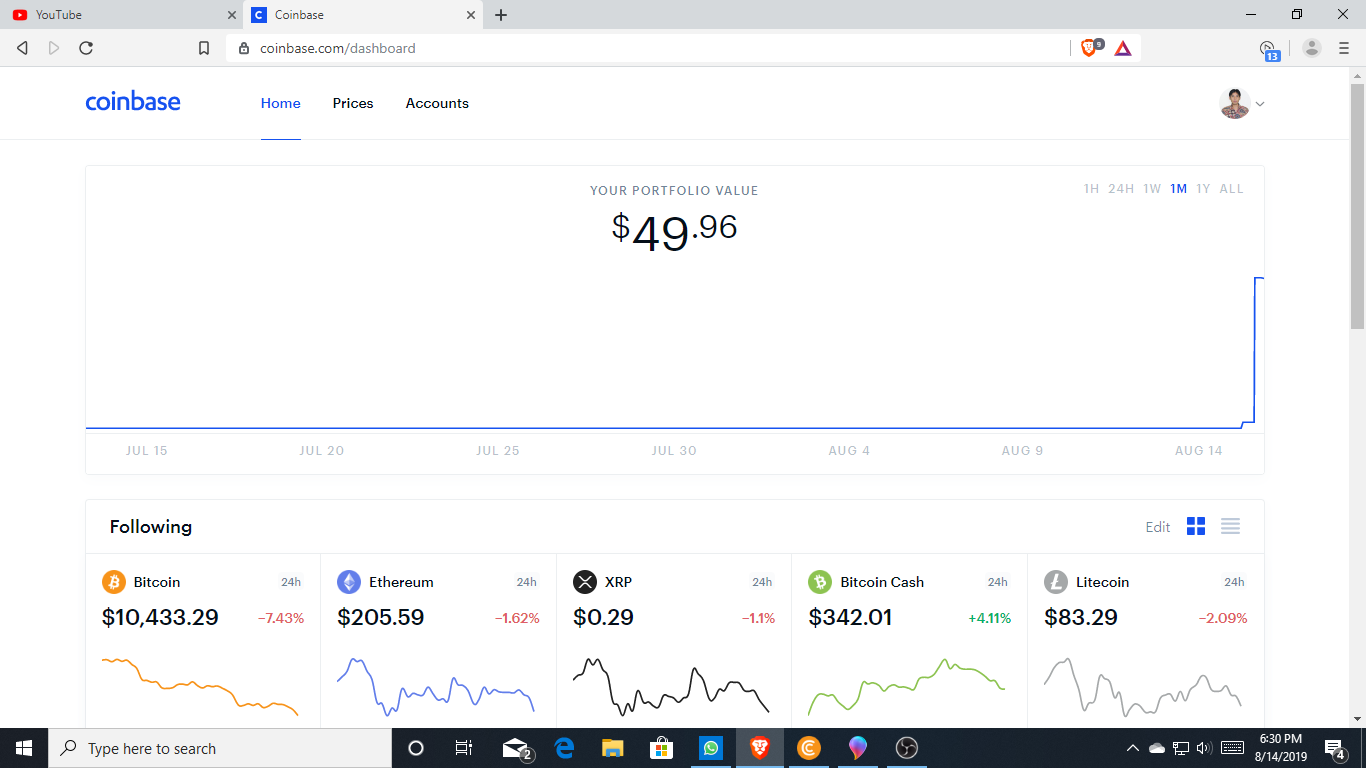
Coinbase is giving away coins for taking their free course.
❮ ❯4 Browsers that Rewards Users in Cryptocurrency
The 4 browsers that rewards users in cryptocurrency are Brave Browser, Netbox Browser, Bittube Browser or Extension, and Cryptotab Browser.
❮ ❯4 Browser yang Memberi Koin Kripto

4 Browser yang Memberi Koin Kripto adalah Brave Browser, Netbox Browser, Bittube Browser atau Extension, dan Cryptotab Browser.
❮ ❯mining
internet
Latihan Aplikasi Arsip Barang di Fluter dengan MySQL dan ExpressJs
Latihan Aplikasi Arsip Barang di Fluter
❮ ❯Indonesia Blocked Yahoo PayPal Steam Website and What Can Citizens Do
Many Indonesians are freelancers and received their salaries in PayPal. Therefore blocking PayPal, is the same as cutting off their income.
❮ ❯Python Cheat Sheet
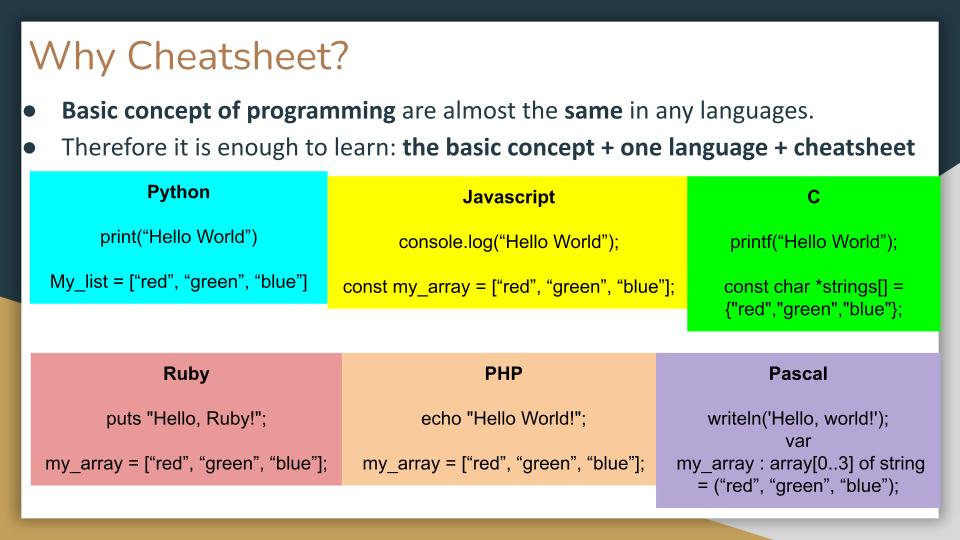
This is a cheatsheet for Python programming language that will be constantly updated.
❮ ❯Factory Reset on Smartphone and Windows and Linux
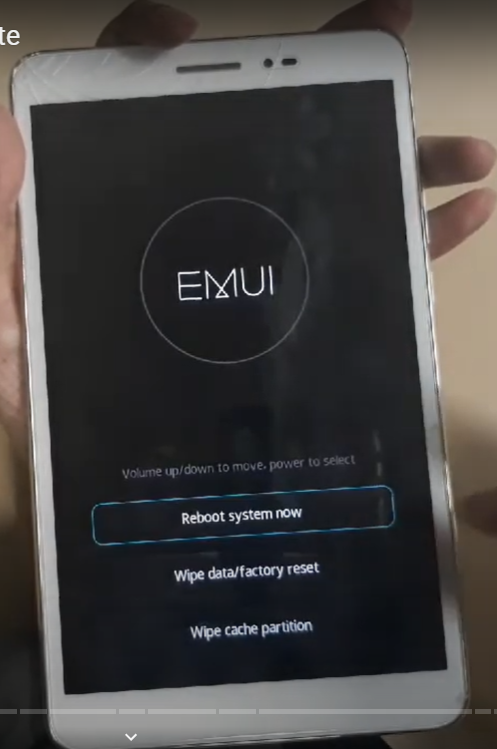
Factory reset is an action of returning a device into its initial state. On Windows is System Restore, and Linux is Time Shift & Systemback.
❮ ❯Damaged Disk Data Recovery Safe Practice

Directly fixing errors and bad block reallocation may further damage the disk so before that it is highly recommended to clone the disk and recover any data possible.
❮ ❯Disable or Customize Windows 10 Update also Linux and Android
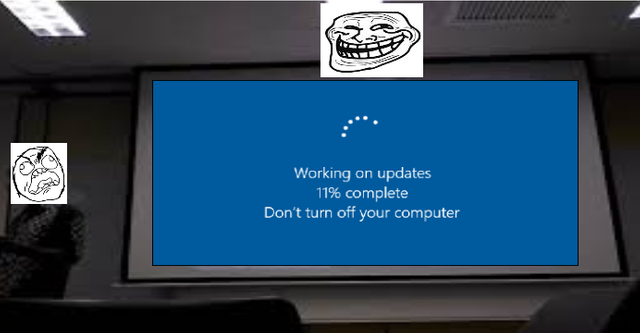
Enable Group Policy Editor, run gpedit, go to Computer Configuration, Administrative Templates, Windows Update, Configure Automatic Updates, Disable.
❮ ❯Compress Multiple Image using Windows Resizer and Image Magick Linux
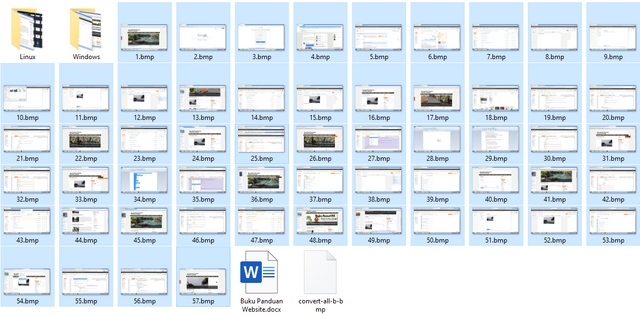
Compress multiple image using Windows Image Resizer or Image Magick Linux at once.
❮ ❯Manually Set IP Address Version 4

Most common people does not know that IP address is set on the network interface and not in the core system of the computer.
❮ ❯Scanning IP Address Version 4

When you are handling large computer networks, you probably need an automated IP scanner application. Here I use Angry IP scanner and NMAP.
❮ ❯Fix Blank Screen Nvidia Optimus Laptop Linux and Cuda
Find a suitable Nvidia driver version, install bumblebee for optimus laptop, and find suitable CUDA version, wrong version will not work.
❮ ❯Trying and Installing Linux Ubuntu Guide

The steps are download Linux, create a bootable drive, start boot menu and bootable drive, try it, and install it either in internal or external drive.
❮ ❯Setting Up ASUS Mini MP3 Player

A mini mp3 player is a portable device to store and play electronic music files. Some reasons still exist for people to own mini mp3 player.
❮ ❯Tobii 4c Eye Tracker Demo

Few years ago, the prices are over $3000 was not affordable for many people. Today, the price averages $200 where average people can afford.
❮ ❯PS1 and PS2 emulator available by default in Debian based Linux repository

The pcsxr and pcsx2 emulators are available by default on Debian repository where you only need one command line to install.
❮ ❯Upgrading Old Moodle Guide to Latest Version

I tried several upgrade paths and found one that succeeded which are moodle version 1.x > 1.9 > 2.2 > 2.7 > 2.9 > 3.0 > latest.
❮ ❯Installing Moodle Guide on Windows XAMPP
The difference on the Ubuntu version is the directory location C:xampp\htdocs and GUI control panel and the rest of the process are the same
❮ ❯Installing Moodle Guide on Debian Based Linux

The steps are installing web and database server, php packages, download moodle files and put into web server directory, and open browser.
❮ ❯Android Emulator and Operating System for Personal Computer
Here I demonstrate Brave Frontier on Microsoft Store Windows, Bluestacks on Windows, Genymotion on Linux, and Remix OS on personal computer.
❮ ❯Overheated Acer Turns Out That The Fan Was Rusted

I feel the laptop each time it boots and finally found the problem that it was overheated. I disassembled it and found the fan to be rusted.
❮ ❯Common Ways to Bypass Internet Censorship
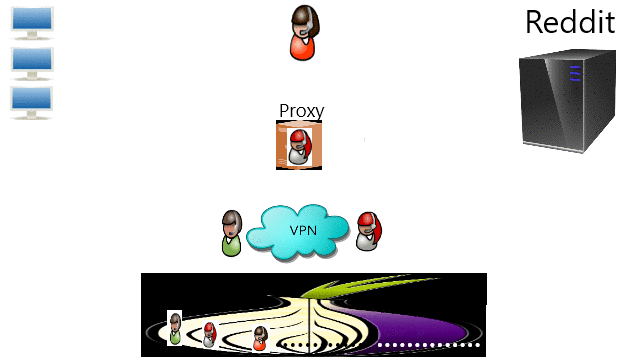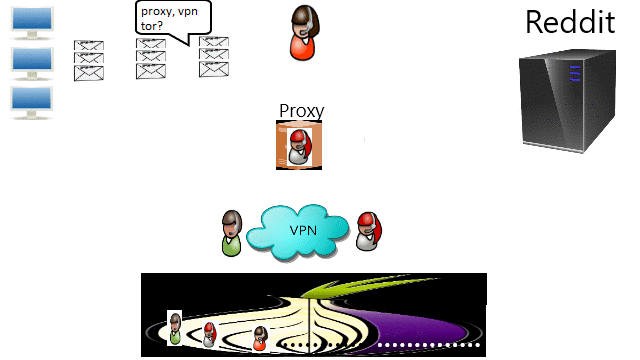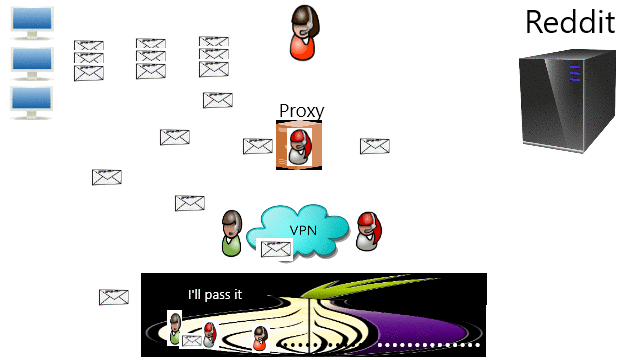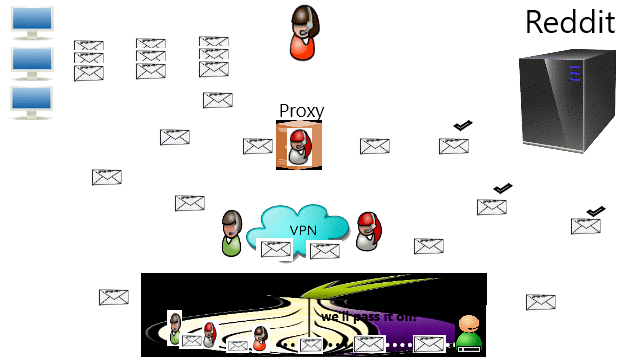
Porn blocked sure, but Reddit and Imgur? What more? The common ways I found are by DNS, proxy, VPN, and TOR. Leave a comment if you know anymore.
❮ ❯Cara Biasa Melewati Sensor Internet

Pornografi diblokir, tetapi Reddit dan Imgur juga? Cara umum yang saya temukan adalah DNS, proxy, VPN, dan TOR. Adakah cara lain?
❮ ❯Melewati Sensor dengan TOR
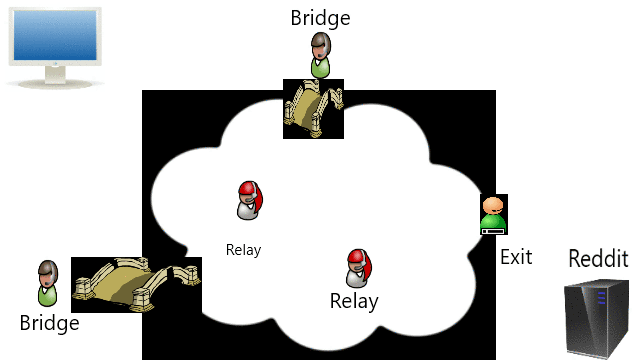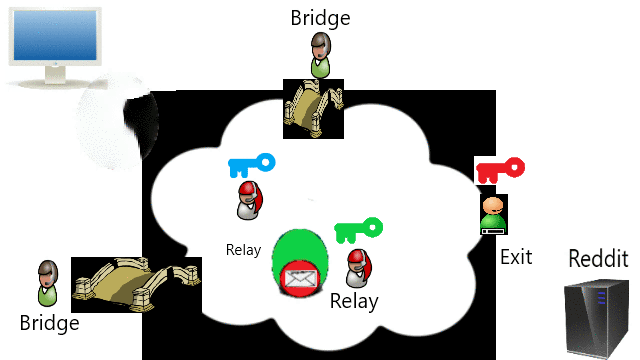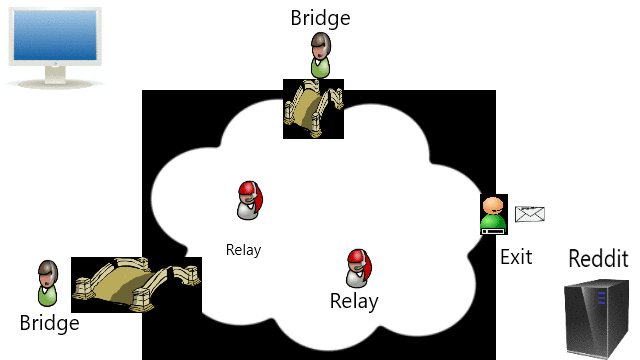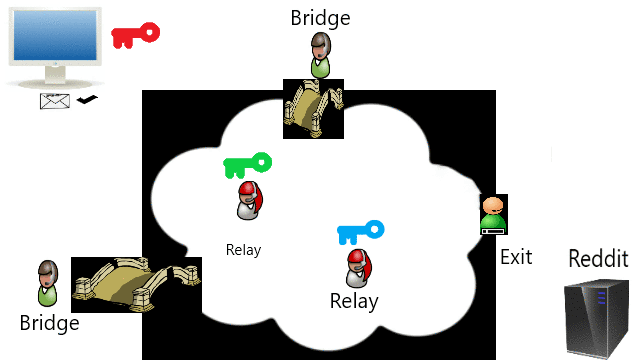
Onion Router (TOR) adalah implementasi open source dari perutean bawang untuk anonimitas dan privasi, saya menggunakannya untuk melewati sensor.
❮ ❯Bypass Censorship By TOR

The Onion Router (TOR) is an open source implementation of onion routing for anonymity and privacy, but I use them for bypassing censorship.
❮ ❯Melewati Sensor dengan VPN
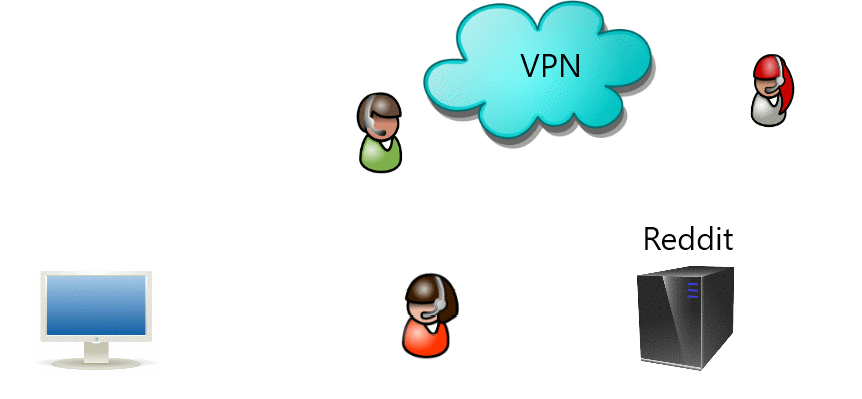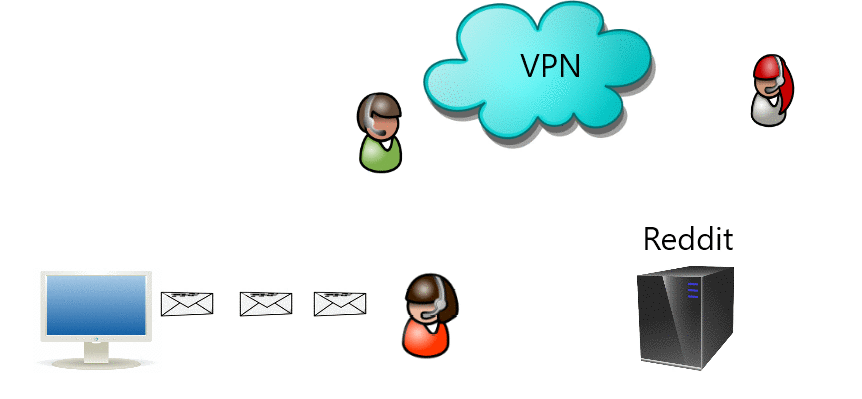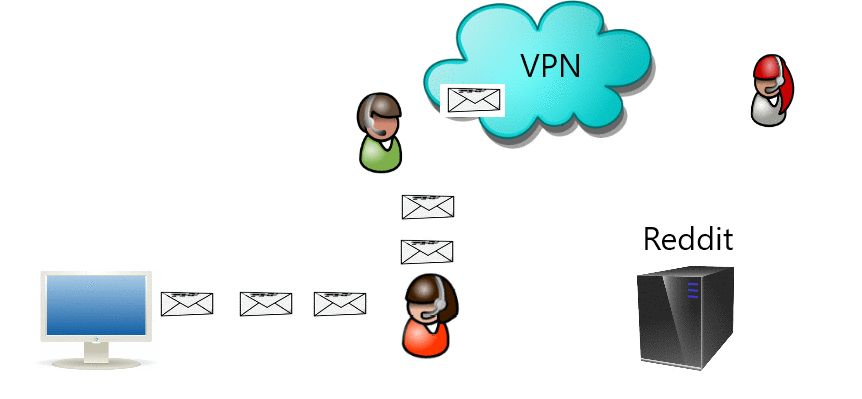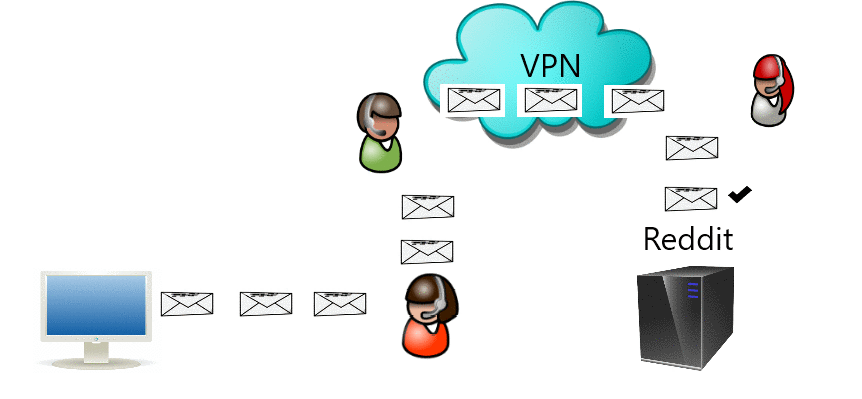
Jaringan pribadi virtual (VPN) memperluas jaringan pribadi melintasi jaringan publik. Jika jalur keluar terbuka dapat digunakan untuk melewati sensor.
❮ ❯Bypass Censorship By VPN

Virtual private network (VPN) extends a private network across a public network where if outgoing path is open can also be used to bypass censorship.
❮ ❯Melewati Sensor dengan Proxy
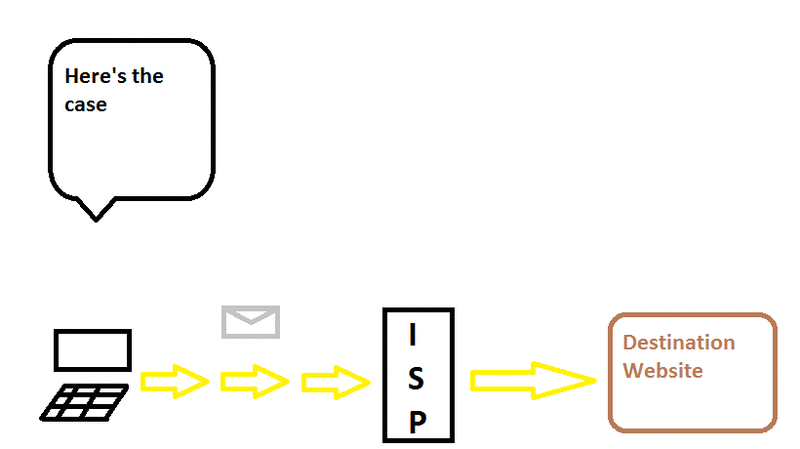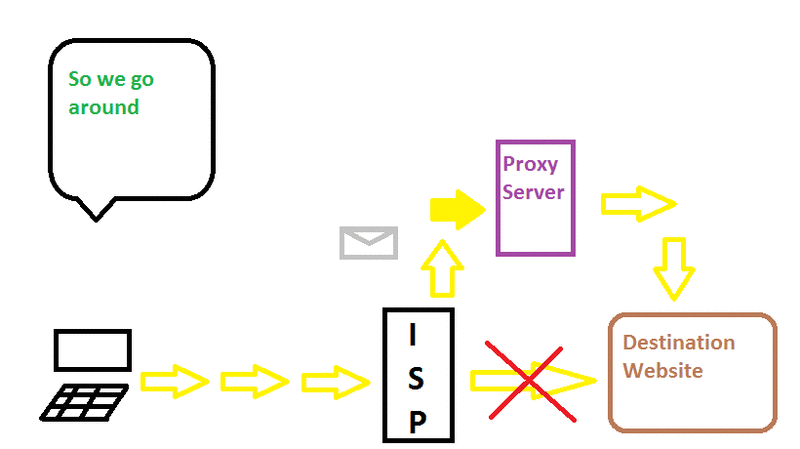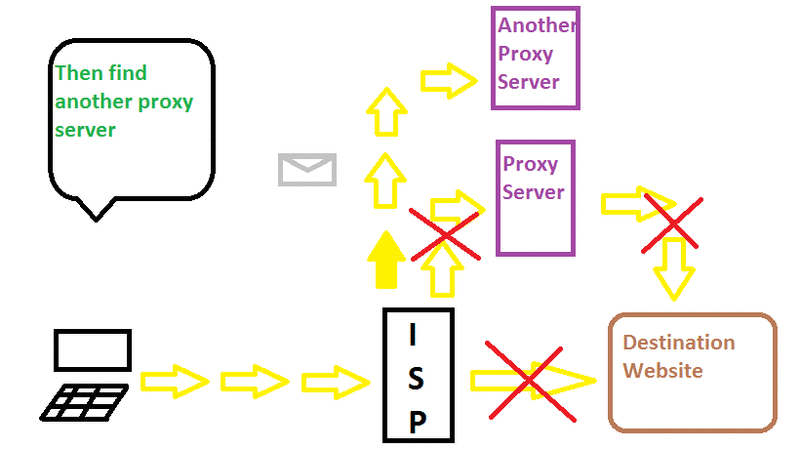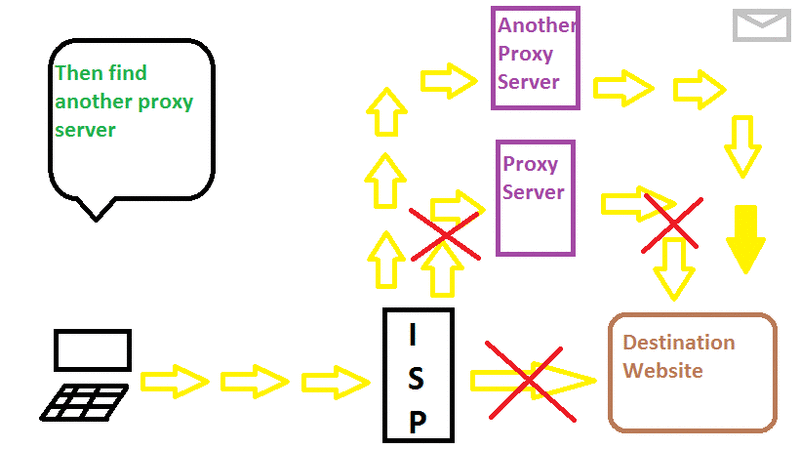
Daripada langsung ke alamat tujuan, paket akan pergi ke server proxy dan diproses di sana sebelum pergi ke tujuan
❮ ❯Bypass Censorship By Proxy

Instead of going straight ahead to the destination address the packets turn around to the proxy server and processed there before going to the origin.
❮ ❯Melewati Sensor dengan DNS
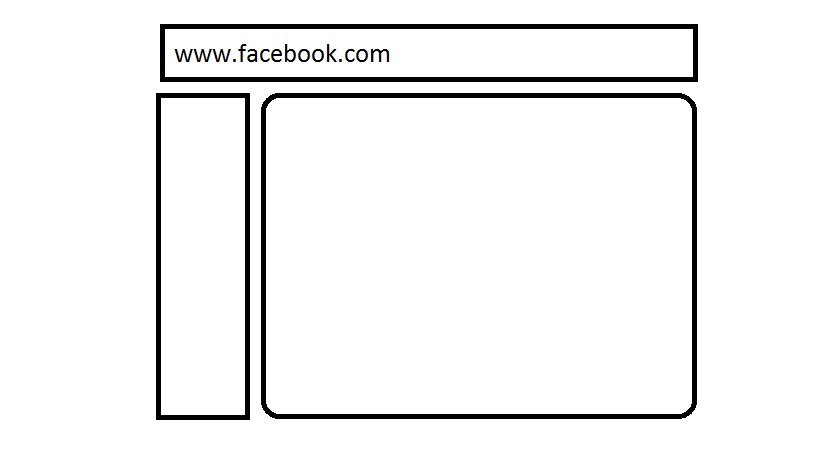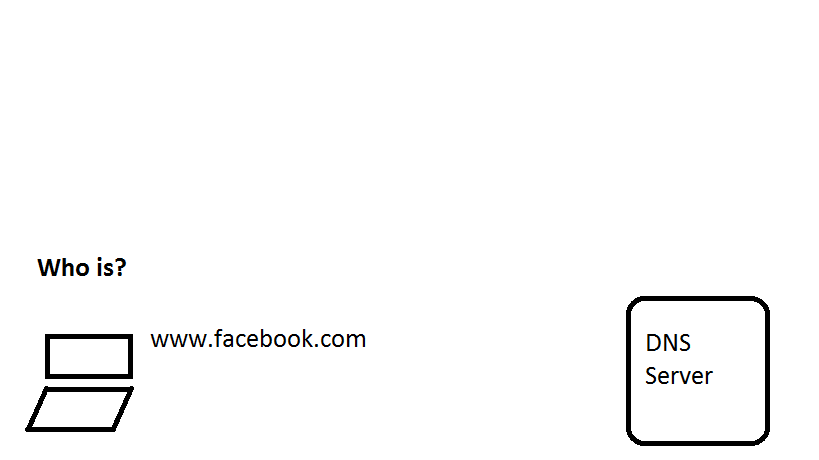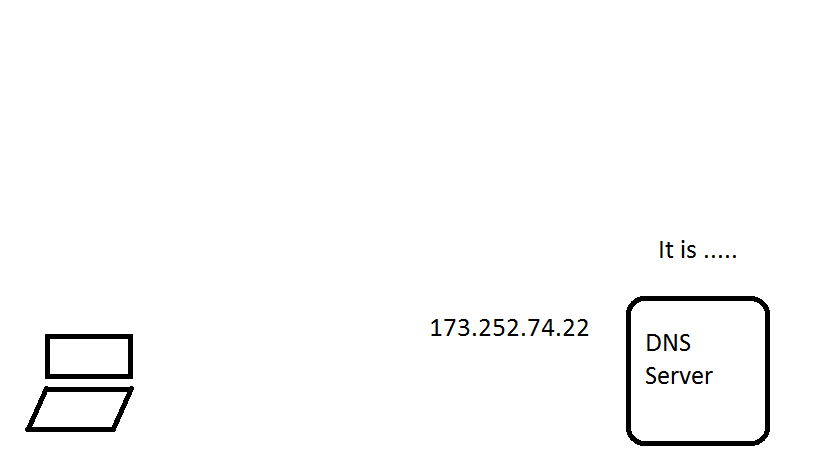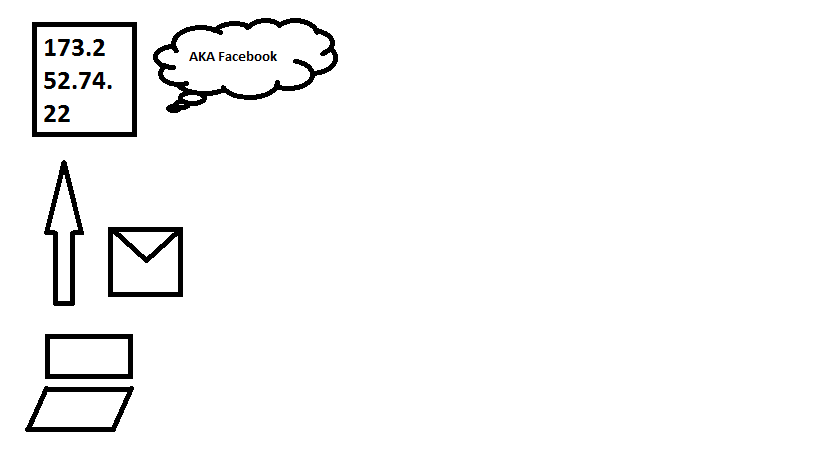
Mengubah DNS pada klien juga termasuk yang paling mendasar karena ada banyak server DNS terbuka di luar sana dibandingkan dengan server proxy dan VPN.
❮ ❯Bypass Censorship By DNS

Changing DNS on client is also among the most basic because there are many open DNS server out there compared to proxy and VPN server.
❮ ❯Ikon Hiperlink
Tujuannya adalah untuk mempercantik dan menyederhanakan hyperlink yang ada berdasarkan pepatah satu gambar bisa berarti seribu kata.
❮ ❯Hyperlink Icon
The purpose in my opinion is to beautify and simplify hyperlinks where there is a saying that a single picture can mean a thousand words.
❮ ❯Membuat Kata Sandi yang Kuat
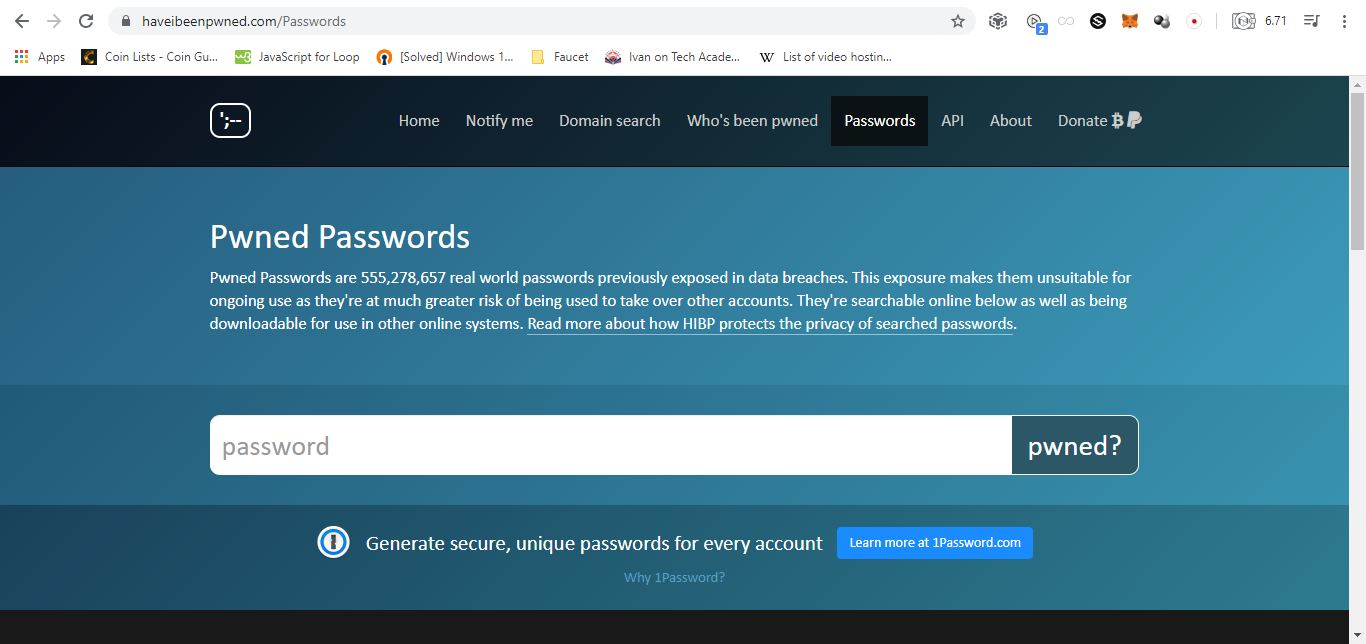
Kata sandi yang kuat berisi huruf kecil, huruf kapital, angka, simbol, lebih dari 6 karakter. Yang super berisi simbol bukan di keyboard
❮ ❯Creating Strong Passwords

Strong password contains small letters, capital letters, numbers, symbol, more than 6 characters. Super ones contain symbols not on keyboard
❮ ❯Starting Computer Programming

This article introduces computer programming for those who would like to dive into the world of programming starting with Pascal and C lang.
❮ ❯Simple Introduction to Computer Network and the Internet
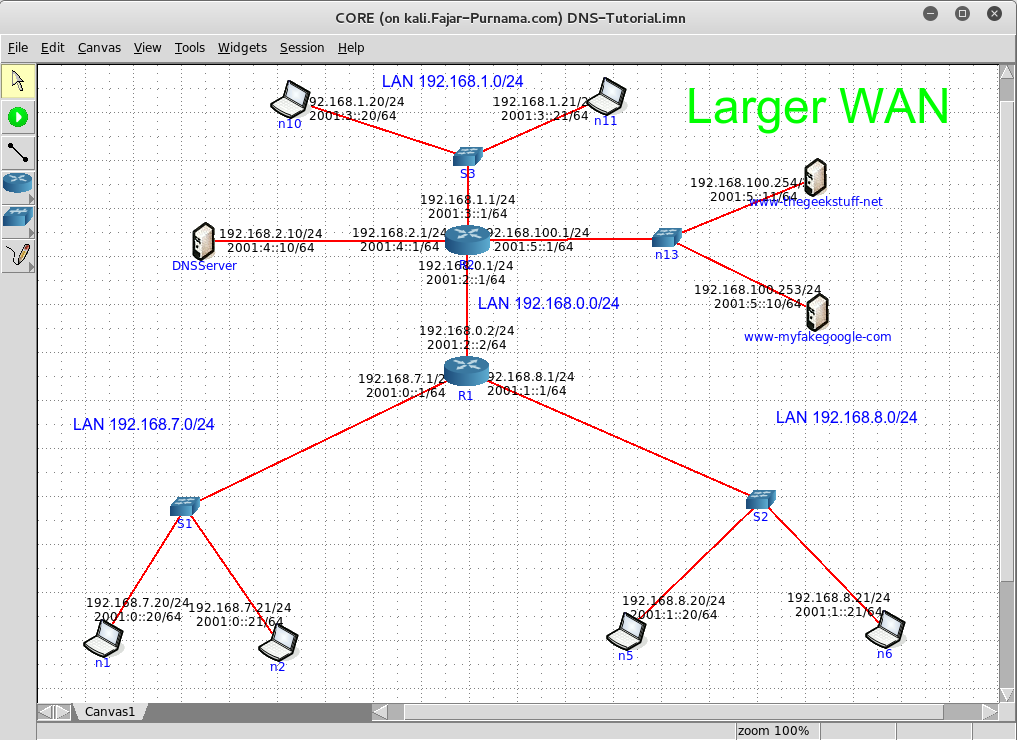
Objective is simulate Local Area Network (LAN). Simulate Wide Area Network (WAN). Common services of The Internet. Design your simple cloud.
❮ ❯finance
Various Investments Through Financial Technology

The various types of investments are certificate of deposits, mutual funds, government bonds, stocks, commodities, and cryptocurrencies.
❮ ❯donation
pentest
Denial of Service (DOS) on Wifi using Ostinato Linux
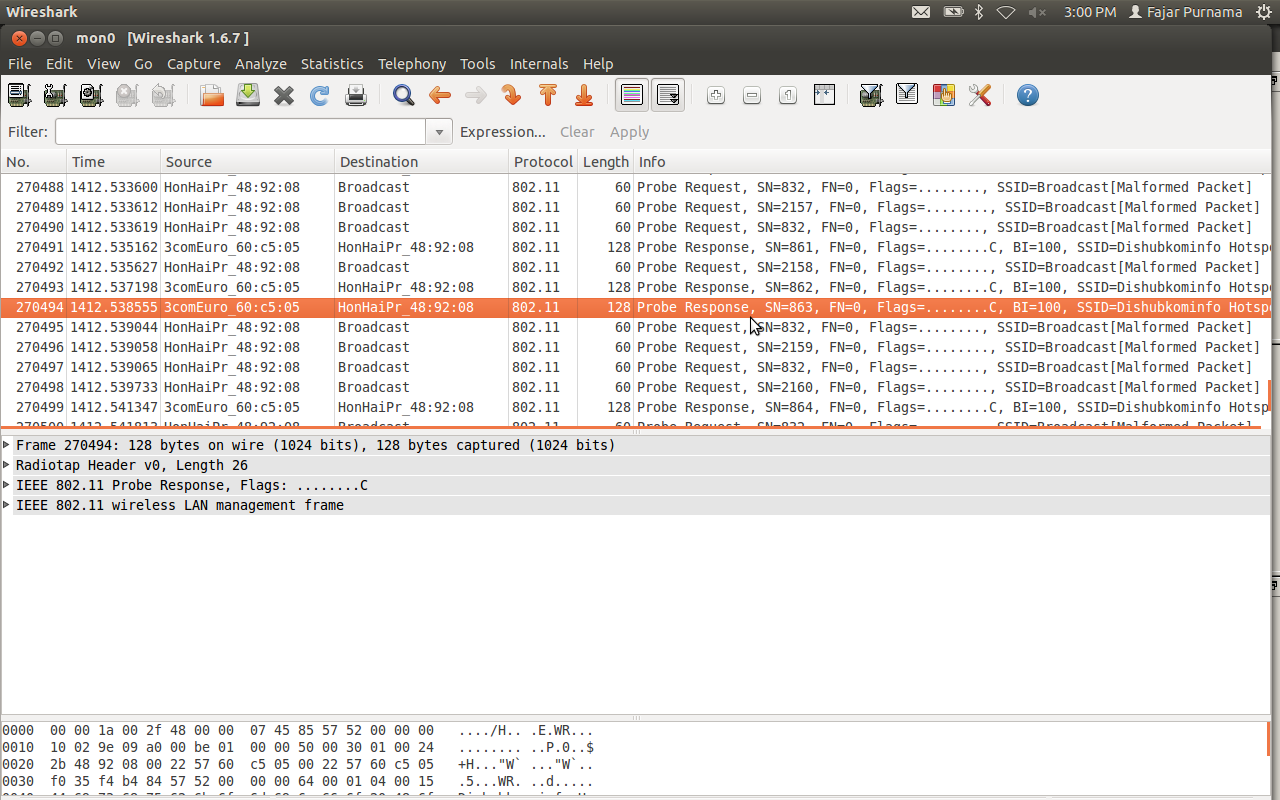
There was no CommView in Linux where I used it to perform DoS. However, I found a similar software called Ostinato and it can work for Dos.
❮ ❯Denial of Service (DOS) Pada Wifi Menggunakan Ostinato Linux
Tidak ada CommView di Linux untuk melakukan DoS. Namun, saya menemukan perangkat lunak serupa yang disebut Ostinato dan dapat Dos.
❮ ❯Denial of Service (DOS) on Wifi using CommView Windows
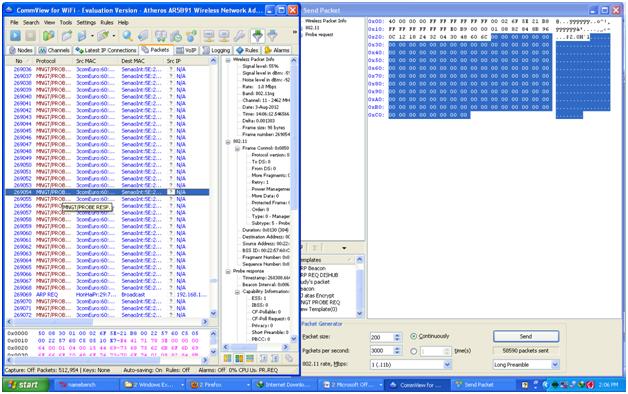
DOS prevents other users from doing activities on the network. Here I will demonstrate DOS on a wifi using CommView for WiFi on Windows.
❮ ❯Denial of Service (DOS) Pada Wifi Menggunakan CommView Windows

DOS mencegah pengguna lain beraktivitas di jaringan. Di sini saya akan mendemonstrasikan DOS pada wifi menggunakan CommView for WiFi di Windows.
❮ ❯Simple Password Bruteforce Demonstration Using Hydra

I can define password brute forcing in just one sentence which is trying every single character combination to crack a password.
❮ ❯Demonstrasi Bruteforce Sederhana Menggunakan Hydra

Saya dapat mendefinisikan password bruteforce hanya dalam satu kalimat yaitu mencoba setiap kombinasi karakter untuk memecahkan kata sandi.
❮ ❯Having a Taste of Being a Hacker
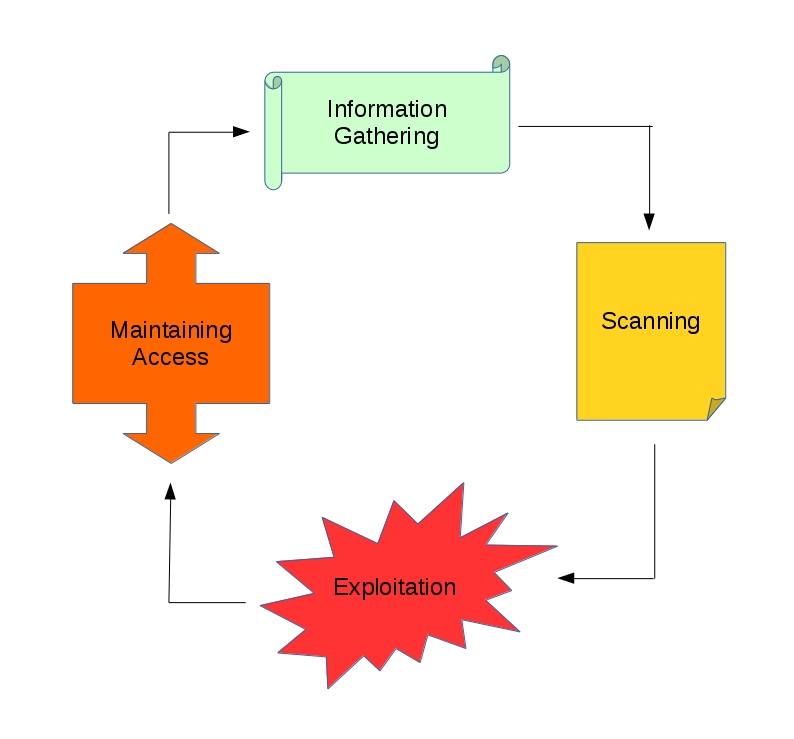
There are four main steps in penetration testing which are (1) Information Gathering, (2) Scanning, (3) Exploitation, (4) Maintaining Access
❮ ❯tools
AudioSynth Slider Mixer in HTML CSS JavaScript
AudioSynth Slider Mixer in hyper text markup language, cascading style sheets, and javascript.
❮ ❯PDF Tools in HTML CSS JavaScript
PDF Tools in hyper text markup language, cascading style sheets, and javascript.
❮ ❯Simple Piano in HTML CSS JavaScript
Simple Piano in hyper text markup language, cascading style sheets, and javascript.
❮ ❯Date Time Dashboard in HTML CSS JavaScript
Date Time Dashboard in hyper text markup language, cascading style sheets, and javascript.
❮ ❯Image Editor in HTML CSS JavaScript

Image Editor in hyper text markup language, cascading style sheets, and javascript.
❮ ❯Text Case Converter in HTML CSS JavaScript
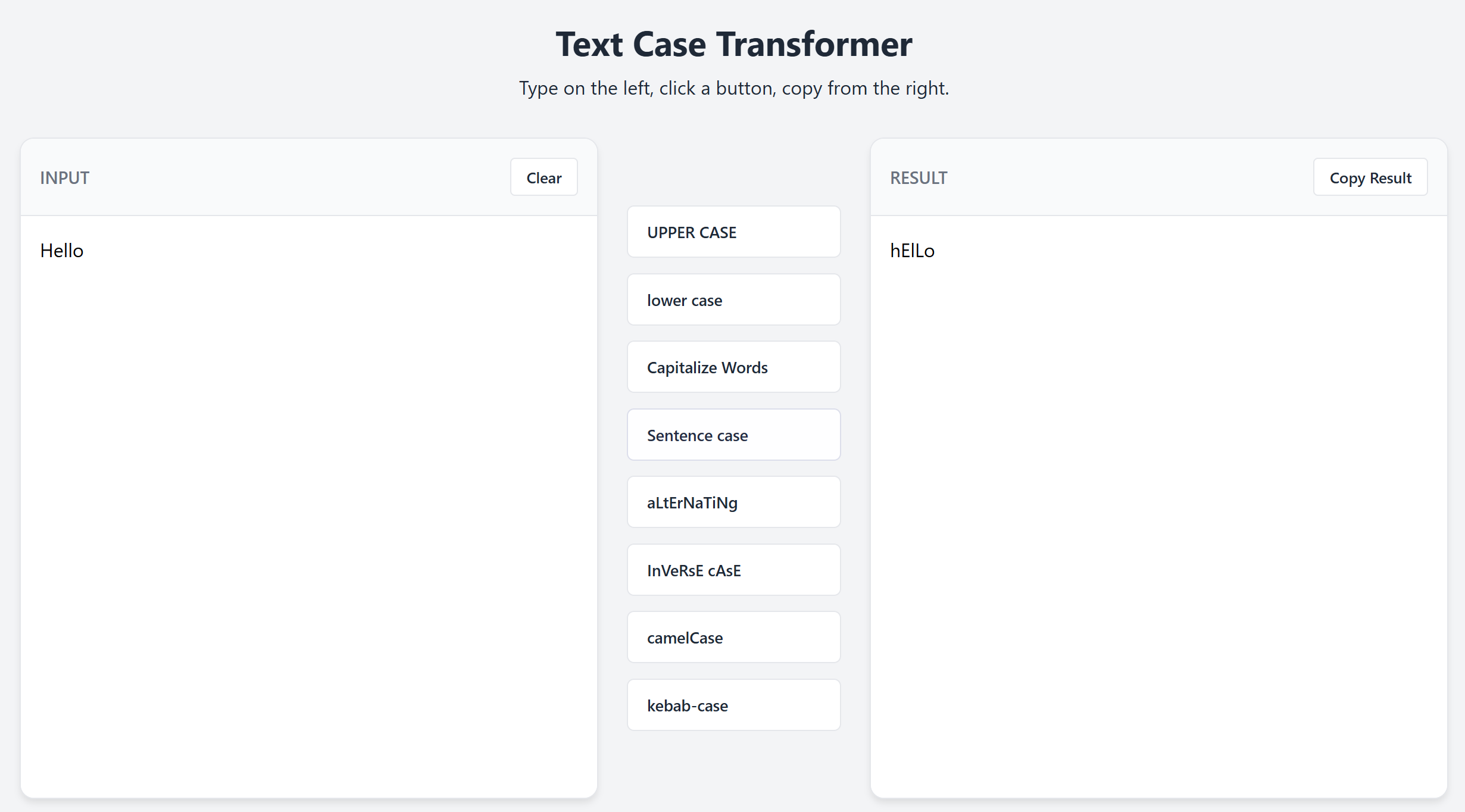
Text Case Converter game in hyper text markup language, cascading style sheets, and javascript.
❮ ❯Minesweeper in HTML CSS JavaScript
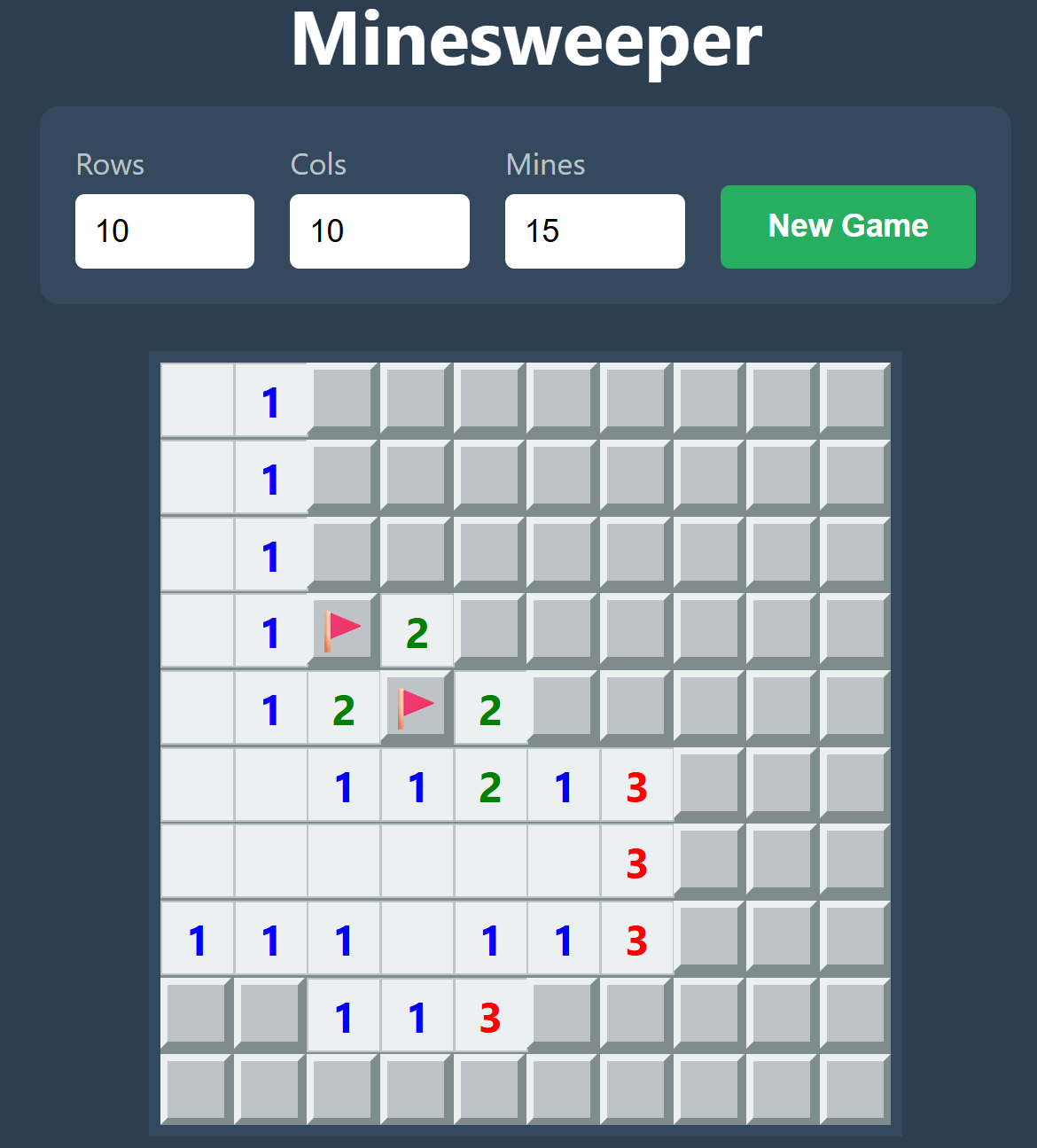
Minesweeper game in hyper text markup language, cascading style sheets, and javascript.
❮ ❯Chess Board 2 Player Peer to Peer HTML CSS JavaScript

Play chess together through peer to peer (p2p) protocol hyper text markup language, cascading style sheets, and javascript.
❮ ❯Chess Board 2 Player Local HTML CSS JavaScript

Play chess together on single browsertab hyper text markup language, cascading style sheets, and javascript.
❮ ❯Chess Board Tree Explorer HTML CSS JavaScript
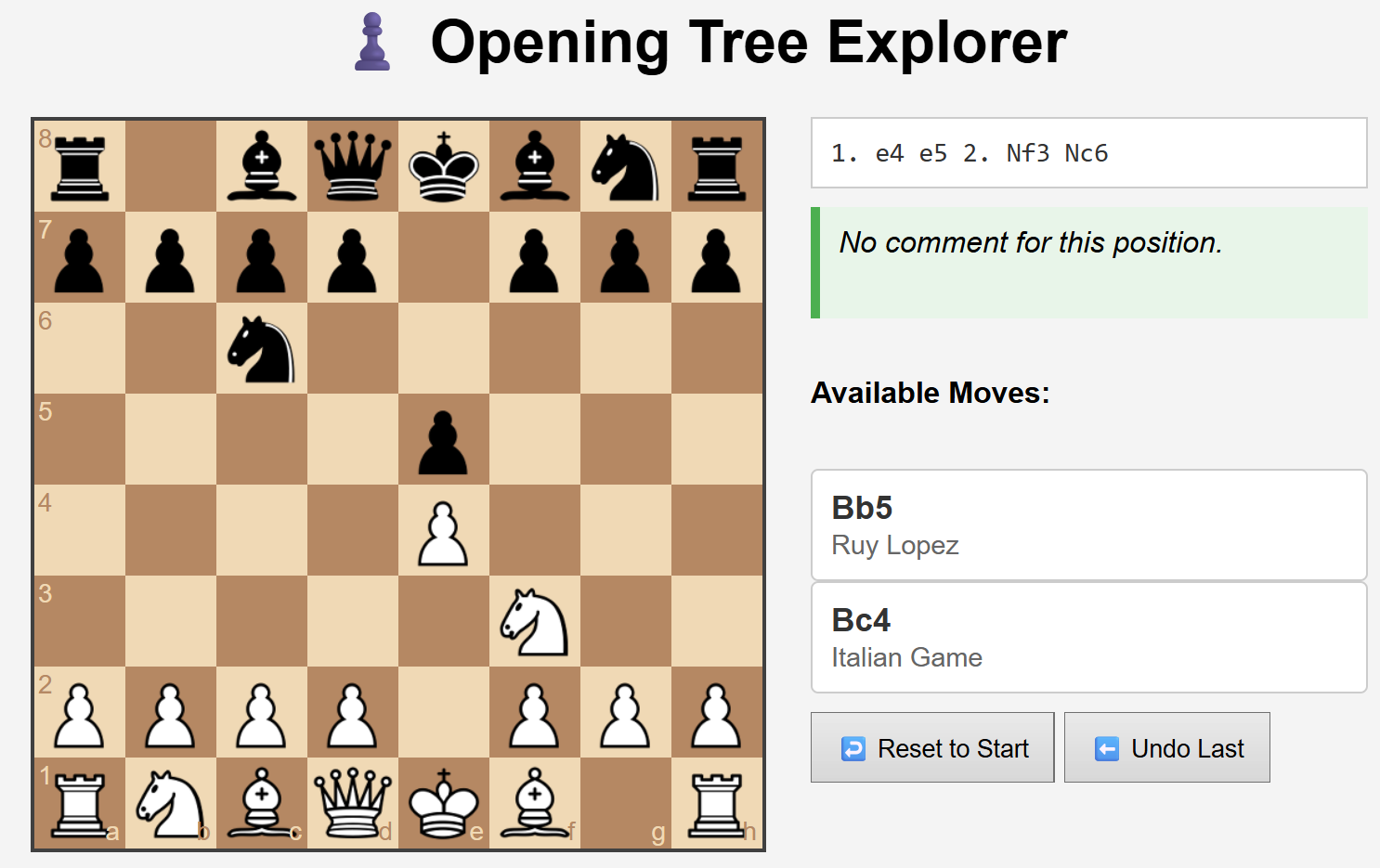
A chess board tree explorer only in hyper text markup language, cascading style sheets, and javascript.
❮ ❯Chess Board HTML CSS JavaScript

A chess board only in hyper text markup language, cascading style sheets, and javascript.
❮ ❯Ask Anything with Expert Chat Open AI GPT Widget

A widget for chat open ai gpt only in html, css, and javascript for any website.
❮ ❯Cryptocurrency Dashboard
Dashboard to dive into cryptoccurency for my entertainment and hopefully others can enjoy as well.
❮ ❯quote
bachelor
Server Room Safety and Security Consideration Case Study Server Room GDLN UNUD 2012

Here we will discuss about the physical and virtual safety and security of server room and data center from unwanted threats to last long.
❮ ❯Assignment About Flow Control and Selective Repeat ARQ
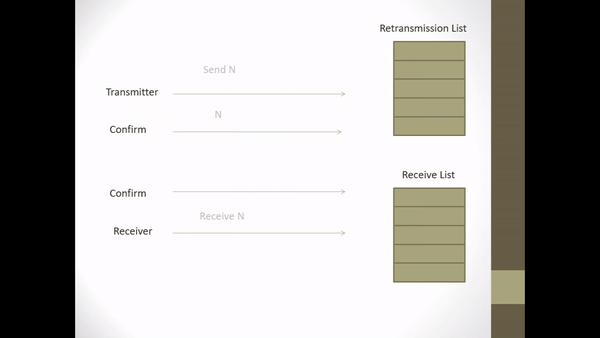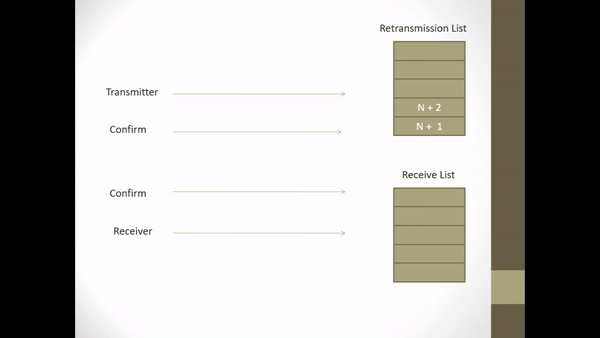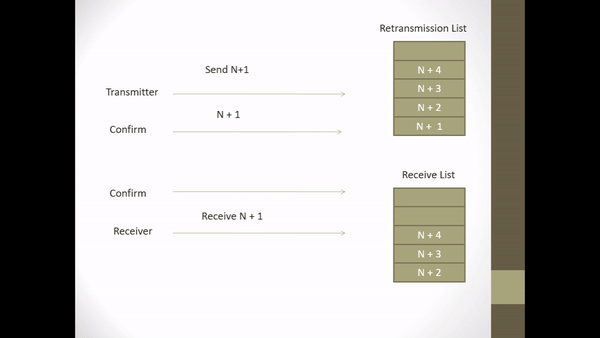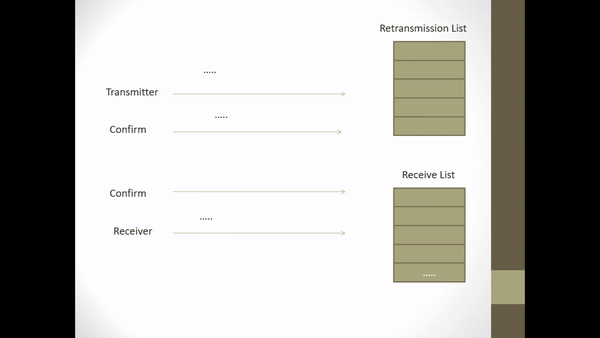
Data Communication course about writing essays on flow control, error detection & control, and selective repeat ARQ.
❮ ❯Tugas Kuliah Tentang Flow Control dan Selective Repeat ARQ

Tugas kuliah Komunikasi Data menulis essai mengenai flow control, error detection & control, dan selective repeat ARQ.
❮ ❯Trojan Horse Demonstration with Metasploit Framework Payload
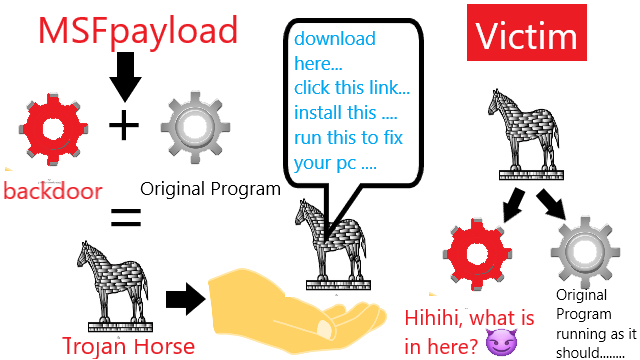
Metasploit Framework Payload practice, the difference with an ordinary backdoor is that a Trojan horse disguises itself as a legitimate program.
❮ ❯Demonstrasi Trojan Horse dengan Metasploit Framework Payload
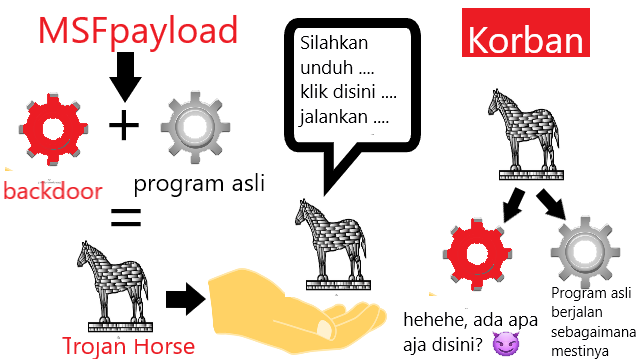
Praktik Metasploit Framework Payload, bedanya dengan backdoor biasa adalah trojan horse menyamar sebagai program sah.
❮ ❯Making Private Streaming Server as Media for Surveillance Cameras with Red5
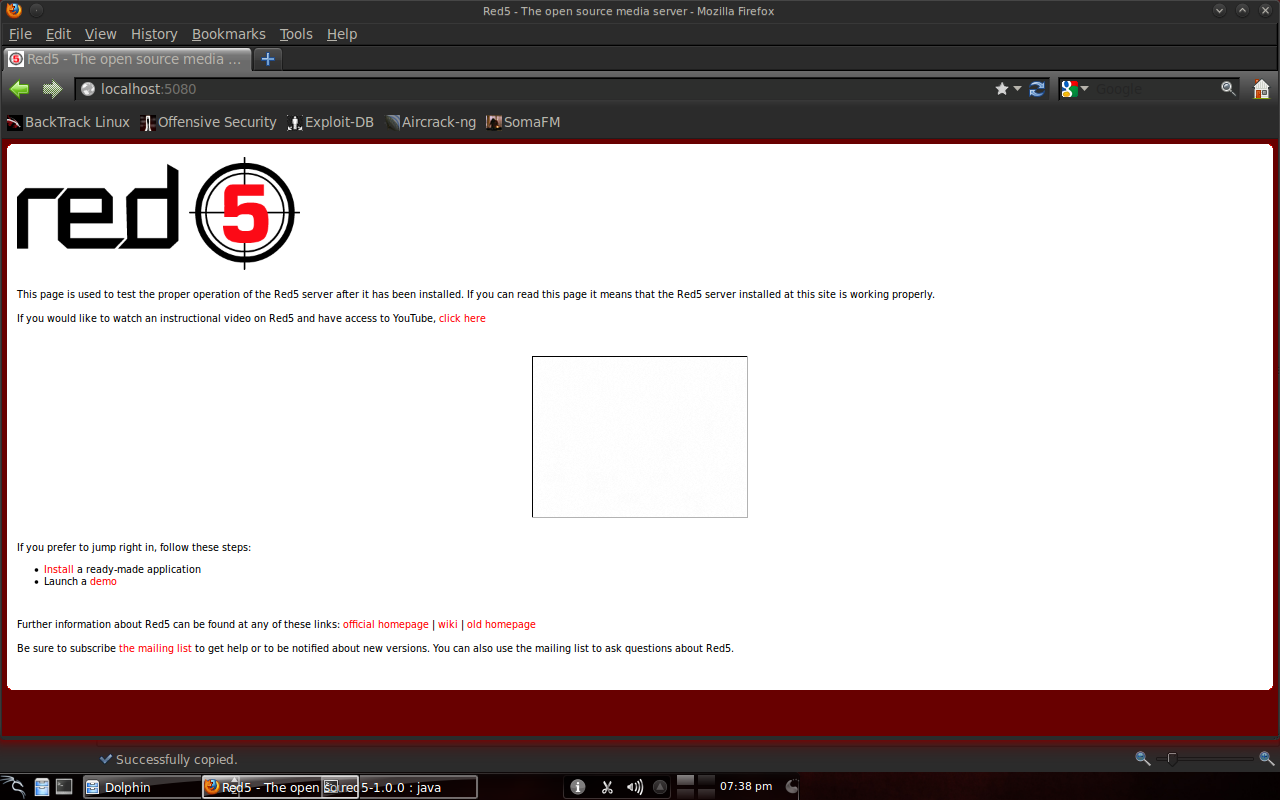
Other colleagues chose HTML5 server streaming software, VLC, Adobe Flash, etc., and I got the rare one, Red5.
❮ ❯Pembuatan Streaming Server Pribadi Sebagai Media Kamera Pengawas dengan Red5
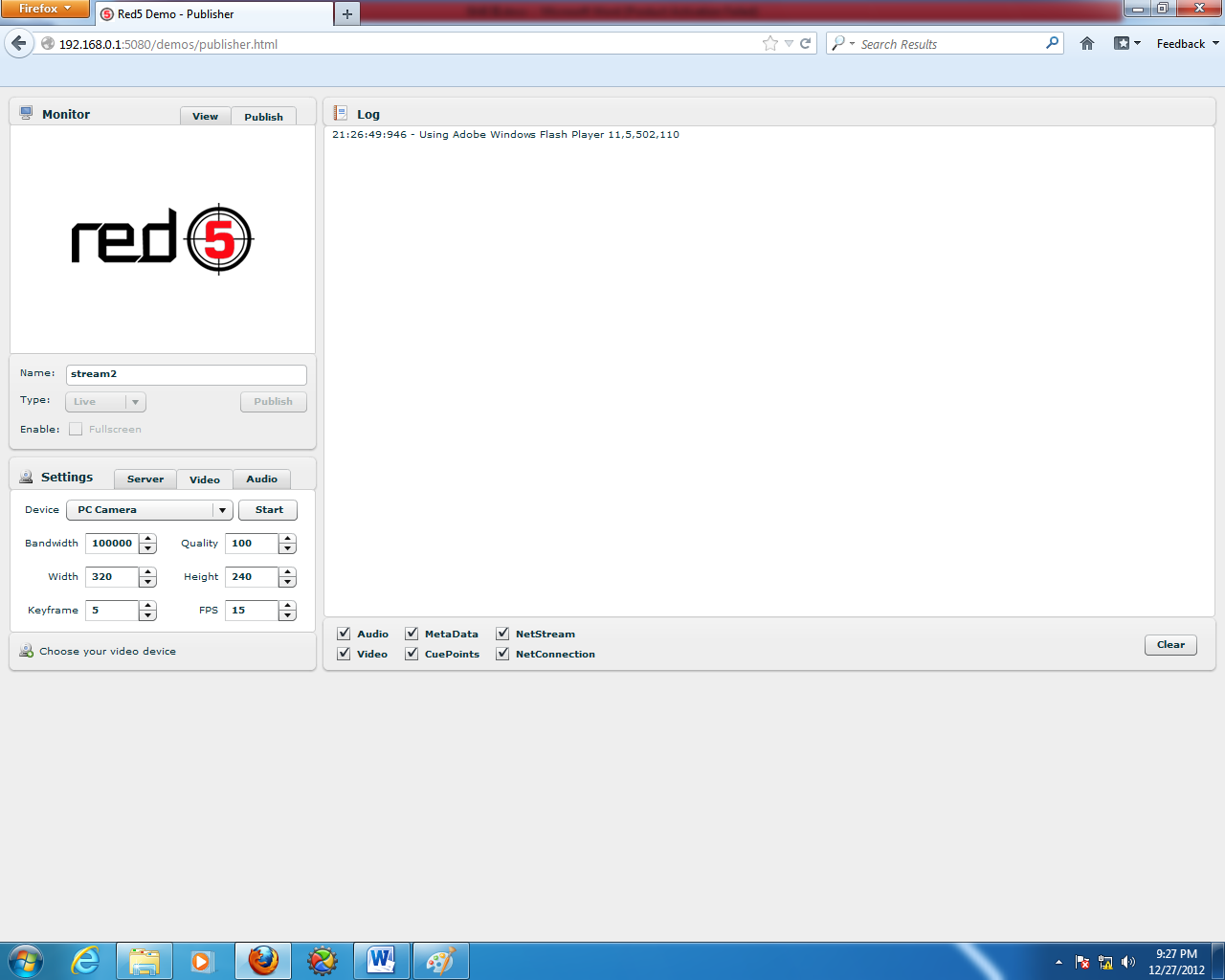
Rekan yang lain memilih software streaming server HTML5, VLC, Adobe Flash, dll, dan saya dapat yang langka yaitu Red5.
❮ ❯Mindmapping using Semantik on KDE Linux
This is my undergraduate assignment in the 2013 Technology Application in Education course regarding KDE Linux Semantik.
❮ ❯Mindmapping menggunakan Semantik pada Linux KDE
Ini merupakan tugas S1 saya pada mata kuliah Aplikasi Teknologi Dalam Pembelajaran 2013 mengenai Semantik Linux KDE.
❮ ❯3G Network Modem Signal Amplification Testing With Parabolic Pan

3G modem signal strength can be increased by parabolic bazooka pan and reduce Internet connection instability.
❮ ❯Pengujian Penguatan Kuat Sinyal Modem Jaringan 3G Dengan Wajanbolic
%20dan%20dengan%20wajanbolic%20(kanan).png)
Kuat sinyal modem 3G dapat ditingkatkan dengan wajanbolic bazooka dan mengurangi ketidak stabilan koneksi Internet.
❮ ❯Pengujian Wajan Parabola Sebagai Alat Bantu Penguat Sinyal Pada Modem AT&T

Dulu saya menggunakan modem tetapi bermasalah dengan stabilitas koneksi Internet. Kuat sinyal modem dapat ditingkatkan dengan wajanbolic.
❮ ❯Testing Parabolic Pans as a Signal Amplifier Tool on AT&T Modems

I had problems with the modem's Internet connection stability. Modem signal strength can be increased using parabolic pan.
❮ ❯Droptail Simulation and Random Early Detection in Network Simulator 3
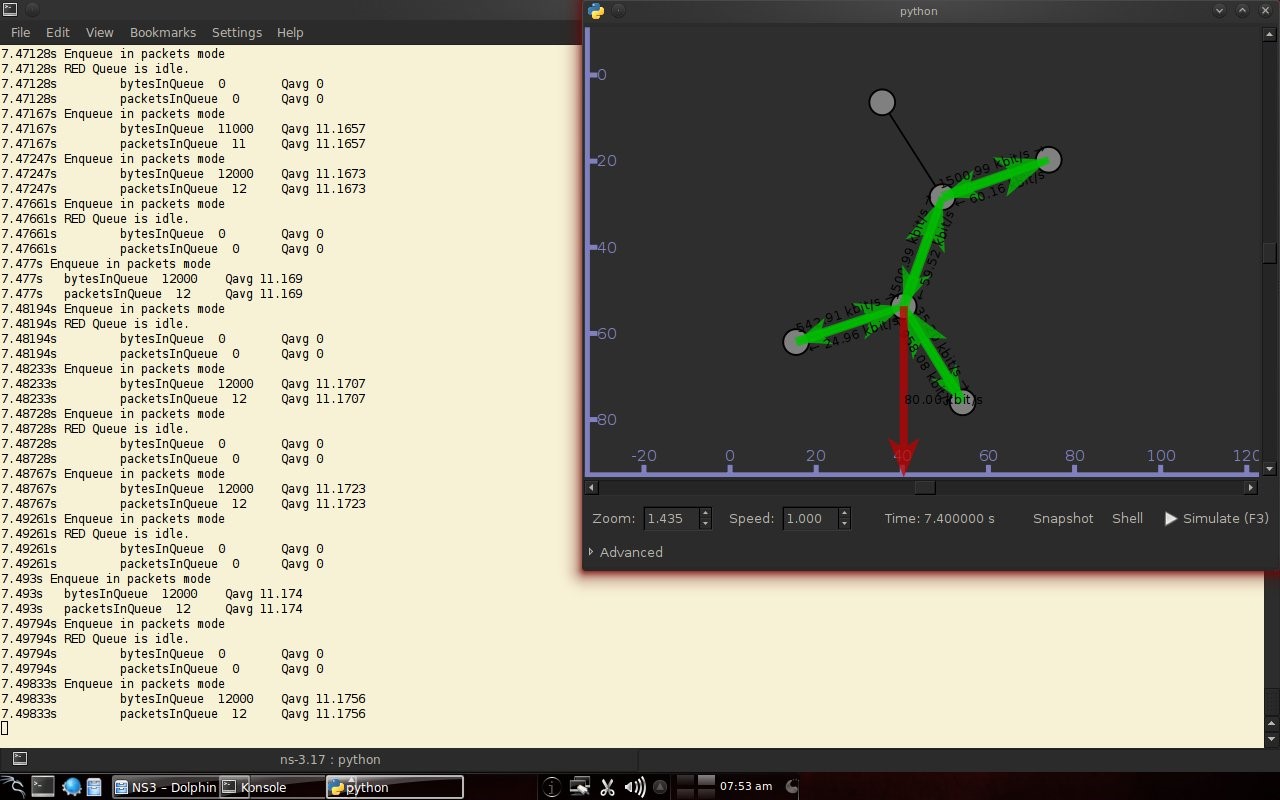
Network Simulator 3 can simulate REDQueue and display animation so it's easier to observe.
❮ ❯Simulasi Droptail dan Random Early Detection Pada Network Simulator 3
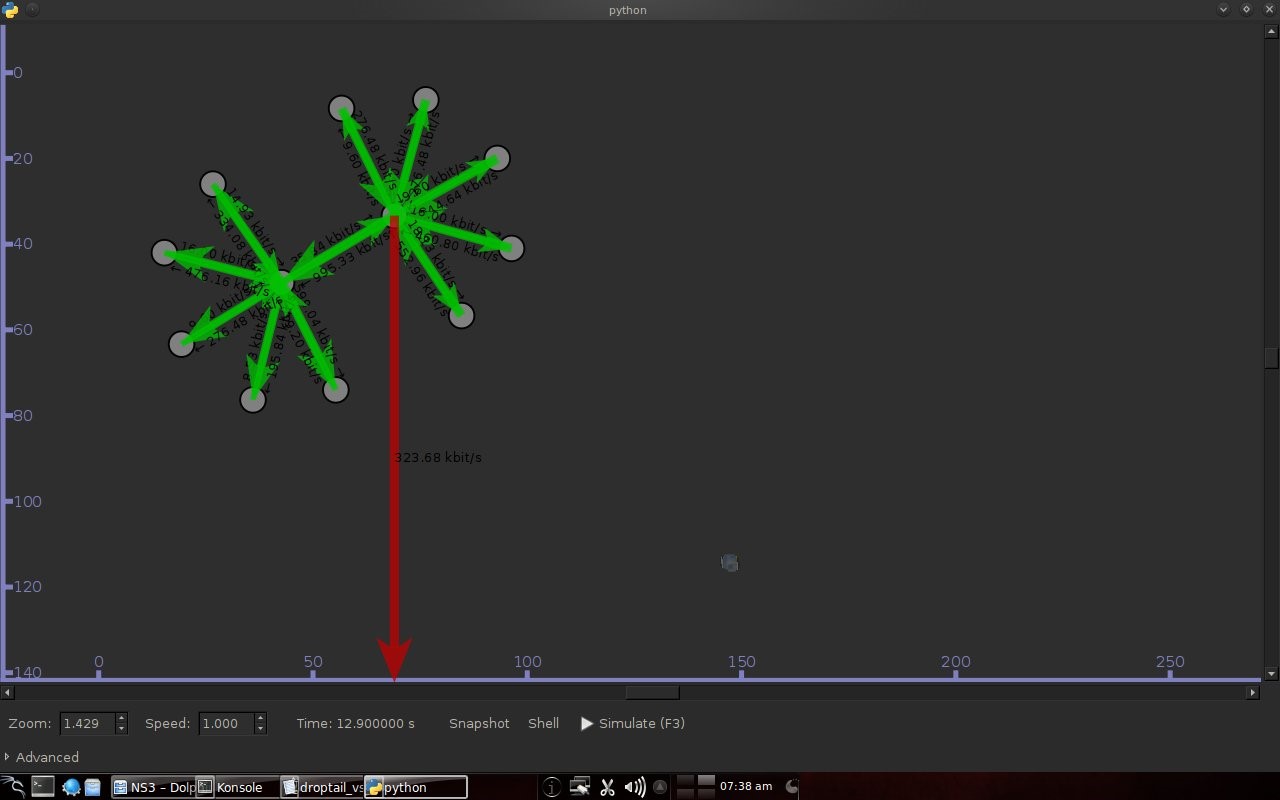
Network Simulator 3 dapat mensimulasikan REDQueue dan menampilkan animasi sehingga lebih mudah untuk diamati.
❮ ❯The use of Nagios in the Electrical Engineering Computer Lab of Udayana University
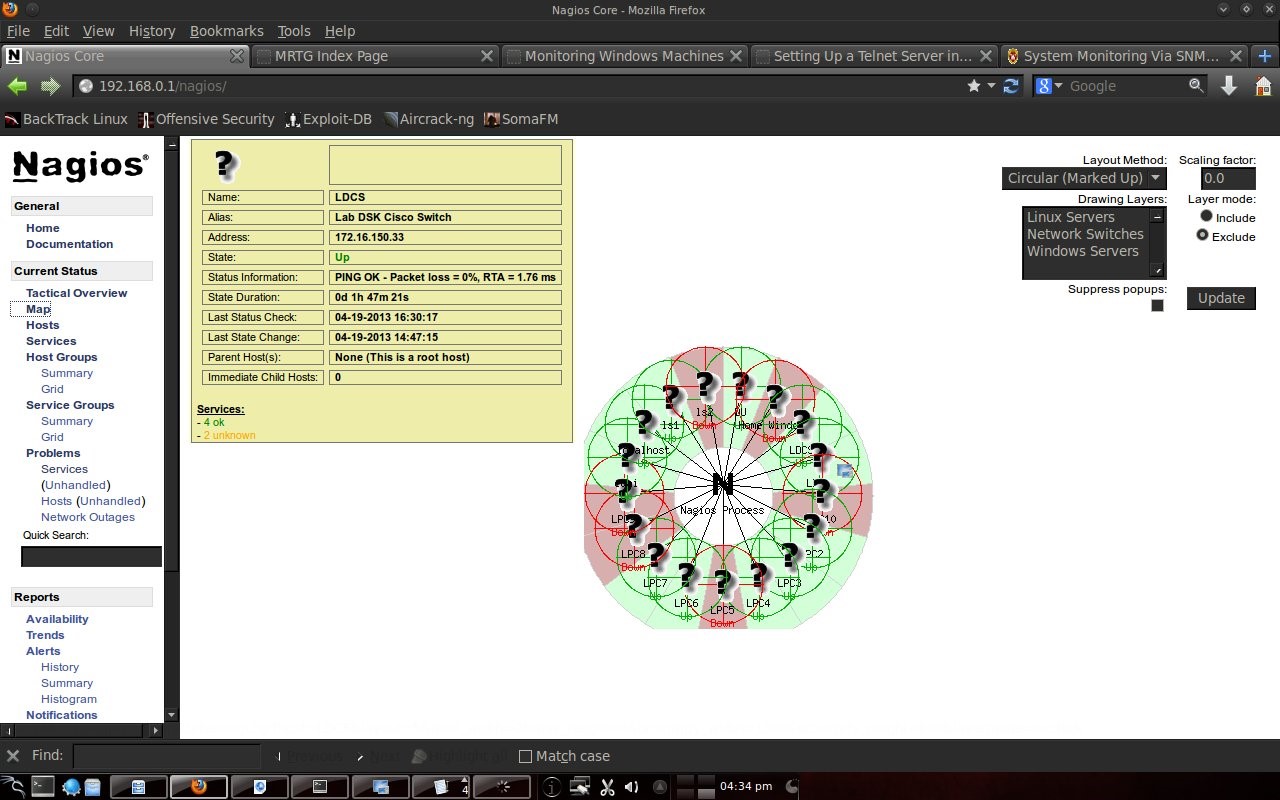
The assignment of my Telecommunication System Reliability course regarding Nagios application which can monitor the state computer network.
❮ ❯Observing DOTA Playing Performance with OPNET Simple LAN System
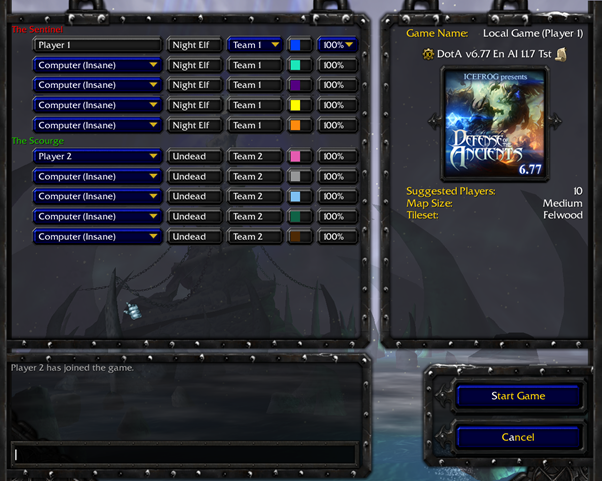
Telecommunication Network Course assignment about simulating playing DOTA 10 players on LAN using OPNET based on 1 player datarate from Wireshark.
❮ ❯Mengamati Perfoma Bermain DOTA dengan OPNET Sistem LAN Sederhana

Tugas mata kuliah jaringan telekomunikasi tentang simulasi bermain DOTA 10 pemain LAN di OPNET berdasarkan datarate 1 pemain dari Wireshark.
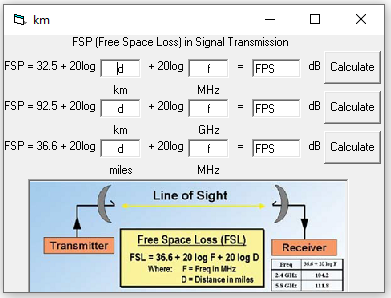
❮ ❯The Effect of FPS, Resolution and Bitrate Settings on the Resulting Throughput in the Adobe Flash Media Live Encoder Software
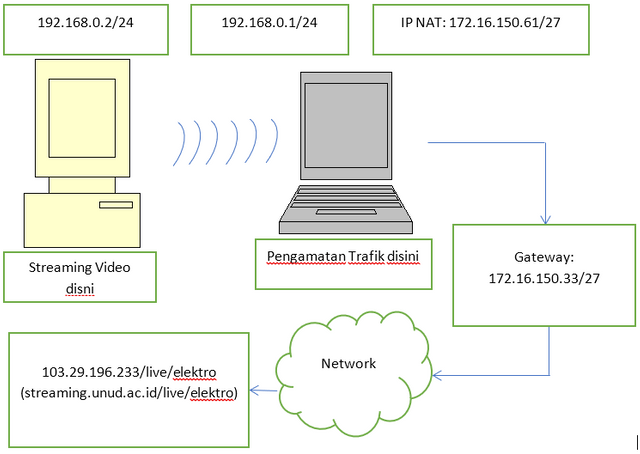
Research writing assignment regarding abstract, introduction, literature review, method, discussion, conclusion, and bibliography.
❮ ❯Pengaruh Pengaturan FPS, Resolusi dan Bitrate Terhadap Throughput Yang Dihasilkan pada Software Adobe Flash Media Live Encoder
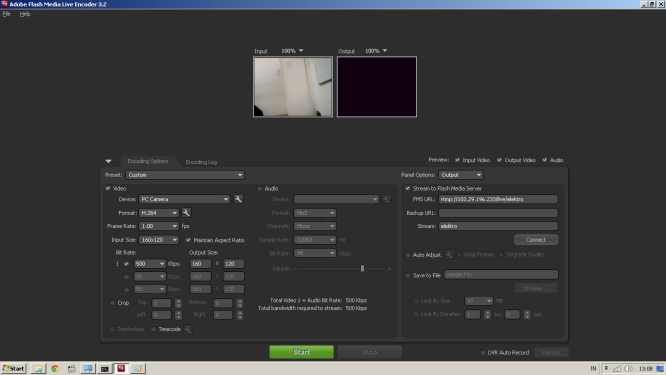
Tugas mata kuliah penulisan penelitian mengenai abstrak, pendahuluan, kajian pustaka, metode penelitian, pembahasan, penutup, dan daftar pustaka.
❮ ❯Image Transmission on Wireless Visual Sensor Networking Devices Imote2 Platform Based on IEEE 802.15.4 ZigBee Embedded Linux
My final project is to create a C program for image delivery on WSN Imote2 ZigBee and save image transmission cost with JPEG2000 using embedded Linux.
❮ ❯Transmisi Citra Pada Perangkat Jaringan Sensor Visual Nirkabel Platform Imote2 Berbasis IEEE 802.15.4 ZigBee Embedded Linux

Tugas akhir saya membuat program C pengiriman citra pada JSN Imote2 ZigBee dan penghematan transmisi citra dengan JPEG2000 menggunakan embedded Linux.
❮ ❯Menentukan Coverage Macro Cell Berdasarkan Okumura Hata Di Matlab
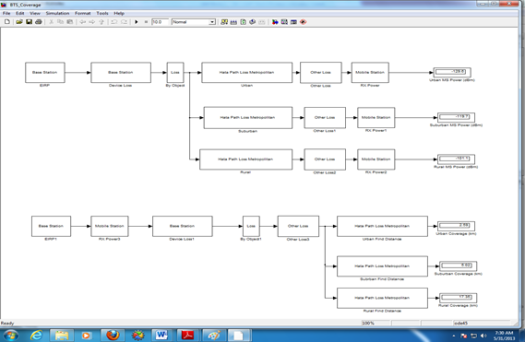
Menggunakan MATLAB jauh lebih cepat dari menghitung manual serta dapat membuat grafik dan menggambarkan illustrasi radius BS dengan MS.
❮ ❯Determining Macro Cell Coverage Based on Okumura Hata in Matlab
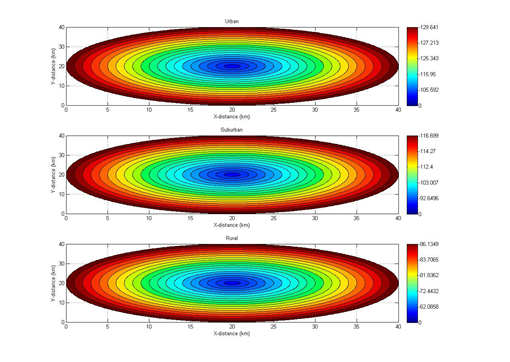
Using MATLAB is much faster than calculating manually and able to graph the base station radius with mobile station.
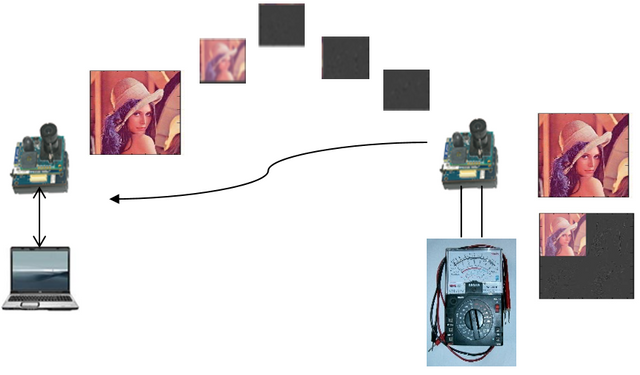
❮ ❯Simulation of ICT Network Configuration Based on Existing Network Configuration at the Network Operation Center of the Badung Regency Government
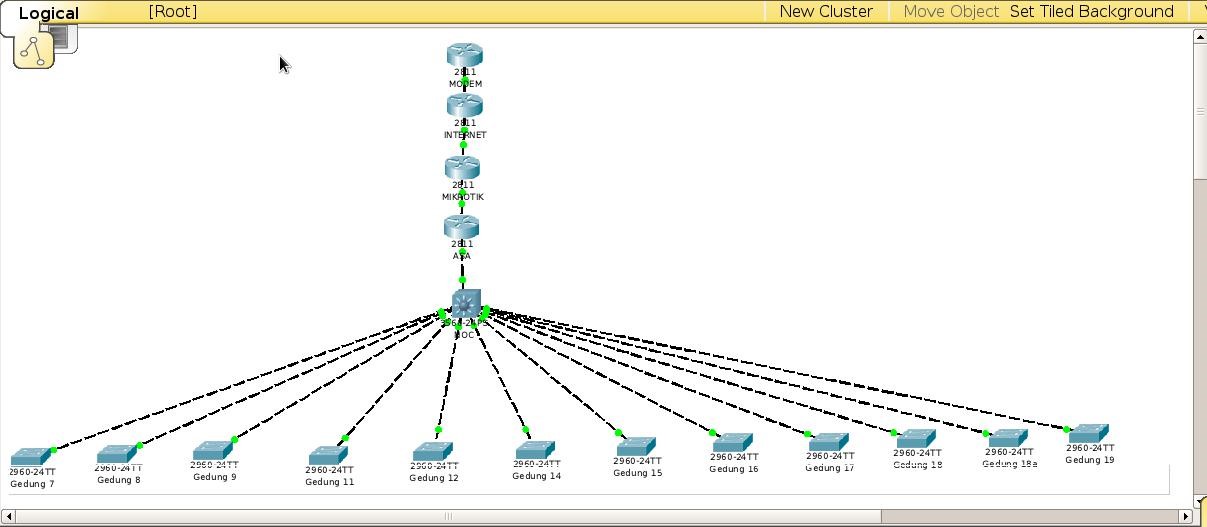
My practical work on Fiber Optic Installation Project in Badung Regency Government regarding computer network configuration on Cisco Devices
❮ ❯Penggunaan Nagios di Lab Komputer Teknik Elektro Universitas Udayana
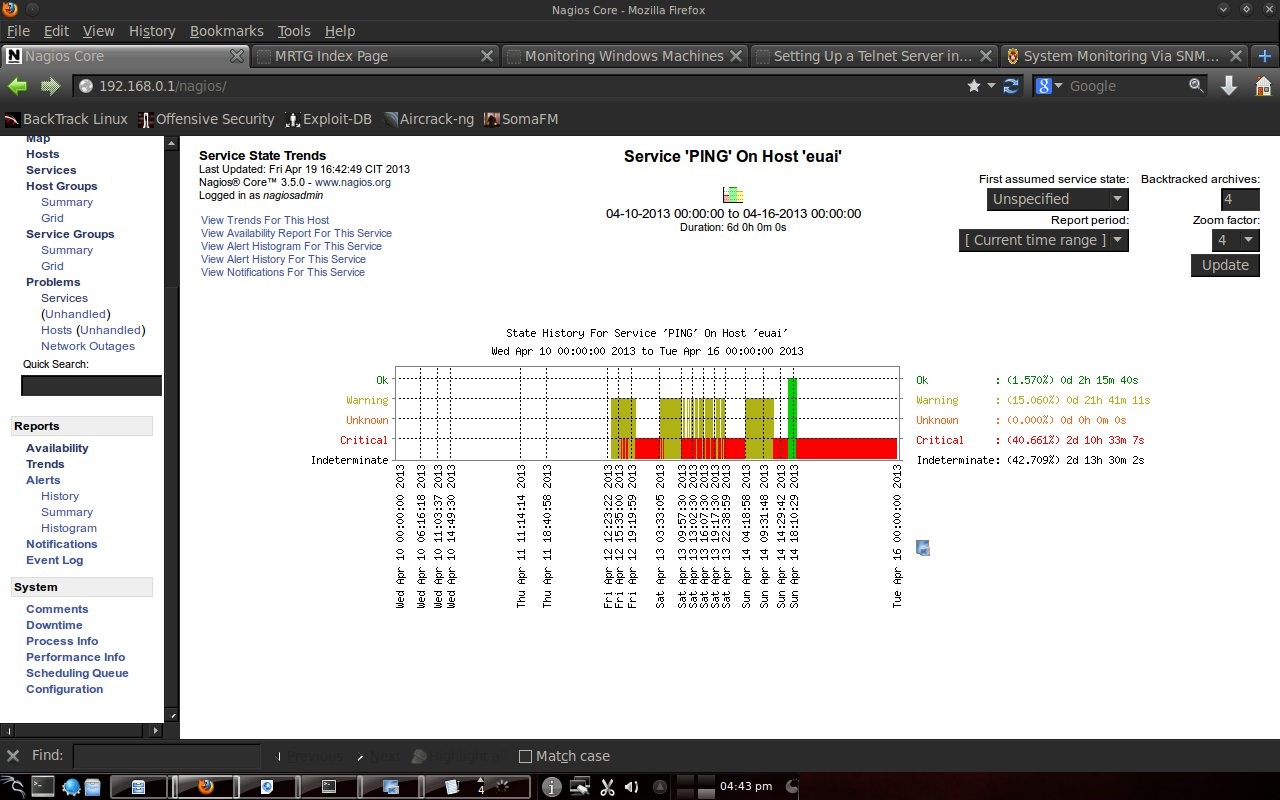
Tugas dari mata kuliah Kehandalan Sistem Telekomunikasi S1 saya mengenai aplikasi Nagios yang dapat memantau keadaan jaringan komputer.
❮ ❯Simulasi Konfigurasi Jaringan ICT Berbasis Konfigurasi Jaringan Eksisting di Network Operation Center Pemerintah Kabupaten Badung
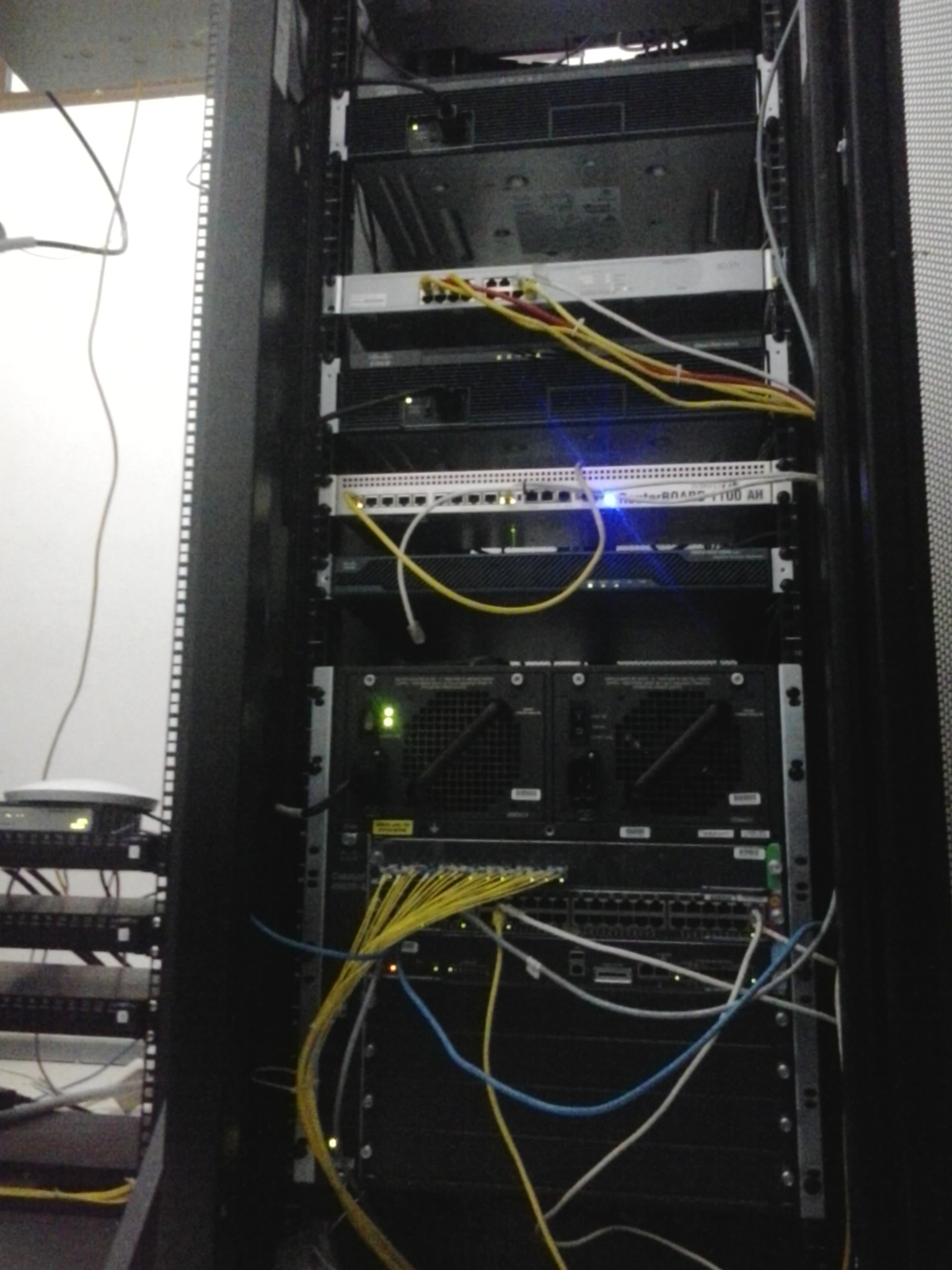
Kerja praktek saya pada Proyek Instalasi Fiber Optik di Kawasan Pusat Pemerintah Kabupaten Badung mengenai konfigurasi jaringan komputer.
❮ ❯Embedded Linux implementation on Imote2 Platform Wireless Sensor Networks

TinyOS users on the Imote2 platform encounter many limitations. Hence the community developed embedded Linux.
❮ ❯Implementasi Embedded Linux pada Jaringan Sensor Nirkabel Platform Imote2

Pengguna TinyOS pada platform Imote2 menemukan banyak keterbatasan. Oleh karena itu komunitas pengembangkan embedded Linux.
❮ ❯Kelayakan Perayaan Hari Bumi Di Indonesia Berdasarkan Hubungan Alamiah Dalam Pancasila

Walaupun Hari Bumi berasal dari luar teori Pancasila dengan Hari Bumi sejalan. Justru Hari Bumi menduku mendukung hubungan alamiah Pancasila
❮ ❯The Appropriateness of Celebrating Earth Day in Indonesia Based on Natural Relationships in Pancasila

Although Earth Day comes from outside, Pancasila is in line with Earth Day. In fact, Earth Day supports the natural relationship in Pancasila.
❮ ❯My Undergraduate English Assignment Collection

For natives this kind of assignment can be for elementary school students but for us is above high school since English is rarely used here.
❮ ❯Now a Blogger Handbook which used to be a Gumbrih Village Website Handbook during my community service program
In the end, this was shown for those who wanted to know and try blogging and to find out about the contribution of my Community Service Program in 2014 at Gumbrih.
❮ ❯Buku Panduan Blogger Dulu Saat KKN Adalah Buku Panduan Update Website Desa Gumbrih
Pada akhirnya ini ditunjukkan bagi yang ingin mengetahui dan mencoba blogging dan mengetahui kontribusi KKN saya pada tahun 2013 di Gumbrih.
❮ ❯Man in The Middle Demonstration with Arpspoof and Wireshark
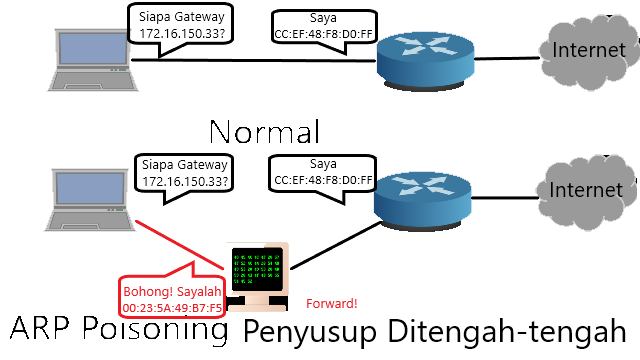
Actually it's just a man in the middle essay but I'm also interested in practicing it with Arpspoof and Wireshark on Linux.
❮ ❯Demonstrasi Penyusup Ditengah dengan Arpspoof dan Wireshark

Sebenarnya hanya essay man in the middle tetapi saya juga tertarik untuk mempraktikannya dengan Arpspoof dan Wireshark di Linux.
❮ ❯Our Essay on the Internet for Indonesians 2011

This assignment is structured for readers in 2011 can find out how big the role and influence of Internet technology is in everyday life.
❮ ❯Esai Kami Tentang Internet untuk Masyarakat Indonesia 2011

Tugas ini disusun agar pembaca pada 2011 dapat mengetahui seberapa besar peran dan pengaruh Teknologi Internet dalam kehidupan sehari-hari.
❮ ❯My Undergraduate Electrical Materials Assignment Collection
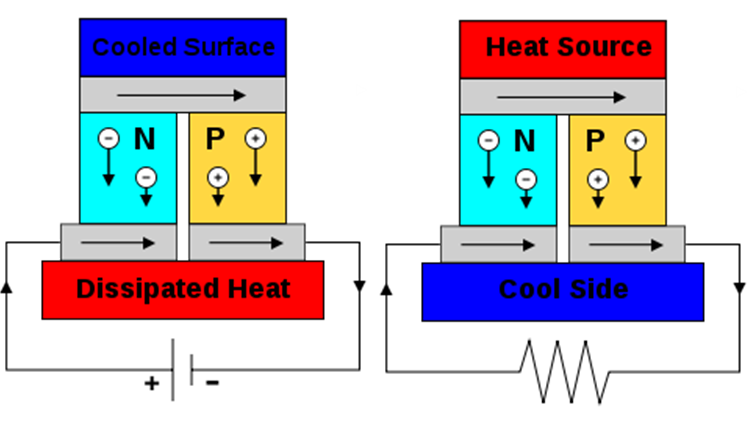
The tasks recorded electronically are electrical insulation and conductor and thermoelectric, others are handwritten and submitted.
❮ ❯Koleksi Tugas Bahan Listrik Sarjana Saya
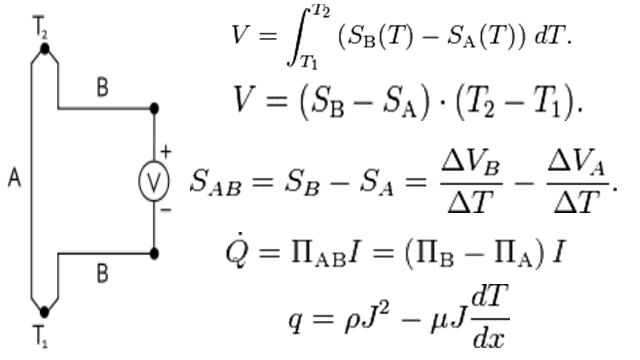
Tugas yang tercatat secara elektronik adalah isolasi dan pengantar listrik dan termoelektrik dimana yang lain ditulis tangan dan dikumpul.
❮ ❯Ampere Law and Magnetic Fields Class Assignment
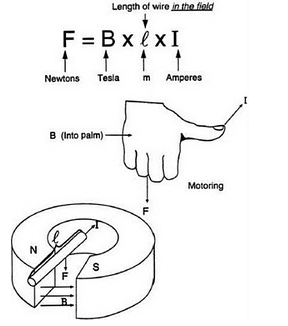
The course assignment in Electric Field Theory is writing essays on Ampere's Law, Biot-Savart Law, and other magnetic field laws.
❮ ❯Tugas Kuliah Hukum Ampere dan Medan Magnetik
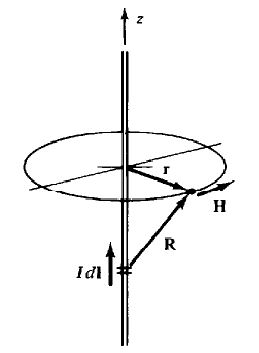
Tugas kuliah Teori Medan Listrik menulis essai mengenai Hukum Ampere, Hukum Biot-Savart, dan hukum medan magnetik lainnya.
❮ ❯My Opinion Regarding Hard Skills and Soft Skills when I was an Undergraduate Student

Most importantly, accept things regardless of background and status, always be prejudiced, and accept all differences.
❮ ❯Opini Saya Mengenai Keterampilan Keras dan Lunak saat Masih Mahasiswa

Yang paling penting, menerima sesuatu tanpa memandang latar belakang dan status, selalu berprasangka baik, dan menerima segala perbedaan.
❮ ❯Our 2011 Assignment Regarding Visual Basic 6
Older programmers will feel nostalgic and young programmers will be surprised how much Visual Basic was underdeveloped before.
❮ ❯Tugas Kuliah 2011 Kami Mengenai Visual Basic 6

Para programer tua akan merasa nostalgia dan para programer muda akan kaget mengenai bagaimana belum berkembangnya Visual Basic dulu.
❮ ❯My Period between College Graduation and Studying Abroad

In summary out of my mind applied to Valve and Blizzard, applied to many scholarships, and my first stressing employment in manufacturing.
❮ ❯My Essay about Google when I was an Undergraduate Student 2013
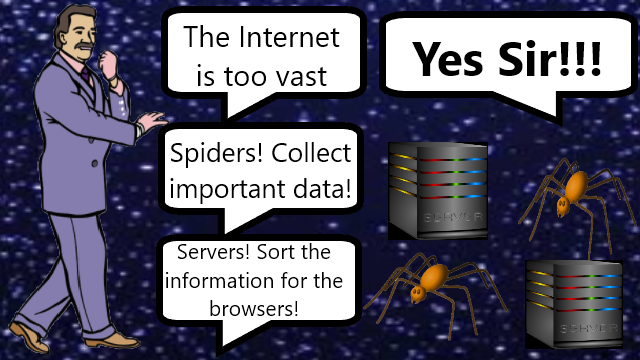
The Internet is vast and we need Google to navigate for us with its page ranking and crawler technology and this is my Google essay in 2013.
❮ ❯Finding Periods in Signal Equation Through Visualization
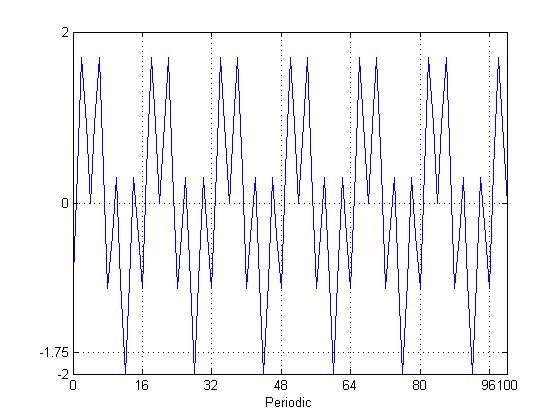
In Engineering we are encouraged not to waste time solving manually for example find periods in signal equations through visualization.
❮ ❯College Assignment About Oscilloscope

An oscilloscope is an electronic device that can display electrical signals and the wave equation of an electrical signal.
❮ ❯Tugas Kuliah Tentang Osiloskop
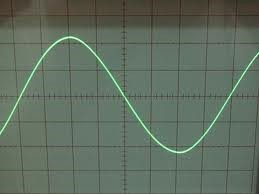
Osiloskop merupakan suatu peralatan elektronik yang dapat menampilkan sinyal listrik dan bentuk persamaan gelombang suatu sinyal listrik.
❮ ❯Megger or Mega Ohm Meter College Assignment
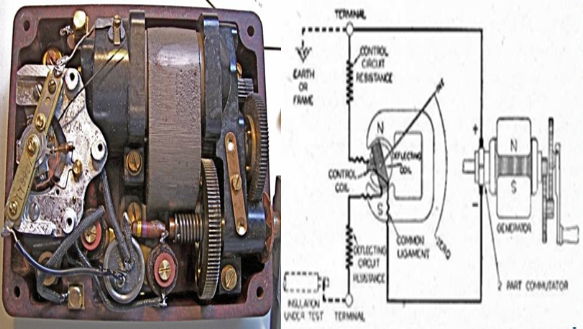
An electrician doing a Megger is an electrical insulation test also sometimes called a Megger Test. Megger has now grown into a big company.
❮ ❯Tugas Kuliah Megger atau Mega Ohm Meter

Seorang teknisi listrik melakukan Megger yang dimaksud adalah pengukuran atau pengujian isolasi listrik juga terkadang disebut Megger Test.
❮ ❯AVO Meter College Assignment
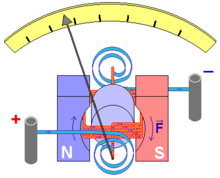
AVO meter is a combination of ampere meter, voltmeter, ohmmeter which have various functions, namely measuring current, voltage, resistance.
❮ ❯Tugas Kuliah AVO Meter
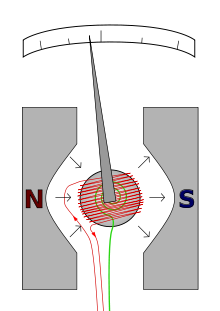
AVO meter adalah gabungan dari ampere meter, voltmeter, ohmmeter yang mempunyai fungsi bervariasi yaitu pengukuran arus, tegangan, hambatan.
❮ ❯Short Description of IPTV Assignment
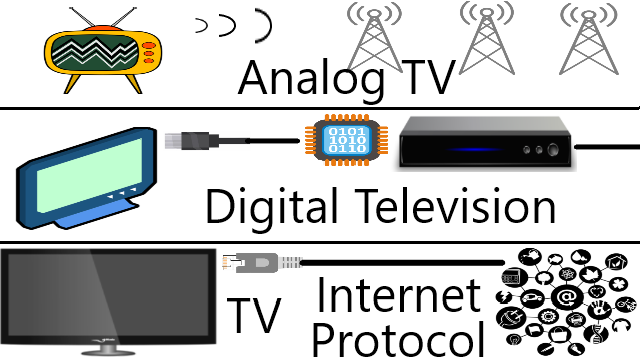
TV with live broadcasts either passes through electromagnetic waves that are captured by the antenna while IPTV through the Internet network.
❮ ❯Tugas Kuliah Deskripsi Singkat IPTV
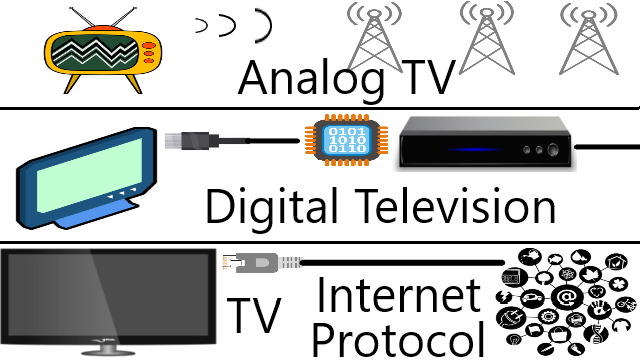
TV dengan siaran langsung baik melewati gelombang elektromagnetik yang ditangkap dengan atenna. Sedangkan IPTV melewati jaringan Internet.
❮ ❯My Undergraduate Electrical Power Engineering Assignment Collection
This task covers the supply of electricity (generation, transmission, distribution), basic electrical theories, transformer, and generators.
❮ ❯Koleksi Tugas Dasar Teknik Tenaga Listrik Sarjana Saya
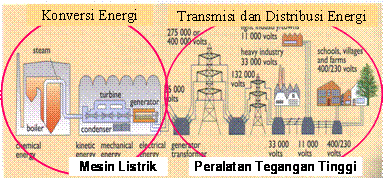
Tugas ini mencangkupi pengadaan listrik (pembangkit, transmisi, distribusi), teori dasar seperti hukum ohm trafo, dan generator arus searah.
❮ ❯My IELTS Speaking Script Decades Ago

This is my script for English speaking practice during my International English Language Testing System (IELTS) course few decades ago.
❮ ❯Brute Force Attack Demonstration with Hydra
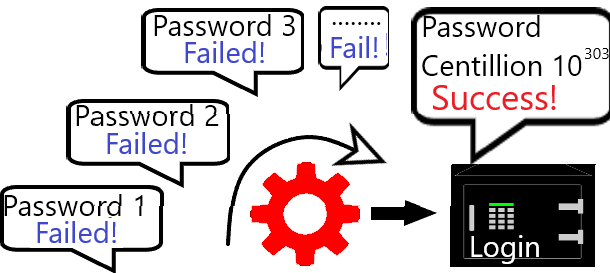
Actually it was just an assignment to write an essay but I happened to try Backtrack Linux at that time and just practiced it.
❮ ❯Demonstrasi Brute Force Attack dengan Hydra
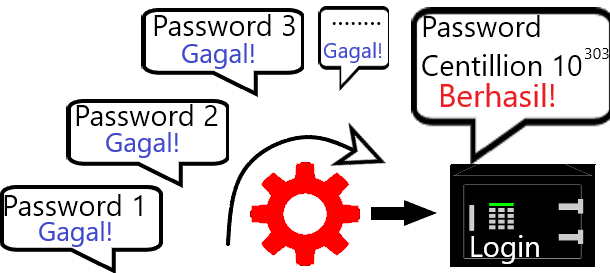
Sebenarnya hanya tugas untuk menulis esai tapi kebetulan saat itu saya mulai mencoba Backtrack Linux dan sekalian saja praktik.
❮ ❯academic
story
tradingsignals
My Technical Analysis on Forex Cross Pairs 2021
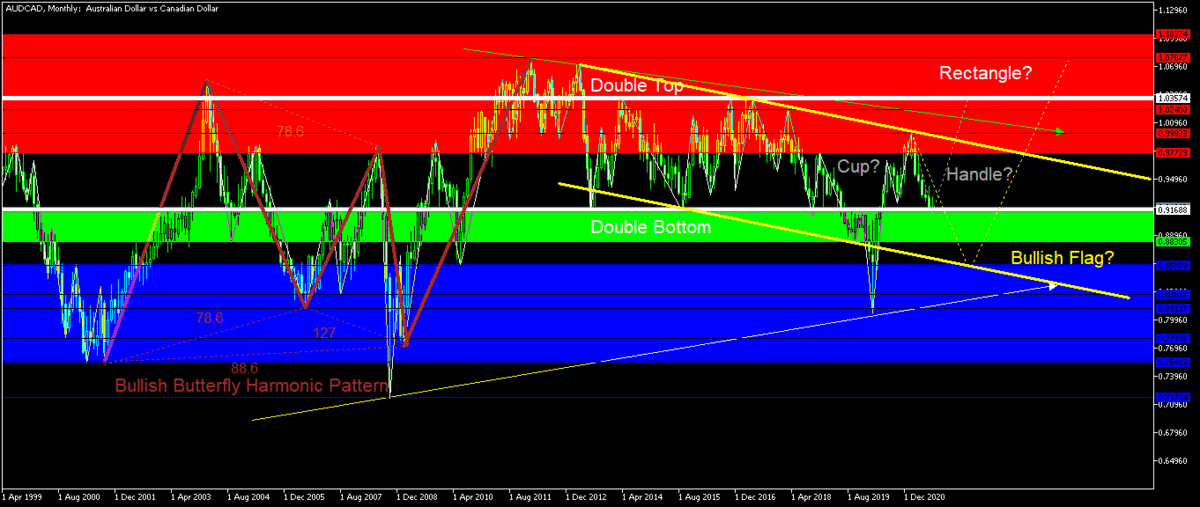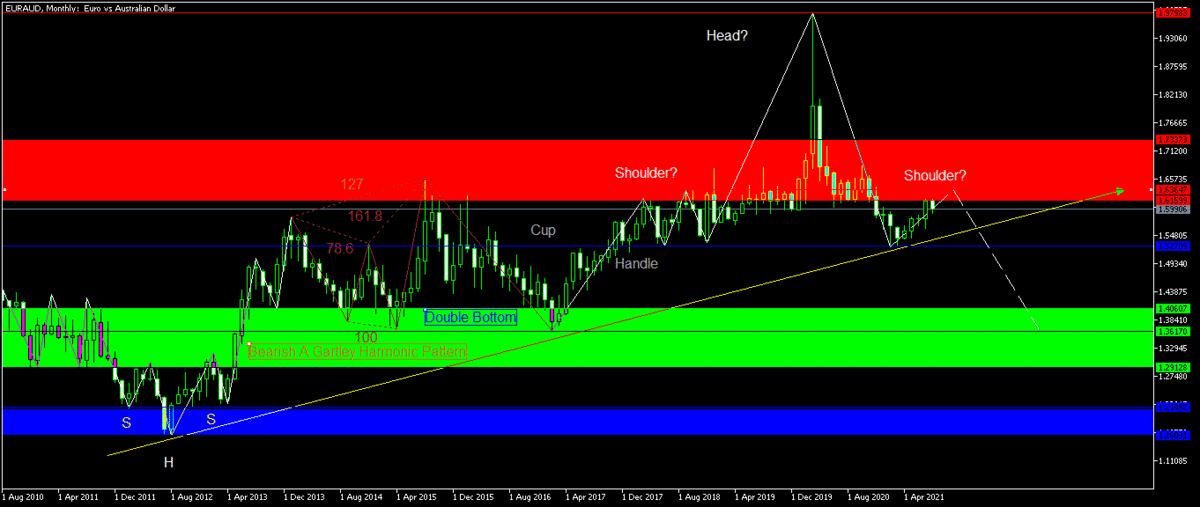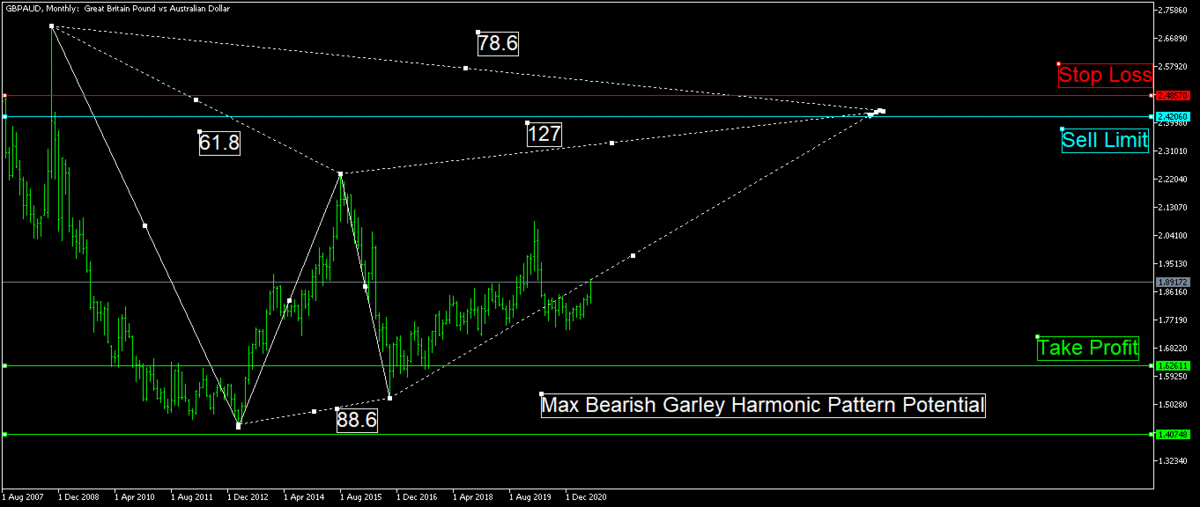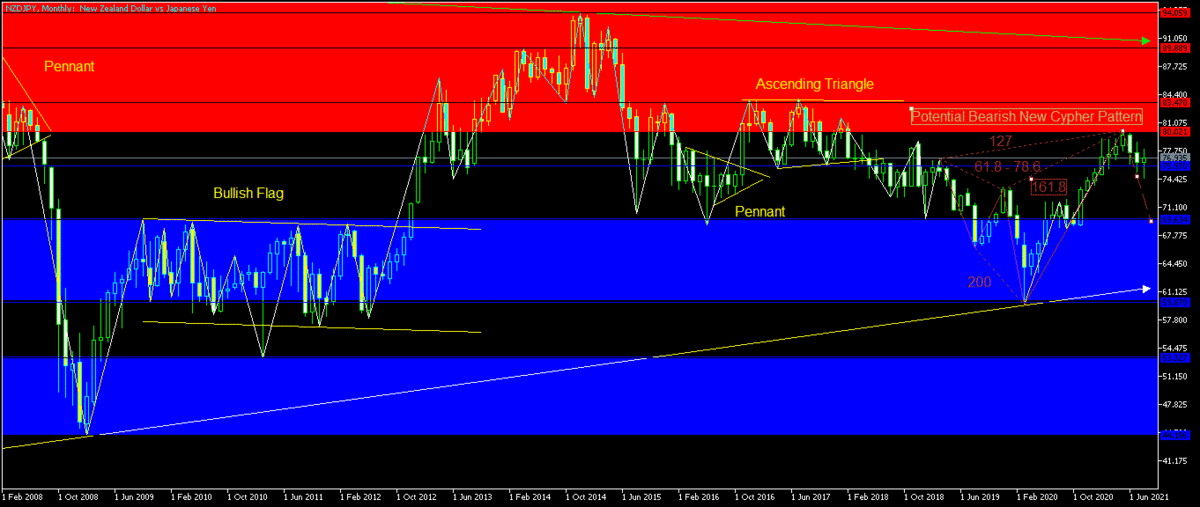
Cross pairs are really just cross pairing of the major and commodity pairs except for the United States (US) Dollar and these are only my TA.
❮ ❯My Technical Analysis on Forex Major and Commodity Pairs 2021
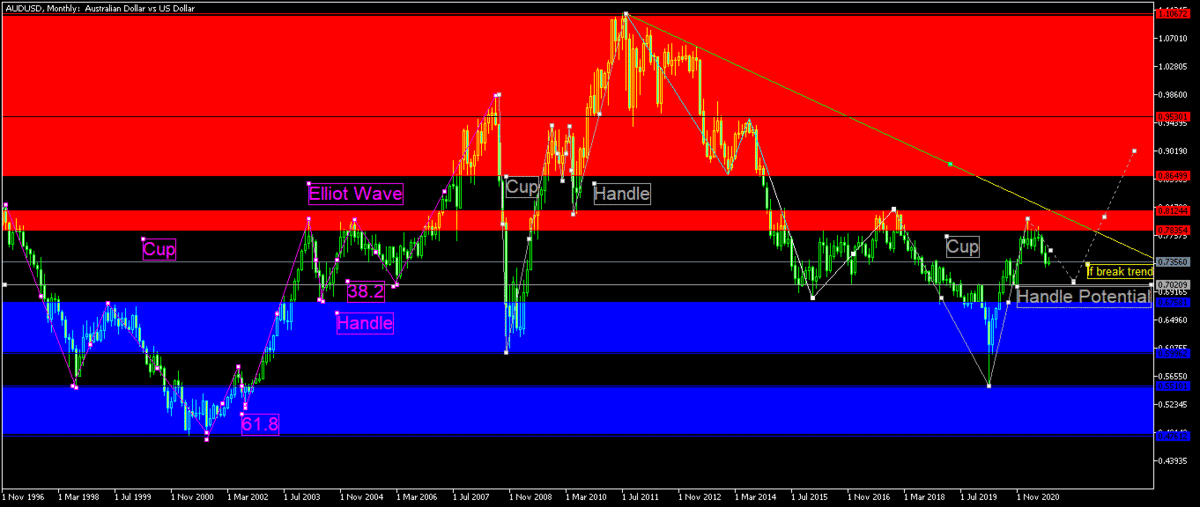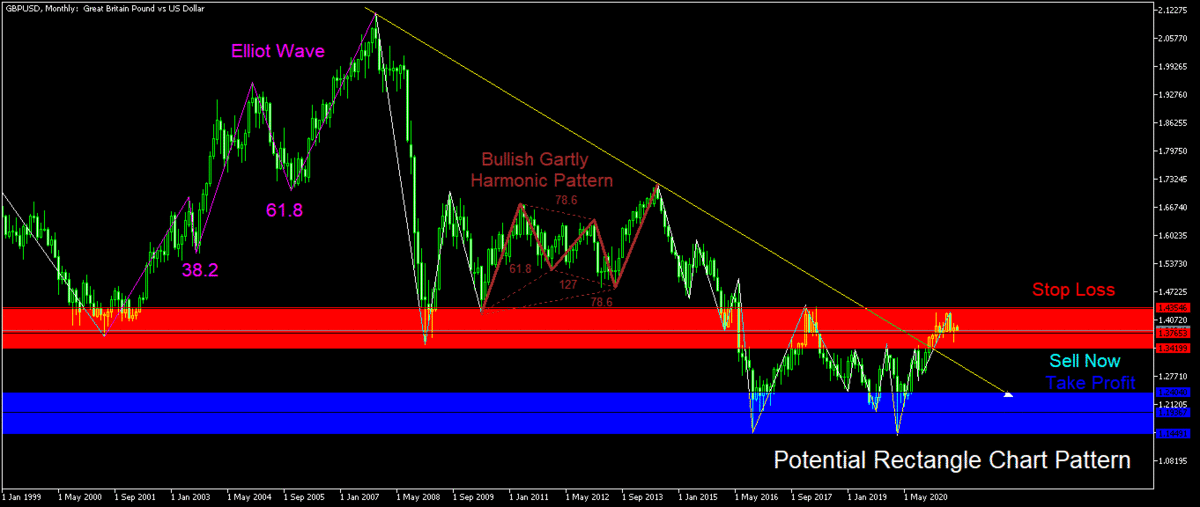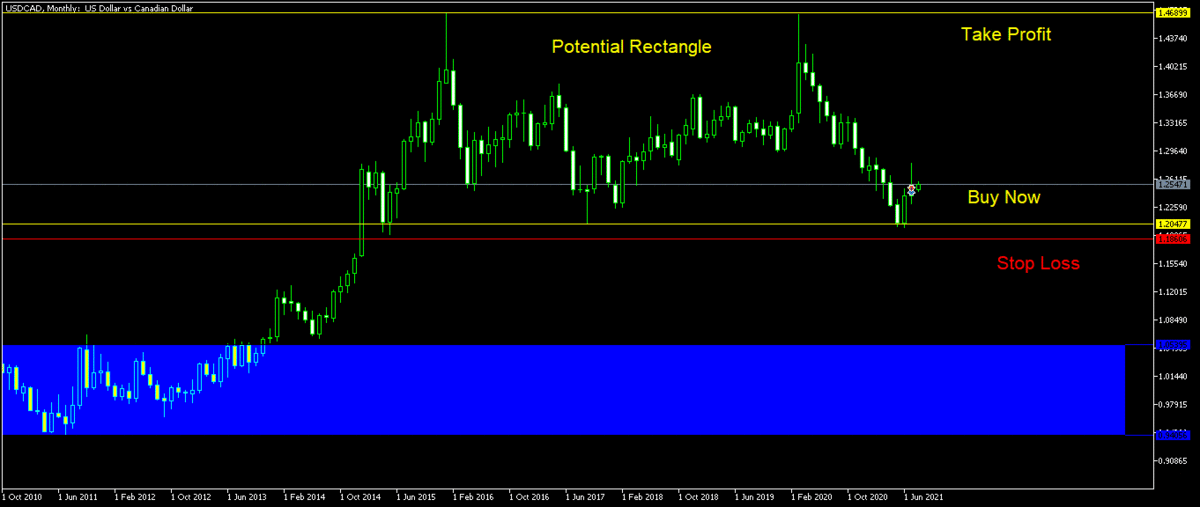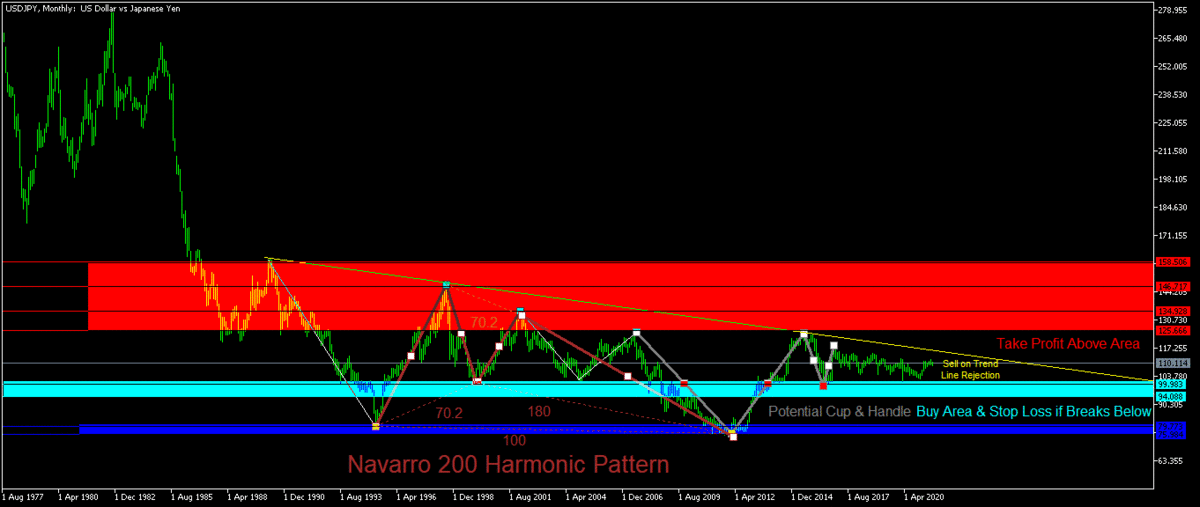
Trading signals for EURUSD, GBPUSD, USDJPY, USDCHF, USDCAD, AUDUSD, NZDUSD, all monthly charts which can be relevant until end of 2021.
❮ ❯